Last edited by a moderator:
Solved Post All Your Success Stories With Your EFT Dongle
- Thread starter Easy Team
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
This topic has been solved
Mirza Asim Pak
Friend's Martview
maanarman
Friend's Martview
Huawei Y5 2017 FRP Done
model MYA-L22
SW Maya-L22C185B125
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: MYA-L22
SW Maya-L22C185B125
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
model MYA-L22
SW Maya-L22C185B125
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: MYA-L22
SW Maya-L22C185B125
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
Huawei Y6II Frp Done By EFT
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: CAM-L21
SW: :CAM-L21C185B150
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: CAM-L21
SW: :CAM-L21C185B150
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
iOS_Shakil
Friend's Martview
iOS_Shakil
Friend's Martview
Y6II Frp Done By EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: CAM-L21
SW: :CAM-L21C185B161
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: CAM-L21
SW: :CAM-L21C185B161
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
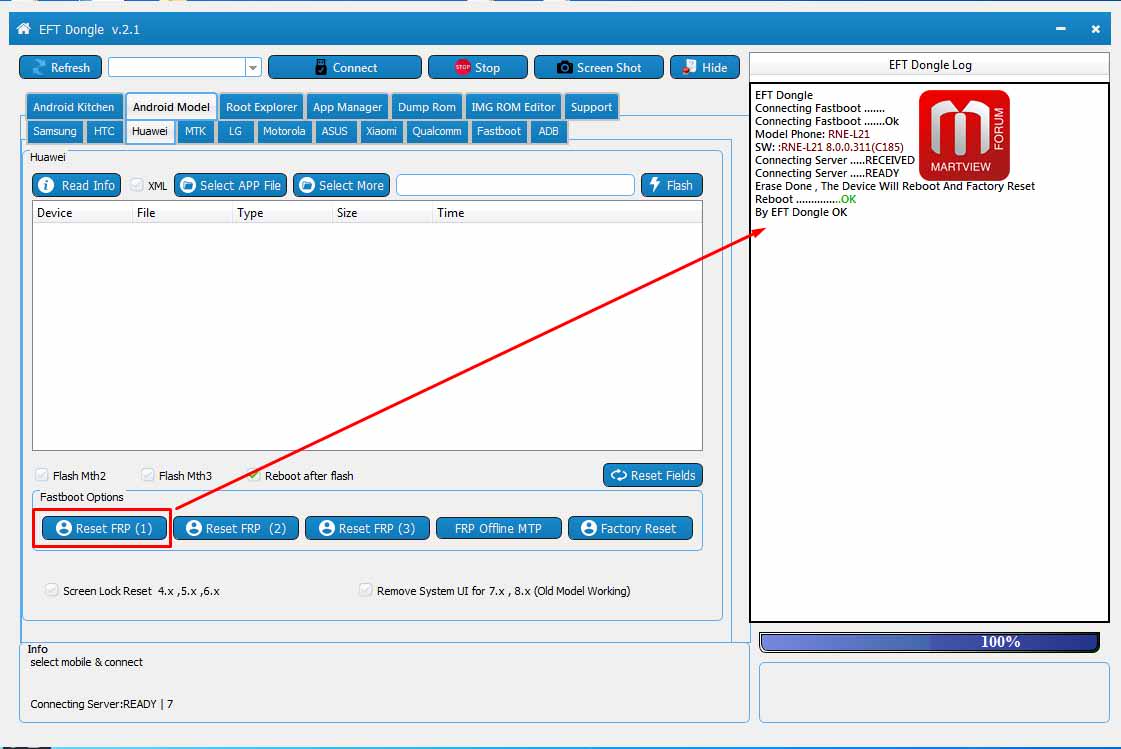
Huawei Mate 10 Lite RNE-L21 8.0.0 FRP Lock Reset Done
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: RNE-L21
SW: :RNE-L21 8.0.0.311(C185)
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
EFT Dongle
Connecting Fastboot .......
