Solved Post All Your Success Stories With Your EFT Dongle
- Thread starter Easy Team
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
This topic has been solved
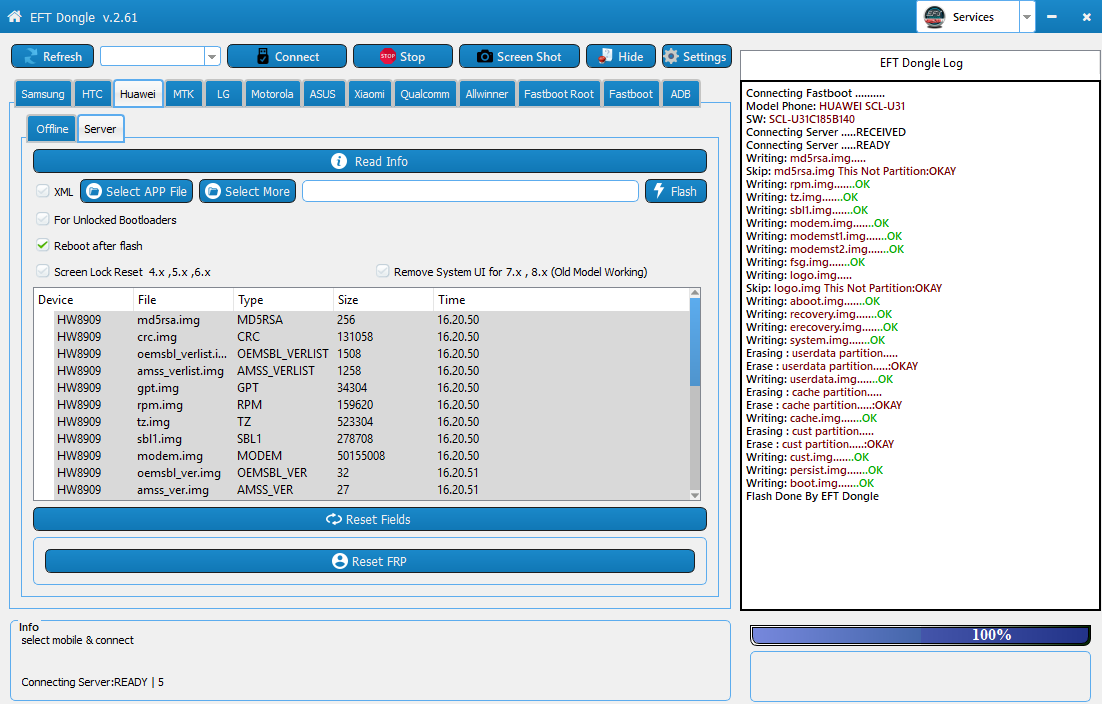
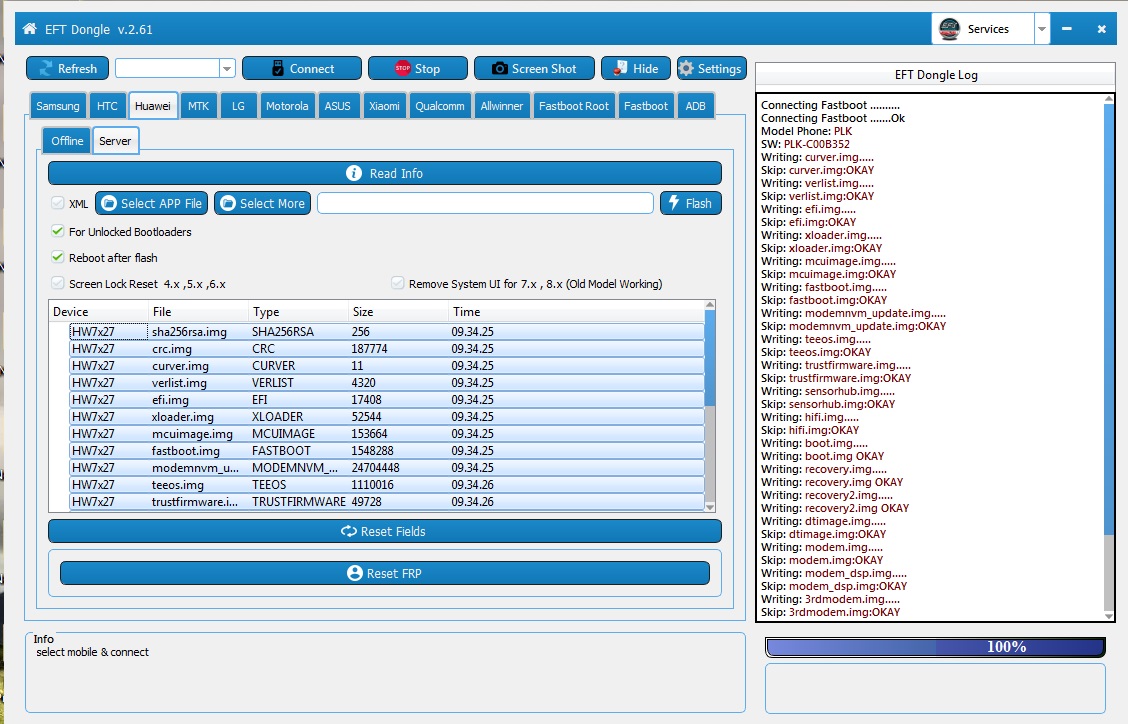
Htc j1 install g Apps done
EASY-TEAM
Waiting For Android Device.......OK
Reading Device Info.......OK
Product: HTC
Device Chipset: m7wlj
Device Model: HTC J One
Device Serial: HT36TS910643
Android Version: 4.4.3
Android SDK: 19
Architecture: armeabi-v7a
Free space in system disk: 943M
Phone Mode: Normal Mode