Connecting Fastboot .......Ok
Model Phone: RNE-L21
SW: :RNE-L21 8.0.0.311(C185)
Connecting Server .....RECEIVED
Connecting Server .....READY
Erase Done , The Device Will Reboot And Factory Reset
Reboot ...............OK
By EFT Dongle OK
cellbhai64
Member
- Dec 3, 2018
- 5
- 1
cellbhai64
Member
- Dec 3, 2018
- 5
- 1
cellbhai64
Member
- Dec 3, 2018
- 5
- 1
cellbhai64
Member
- Dec 3, 2018
- 5
- 1
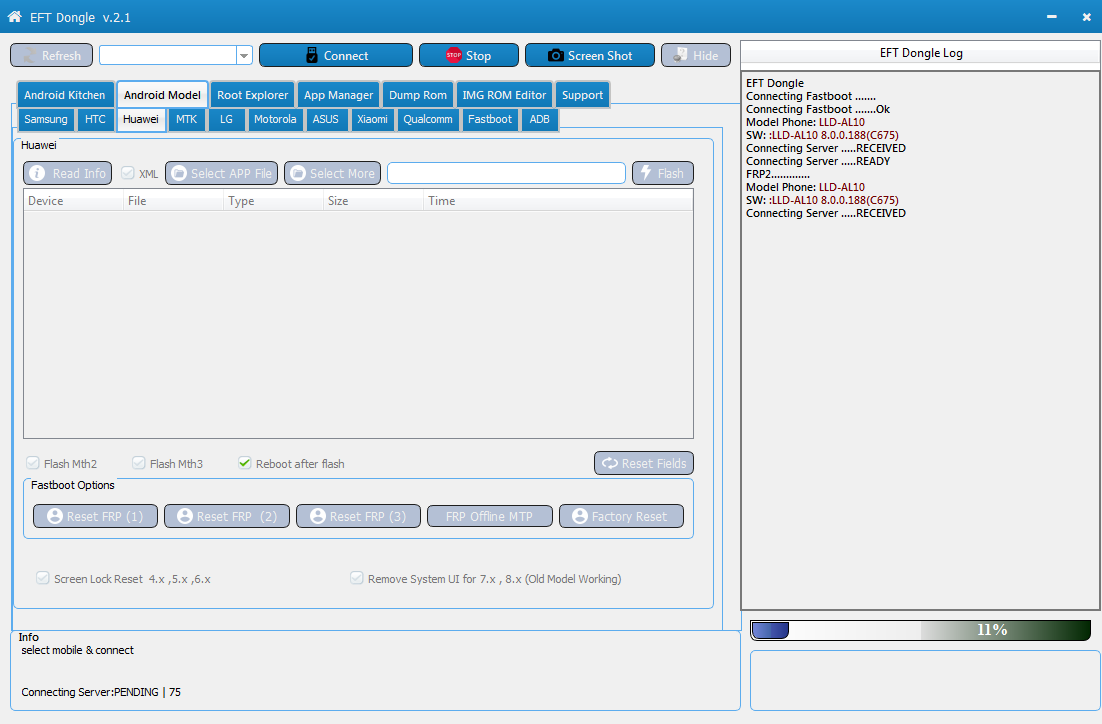
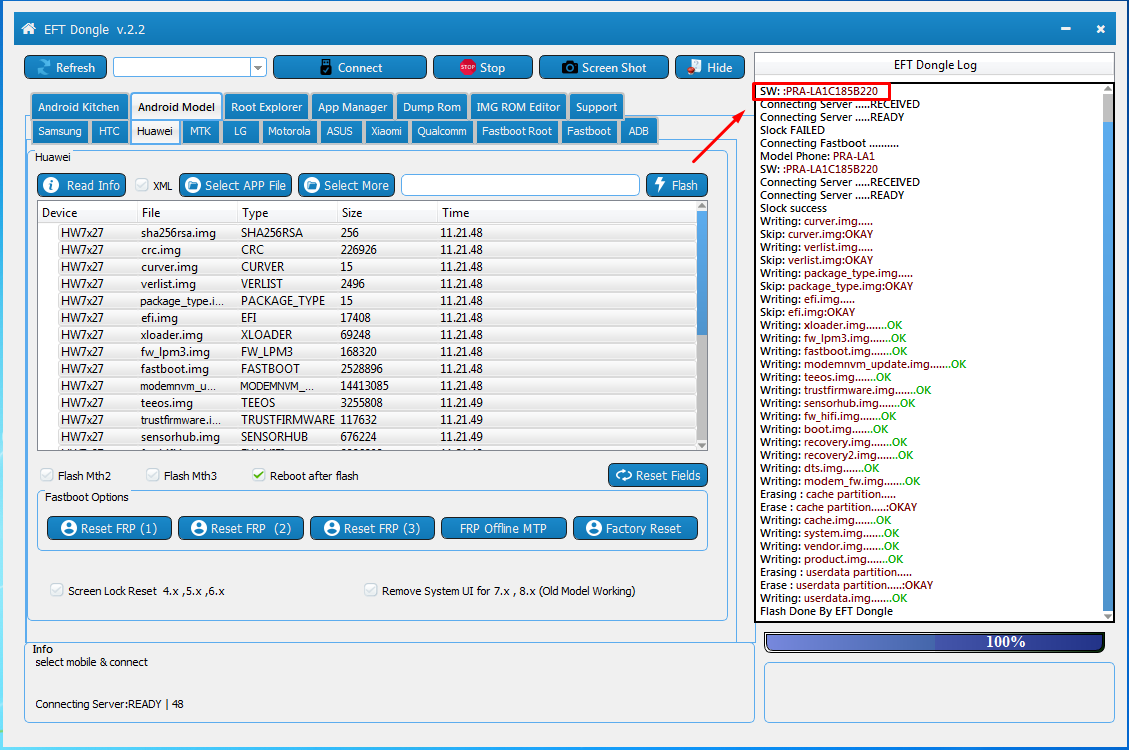
HUAWEI P8 lite 2017 PRA-LA1 Bricked Restart Only | Only Bootloader mode | Fastboot Mode only Done With EFT Dongle
Huawei PRA-LA1 Bricked phone repair guide with EFT Dongle
Huawei PRA-LA1 Bricked phone repair guide with EFT Dongle
Code:
Connecting Fastboot ..........
Model Phone: PRA-LA1
SW: :PRA-LA1C185B220
Connecting Server .....RECEIVED
Connecting Server .....READY
Slock FAILED
Connecting Fastboot ..........
Model Phone: PRA-LA1
SW: :PRA-LA1C185B220
Connecting Server .....RECEIVED
Connecting Server .....READY
Slock success
Writing: curver.img.....
Skip: curver.img:OKAY
Writing: verlist.img.....
Skip: verlist.img:OKAY
Writing: package_type.img.....
Skip: package_type.img:OKAY
Writing: efi.img.....
Skip: efi.img:OKAY
Writing: xloader.img.......OK
Writing: fw_lpm3.img.......OK
Writing: fastboot.img.......OK
Writing: modemnvm_update.img.......OK
Writing: teeos.img.......OK
Writing: trustfirmware.img.......OK
Writing: sensorhub.img.......OK
Writing: fw_hifi.img.......OK
Writing: boot.img.......OK
Writing: recovery.img.......OK
Writing: recovery2.img.......OK
Writing: dts.img.......OK
Writing: modem_fw.img.......OK
Erasing : cache partition.....
Erase : cache partition.....:OKAY
Writing: cache.img.......OK
Writing: system.img.......OK
Writing: vendor.img.......OK
Writing: product.img.......OK
Erasing : userdata partition.....