Checking Root Permission.......OK
install gapps ............OK
EASY-TEAM
Waiting For Android Device.......OK
Reading Device Info.......OK
Product: HTC
Device Chipset: m7wlj
Device Model: HTC J One
Device Serial: HT36TS910643
Android Version: 4.4.3
Android SDK: 19
Architecture: armeabi-v7a
Free space in system disk: 943M
Phone Mode: Normal Mode
Checking Root Permission.......OK
install gapps ............OK
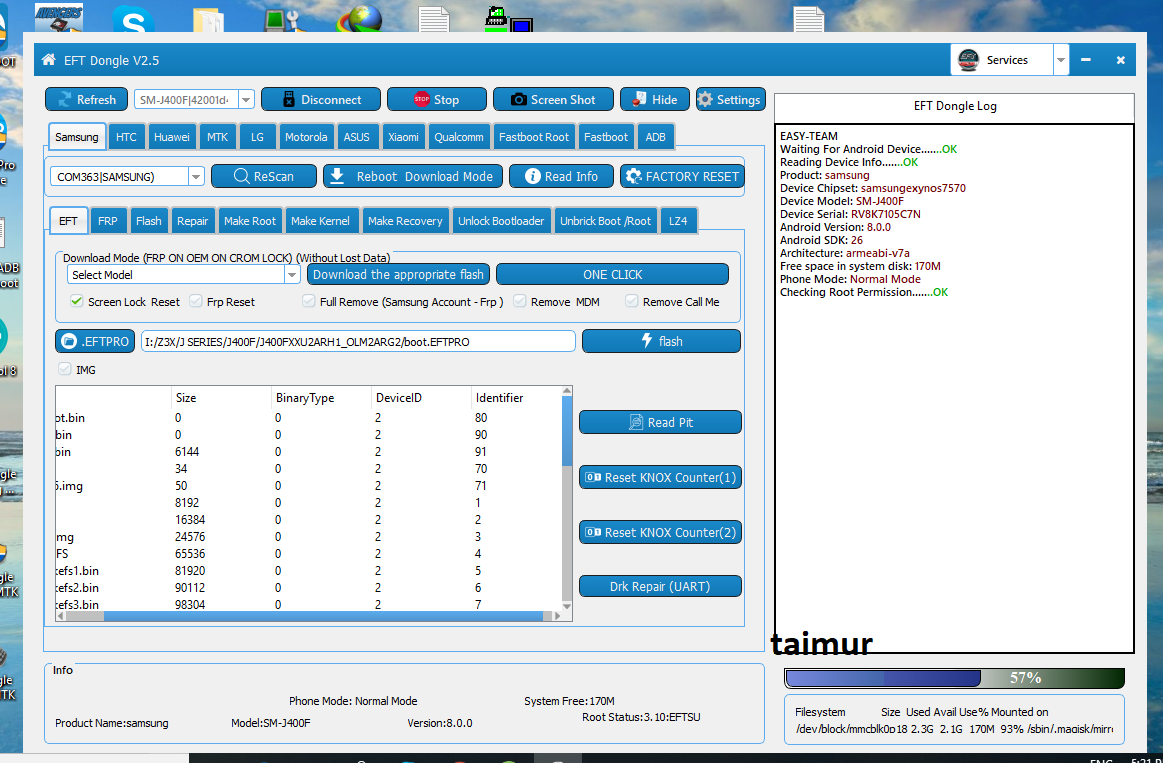
Samsung G 611f Screen Lock Remove Without Data lOst
Thx To Orignal POSter
Thx To Orignal POSter