Erase : userdata partition.....:OKAY
Writing: userdata.img.......OK
Flash Done By EFT DongleDr.sunilsingh
Friend's Martview
Samsung J7 MAX SM-G615F Reset FRP Lock , ( Frp ON Oem On ) ONE CLICK With Eft Dongle
Device Model: Lenovo P1ma40 Factory Reset Done
Wating Device..........OK CPU: MT6735M
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 2.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 14.56 GB
Battery:
Battery Voltage: 3766
Injection..........OK
Detecting Parts info............OK
[ID: 1] [preloader] BaseAddr(0x00000000) Size(0x00400000)
[ID: 8] [pgpt] BaseAddr(0x00000000) Size(0x00080000)
[ID: 8] [proinfo] BaseAddr(0x00080000) Size(0x00300000)
[ID: 8] [nvram] BaseAddr(0x00380000) Size(0x00500000)
[ID: 8] [protect1] BaseAddr(0x00880000) Size(0x00a00000)
[ID: 8] [protect2] BaseAddr(0x01280000) Size(0x00a00000)
[ID: 8] [lk] BaseAddr(0x01c80000) Size(0x00080000)
[ID: 8] [para] BaseAddr(0x01d00000) Size(0x00080000)
[ID: 8] [boot] BaseAddr(0x01d80000) Size(0x01000000)
[ID: 8] [recovery] BaseAddr(0x02d80000) Size(0x01000000)
[ID: 8] [logo] BaseAddr(0x03d80000) Size(0x00800000)
[ID: 8] [expdb] BaseAddr(0x04580000) Size(0x00a00000)
[ID: 8] [seccfg] BaseAddr(0x04f80000) Size(0x00080000)
[ID: 8] [oemkeystore] BaseAddr(0x05000000) Size(0x00200000)
[ID: 8] [secro] BaseAddr(0x05200000) Size(0x00600000)
[ID: 8] [keystore] BaseAddr(0x05800000) Size(0x00800000)
[ID: 8] [tee1] BaseAddr(0x06000000) Size(0x00500000)
[ID: 8] [tee2] BaseAddr(0x06500000) Size(0x00500000)
[ID: 8] [frp] BaseAddr(0x06a00000) Size(0x00100000)
[ID: 8] [nvdata] BaseAddr(0x06b00000) Size(0x02000000)
[ID: 8] [metadata] BaseAddr(0x08b00000) Size(0x02500000)
[ID: 8] [system] BaseAddr(0x0b000000) Size(0xa0000000)
[ID: 8] [cache] BaseAddr(0xab000000) Size(0x1a800000)
[ID: 8] [userdata] BaseAddr(0xc5800000) Size(0x2dd580000)
[ID: 8] [flashinfo] BaseAddr(0x3a2d80000) Size(0x01000000)
[ID: 8] [sgpt] BaseAddr(0x3a3d80000) Size(0x00080000)
Detecting Device info.......OK
Product: LENOVO
Device Model: Lenovo P1ma40
ID: P1ma40_S027_151127_16G_ROW
Sw Internal: P1ma40_USR_S027_1511271830_MP3V2_16G_ROW_US
Build Date: Fri Nov 27 17:14:52 CST 2015
Chip Ver: S01
Android Version: 5.1
Architecture: arm64-v8a
Formating... [USERDATA] .....OK
All Done By EFT Dongle
thx to orignal poster
Wating Device..........OK CPU: MT6735M
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 2.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 14.56 GB
Battery:
Battery Voltage: 3766
Injection..........OK
Detecting Parts info............OK
[ID: 1] [preloader] BaseAddr(0x00000000) Size(0x00400000)
[ID: 8] [pgpt] BaseAddr(0x00000000) Size(0x00080000)
[ID: 8] [proinfo] BaseAddr(0x00080000) Size(0x00300000)
[ID: 8] [nvram] BaseAddr(0x00380000) Size(0x00500000)
[ID: 8] [protect1] BaseAddr(0x00880000) Size(0x00a00000)
[ID: 8] [protect2] BaseAddr(0x01280000) Size(0x00a00000)
[ID: 8] [lk] BaseAddr(0x01c80000) Size(0x00080000)
[ID: 8] [para] BaseAddr(0x01d00000) Size(0x00080000)
[ID: 8] [boot] BaseAddr(0x01d80000) Size(0x01000000)
[ID: 8] [recovery] BaseAddr(0x02d80000) Size(0x01000000)
[ID: 8] [logo] BaseAddr(0x03d80000) Size(0x00800000)
[ID: 8] [expdb] BaseAddr(0x04580000) Size(0x00a00000)
[ID: 8] [seccfg] BaseAddr(0x04f80000) Size(0x00080000)
[ID: 8] [oemkeystore] BaseAddr(0x05000000) Size(0x00200000)
[ID: 8] [secro] BaseAddr(0x05200000) Size(0x00600000)
[ID: 8] [keystore] BaseAddr(0x05800000) Size(0x00800000)
[ID: 8] [tee1] BaseAddr(0x06000000) Size(0x00500000)
[ID: 8] [tee2] BaseAddr(0x06500000) Size(0x00500000)
[ID: 8] [frp] BaseAddr(0x06a00000) Size(0x00100000)
[ID: 8] [nvdata] BaseAddr(0x06b00000) Size(0x02000000)
[ID: 8] [metadata] BaseAddr(0x08b00000) Size(0x02500000)
[ID: 8] [system] BaseAddr(0x0b000000) Size(0xa0000000)
[ID: 8] [cache] BaseAddr(0xab000000) Size(0x1a800000)
[ID: 8] [userdata] BaseAddr(0xc5800000) Size(0x2dd580000)
[ID: 8] [flashinfo] BaseAddr(0x3a2d80000) Size(0x01000000)
[ID: 8] [sgpt] BaseAddr(0x3a3d80000) Size(0x00080000)
Detecting Device info.......OK
Product: LENOVO
Device Model: Lenovo P1ma40
ID: P1ma40_S027_151127_16G_ROW
Sw Internal: P1ma40_USR_S027_1511271830_MP3V2_16G_ROW_US
Build Date: Fri Nov 27 17:14:52 CST 2015
Chip Ver: S01
Android Version: 5.1
Architecture: arm64-v8a
Formating... [USERDATA] .....OK
All Done By EFT Dongle
thx to orignal poster
Wating Device..........OK
CPU: MT6572
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 512.00 MB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 3.64 GB
Battery:
Battery Voltage: 3946
Injection..........OK
[PRELOADER] BaseAddr(0x00000000) Size(0x01000000)
[MBR] BaseAddr(0x01000000) Size(0x00080000)
[EBR1] BaseAddr(0x01080000) Size(0x00080000)
[PRO_INFO] BaseAddr(0x01100000) Size(0x00300000)
[NVRAM] BaseAddr(0x01400000) Size(0x00500000)
[PROTECT_F] BaseAddr(0x01900000) Size(0x00a00000)
[PROTECT_S] BaseAddr(0x02300000) Size(0x00a00000)
[SECCFG] BaseAddr(0x02d00000) Size(0x00020000)
[UBOOT] BaseAddr(0x02d20000) Size(0x00060000)
[BOOTIMG] BaseAddr(0x02d80000) Size(0x00600000)
[RECOVERY] BaseAddr(0x03380000) Size(0x00600000)
[SEC_RO] BaseAddr(0x03980000) Size(0x00800000)
[MISC] BaseAddr(0x04180000) Size(0x00080000)
[FRP] BaseAddr(0x04200000) Size(0x00100000)
[LOGO] BaseAddr(0x04300000) Size(0x00300000)
[EBR2] BaseAddr(0x04600000) Size(0x00080000)
[MOBILE_INFO] BaseAddr(0x04680000) Size(0x00800000)
[EXPDB] BaseAddr(0x04e80000) Size(0x00a00000)
[ANDROID] BaseAddr(0x05880000) Size(0x54000000)
[CACHE] BaseAddr(0x59880000) Size(0x08000000)
[USRDATA] BaseAddr(0x61880000) Size(0x84380000)
[OTP] BaseAddr(0xe5c00000) Size(0x02b00000)
[BMTPOOL] BaseAddr(0xe8700000) Size(0x01500000)
Reading: ...
Reading: CACHE [Size:128.00 MB] .....OK
Reading: USERDATA [Size:2.07 GB] .....OK
Reading: PRELOADER [Size:16.00 MB] .....OK
Reading: MBR [Size:512.00 KB] .....OK
Reading: EBR1 [Size:512.00 KB] .....OK
Reading: PRO_INFO [Size:3.00 MB] .....OK
Reading: NVRAM [Size:5.00 MB] .....OK
Reading: PROTECT_F [Size:10.00 MB] .....OK
Reading: PROTECT_S [Size:10.00 MB] .....OK
Reading: SECCFG [Size:128.00 KB] .....OK
Reading: UBOOT [Size:384.00 KB] .....OK
Reading: BOOTIMG [Size:6.00 MB] .....OK
Reading: RECOVERY [Size:6.00 MB] .....OK
Reading: SEC_RO [Size:8.00 MB] .....OK
Reading: MISC [Size:512.00 KB] .....OK
Reading: FRP [Size:1.00 MB] .....OK
Reading: LOGO [Size:3.00 MB] .....OK
Reading: EBR2 [Size:512.00 KB] .....OK
Reading: MOBILE_INFO [Size:8.00 MB] .....OK
Reading: EXPDB [Size:10.00 MB] .....OK
Reading: ANDROID [Size:1.31 GB] .....OK
Reading: OTP [Size:43.00 MB] .....OK
ROM info.......OK
Product:
Device Model:
ID:
Sw Internal:
Build Date:
Chip Ver:
Android Version:
Architecture:
Read Flash (Dump) Done By EFT Dongle
thx to orignl poster
@yisuscellca
CPU: MT6572
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 512.00 MB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 3.64 GB
Battery:
Battery Voltage: 3946
Injection..........OK
[PRELOADER] BaseAddr(0x00000000) Size(0x01000000)
[MBR] BaseAddr(0x01000000) Size(0x00080000)
[EBR1] BaseAddr(0x01080000) Size(0x00080000)
[PRO_INFO] BaseAddr(0x01100000) Size(0x00300000)
[NVRAM] BaseAddr(0x01400000) Size(0x00500000)
[PROTECT_F] BaseAddr(0x01900000) Size(0x00a00000)
[PROTECT_S] BaseAddr(0x02300000) Size(0x00a00000)
[SECCFG] BaseAddr(0x02d00000) Size(0x00020000)
[UBOOT] BaseAddr(0x02d20000) Size(0x00060000)
[BOOTIMG] BaseAddr(0x02d80000) Size(0x00600000)
[RECOVERY] BaseAddr(0x03380000) Size(0x00600000)
[SEC_RO] BaseAddr(0x03980000) Size(0x00800000)
[MISC] BaseAddr(0x04180000) Size(0x00080000)
[FRP] BaseAddr(0x04200000) Size(0x00100000)
[LOGO] BaseAddr(0x04300000) Size(0x00300000)
[EBR2] BaseAddr(0x04600000) Size(0x00080000)
[MOBILE_INFO] BaseAddr(0x04680000) Size(0x00800000)
[EXPDB] BaseAddr(0x04e80000) Size(0x00a00000)
[ANDROID] BaseAddr(0x05880000) Size(0x54000000)
[CACHE] BaseAddr(0x59880000) Size(0x08000000)
[USRDATA] BaseAddr(0x61880000) Size(0x84380000)
[OTP] BaseAddr(0xe5c00000) Size(0x02b00000)
[BMTPOOL] BaseAddr(0xe8700000) Size(0x01500000)
Reading: ...
Reading: CACHE [Size:128.00 MB] .....OK
Reading: USERDATA [Size:2.07 GB] .....OK
Reading: PRELOADER [Size:16.00 MB] .....OK
Reading: MBR [Size:512.00 KB] .....OK
Reading: EBR1 [Size:512.00 KB] .....OK
Reading: PRO_INFO [Size:3.00 MB] .....OK
Reading: NVRAM [Size:5.00 MB] .....OK
Reading: PROTECT_F [Size:10.00 MB] .....OK
Reading: PROTECT_S [Size:10.00 MB] .....OK
Reading: SECCFG [Size:128.00 KB] .....OK
Reading: UBOOT [Size:384.00 KB] .....OK
Reading: BOOTIMG [Size:6.00 MB] .....OK
Reading: RECOVERY [Size:6.00 MB] .....OK
Reading: SEC_RO [Size:8.00 MB] .....OK
Reading: MISC [Size:512.00 KB] .....OK
Reading: FRP [Size:1.00 MB] .....OK
Reading: LOGO [Size:3.00 MB] .....OK
Reading: EBR2 [Size:512.00 KB] .....OK
Reading: MOBILE_INFO [Size:8.00 MB] .....OK
Reading: EXPDB [Size:10.00 MB] .....OK
Reading: ANDROID [Size:1.31 GB] .....OK
Reading: OTP [Size:43.00 MB] .....OK
ROM info.......OK
Product:
Device Model:
ID:
Sw Internal:
Build Date:
Chip Ver:
Android Version:
Architecture:
Read Flash (Dump) Done By EFT Dongle
thx to orignl poster
@yisuscellca
Wating Device..........OK
CPU: MT6572
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 512.00 MB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 3.64 GB
Battery:
Battery Voltage: 3938
Injection..........OK
[PRELOADER] BaseAddr(0x00000000) Size(0x00c00000)
[MBR] BaseAddr(0x00c00000) Size(0x00080000)
[EBR1] BaseAddr(0x00c80000) Size(0x00080000)
[PRO_INFO] BaseAddr(0x00d00000) Size(0x00300000)
[NVRAM] BaseAddr(0x01000000) Size(0x00500000)
[PROTECT_F] BaseAddr(0x01500000) Size(0x00a00000)
[PROTECT_S] BaseAddr(0x01f00000) Size(0x00a00000)
[SECCFG] BaseAddr(0x02900000) Size(0x00020000)
[UBOOT] BaseAddr(0x02920000) Size(0x00060000)
[BOOTIMG] BaseAddr(0x02980000) Size(0x00600000)
[RECOVERY] BaseAddr(0x02f80000) Size(0x00600000)
[SEC_RO] BaseAddr(0x03580000) Size(0x00040000)
[MISC] BaseAddr(0x035c0000) Size(0x00080000)
[LOGO] BaseAddr(0x03640000) Size(0x00300000)
[EXPDB] BaseAddr(0x03940000) Size(0x00a00000)
[ANDROID] BaseAddr(0x04340000) Size(0x32000000)
[CACHE] BaseAddr(0x36340000) Size(0x0e200000)
[USRDATA] BaseAddr(0x44540000) Size(0xa41c0000)
[BMTPOOL] BaseAddr(0xe8700000) Size(0x01500000)
Reading: ...
Reading: CACHE [Size:226.00 MB] .....OK
Reading: USERDATA [Size:2.56 GB] .....OK
Reading: PRELOADER [Size:12.00 MB] .....OK
Reading: MBR [Size:512.00 KB] .....OK
Reading: EBR1 [Size:512.00 KB] .....OK
Reading: PRO_INFO [Size:3.00 MB] .....OK
Reading: NVRAM [Size:5.00 MB] .....OK
Reading: PROTECT_F [Size:10.00 MB] .....OK
Reading: PROTECT_S [Size:10.00 MB] .....OK
Reading: SECCFG [Size:128.00 KB] .....OK
Reading: UBOOT [Size:384.00 KB] .....OK
Reading: BOOTIMG [Size:6.00 MB] .....OK
Reading: RECOVERY [Size:6.00 MB] .....OK
Reading: SEC_RO [Size:256.00 KB] .....OK
Reading: MISC [Size:512.00 KB] .....OK
Reading: LOGO [Size:3.00 MB] .....OK
Reading: EXPDB [Size:10.00 MB] .....OK
Reading: ANDROID [Size:800.00 MB] .....OK
ROM info.......OK
Product: BLU
Device Model: BLU ADVANCE 4.0 L
ID: ALPS.KK1.MP7.V1
Sw Internal:
Build Date: Fri Feb 19 18:07:46 CST 2016
Chip Ver: S01
Android Version: 4.4.2
Architecture: armeabi-v7a
Read Flash (Dump) Done By EFT Dongle
@yisuscellca
CPU: MT6572
Chip Version: 0x0000ca00
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 512.00 MB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 3.64 GB
Battery:
Battery Voltage: 3938
Injection..........OK
[PRELOADER] BaseAddr(0x00000000) Size(0x00c00000)
[MBR] BaseAddr(0x00c00000) Size(0x00080000)
[EBR1] BaseAddr(0x00c80000) Size(0x00080000)
[PRO_INFO] BaseAddr(0x00d00000) Size(0x00300000)
[NVRAM] BaseAddr(0x01000000) Size(0x00500000)
[PROTECT_F] BaseAddr(0x01500000) Size(0x00a00000)
[PROTECT_S] BaseAddr(0x01f00000) Size(0x00a00000)
[SECCFG] BaseAddr(0x02900000) Size(0x00020000)
[UBOOT] BaseAddr(0x02920000) Size(0x00060000)
[BOOTIMG] BaseAddr(0x02980000) Size(0x00600000)
[RECOVERY] BaseAddr(0x02f80000) Size(0x00600000)
[SEC_RO] BaseAddr(0x03580000) Size(0x00040000)
[MISC] BaseAddr(0x035c0000) Size(0x00080000)
[LOGO] BaseAddr(0x03640000) Size(0x00300000)
[EXPDB] BaseAddr(0x03940000) Size(0x00a00000)
[ANDROID] BaseAddr(0x04340000) Size(0x32000000)
[CACHE] BaseAddr(0x36340000) Size(0x0e200000)
[USRDATA] BaseAddr(0x44540000) Size(0xa41c0000)
[BMTPOOL] BaseAddr(0xe8700000) Size(0x01500000)
Reading: ...
Reading: CACHE [Size:226.00 MB] .....OK
Reading: USERDATA [Size:2.56 GB] .....OK
Reading: PRELOADER [Size:12.00 MB] .....OK
Reading: MBR [Size:512.00 KB] .....OK
Reading: EBR1 [Size:512.00 KB] .....OK
Reading: PRO_INFO [Size:3.00 MB] .....OK
Reading: NVRAM [Size:5.00 MB] .....OK
Reading: PROTECT_F [Size:10.00 MB] .....OK
Reading: PROTECT_S [Size:10.00 MB] .....OK
Reading: SECCFG [Size:128.00 KB] .....OK
Reading: UBOOT [Size:384.00 KB] .....OK
Reading: BOOTIMG [Size:6.00 MB] .....OK
Reading: RECOVERY [Size:6.00 MB] .....OK
Reading: SEC_RO [Size:256.00 KB] .....OK
Reading: MISC [Size:512.00 KB] .....OK
Reading: LOGO [Size:3.00 MB] .....OK
Reading: EXPDB [Size:10.00 MB] .....OK
Reading: ANDROID [Size:800.00 MB] .....OK
ROM info.......OK
Product: BLU
Device Model: BLU ADVANCE 4.0 L
ID: ALPS.KK1.MP7.V1
Sw Internal:
Build Date: Fri Feb 19 18:07:46 CST 2016
Chip Ver: S01
Android Version: 4.4.2
Architecture: armeabi-v7a
Read Flash (Dump) Done By EFT Dongle
@yisuscellca