Dr.sunilsingh
Friend's Martview
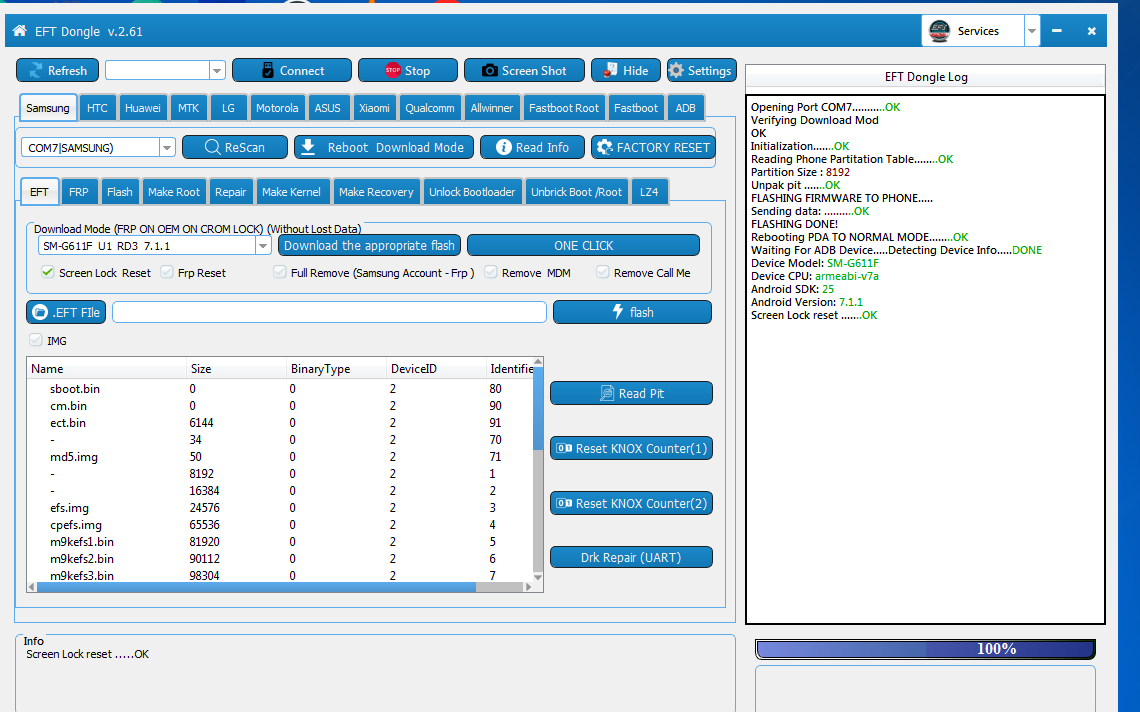
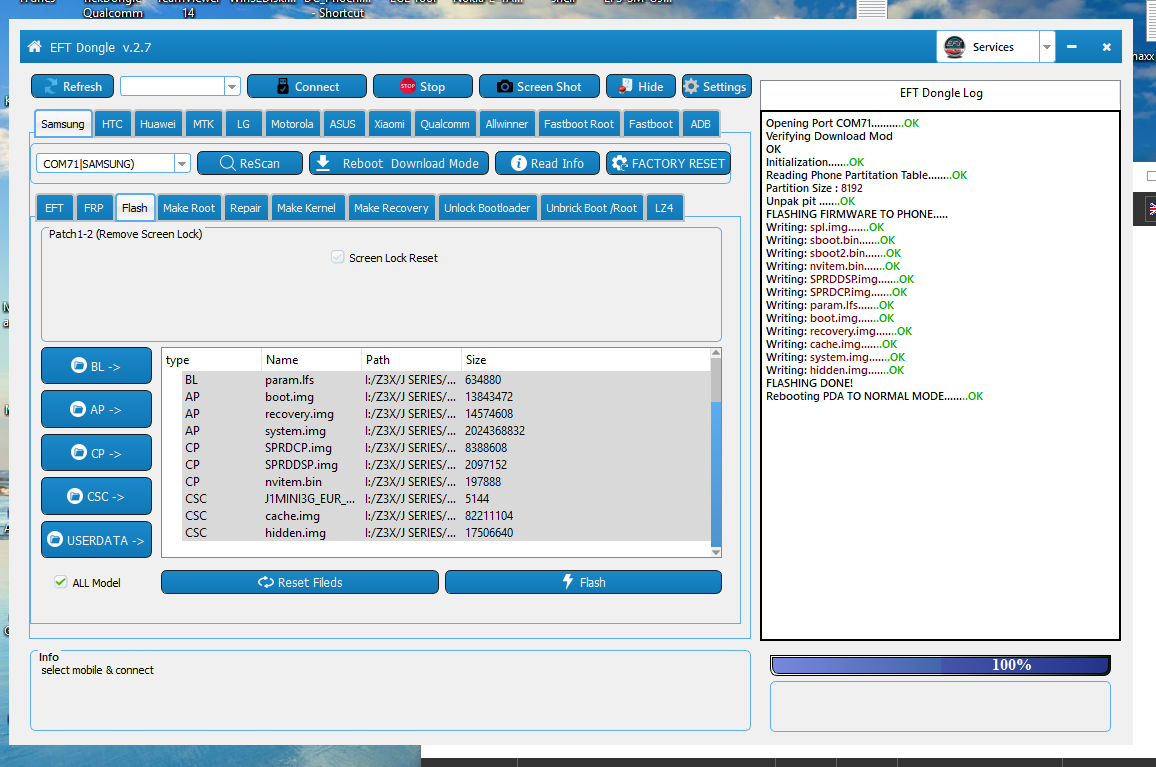
SM-G610F Android Version: 8.1.0 Resetting FRP Done
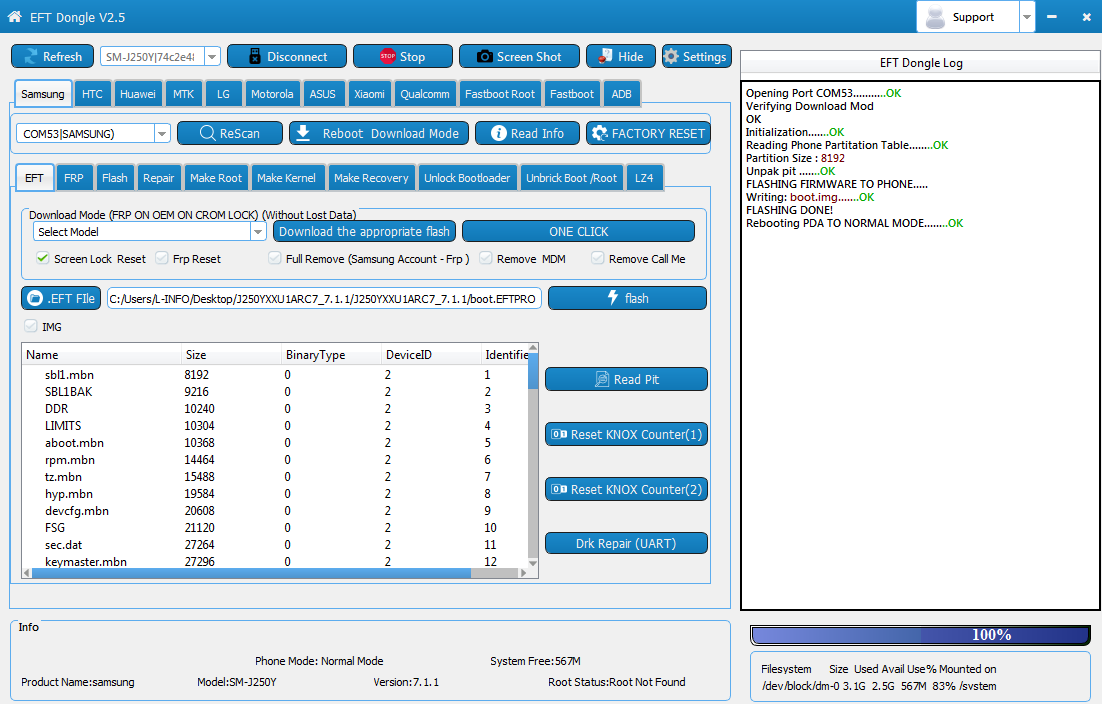
Opening Port COM4...........OK
Verifying Download Mod
OK
Initialization.......OK
Reading Phone Partitation Table........OK
Partition Size : 8192
Unpak pit .......OK
FLASHING FIRMWARE TO PHONE.....
Sending data: ..........OK
FLASHING DONE!
Rebooting PDA TO NORMAL MODE........OK
Waiting For ADB Device.....Detecting Device Info.....DONE
Device Model: SM-G610F
Device CPU: armeabi-v7a
Android SDK: 27
Android Version: 8.1.0
Resetting FRP.......OK
Opening Port COM4...........OK
Verifying Download Mod
OK
Initialization.......OK
Reading Phone Partitation Table........OK
Partition Size : 8192
Unpak pit .......OK
FLASHING FIRMWARE TO PHONE.....
Sending data: ..........OK
FLASHING DONE!
Rebooting PDA TO NORMAL MODE........OK
Waiting For ADB Device.....Detecting Device Info.....DONE
Device Model: SM-G610F
Device CPU: armeabi-v7a
Android SDK: 27
Android Version: 8.1.0
Resetting FRP.......OK
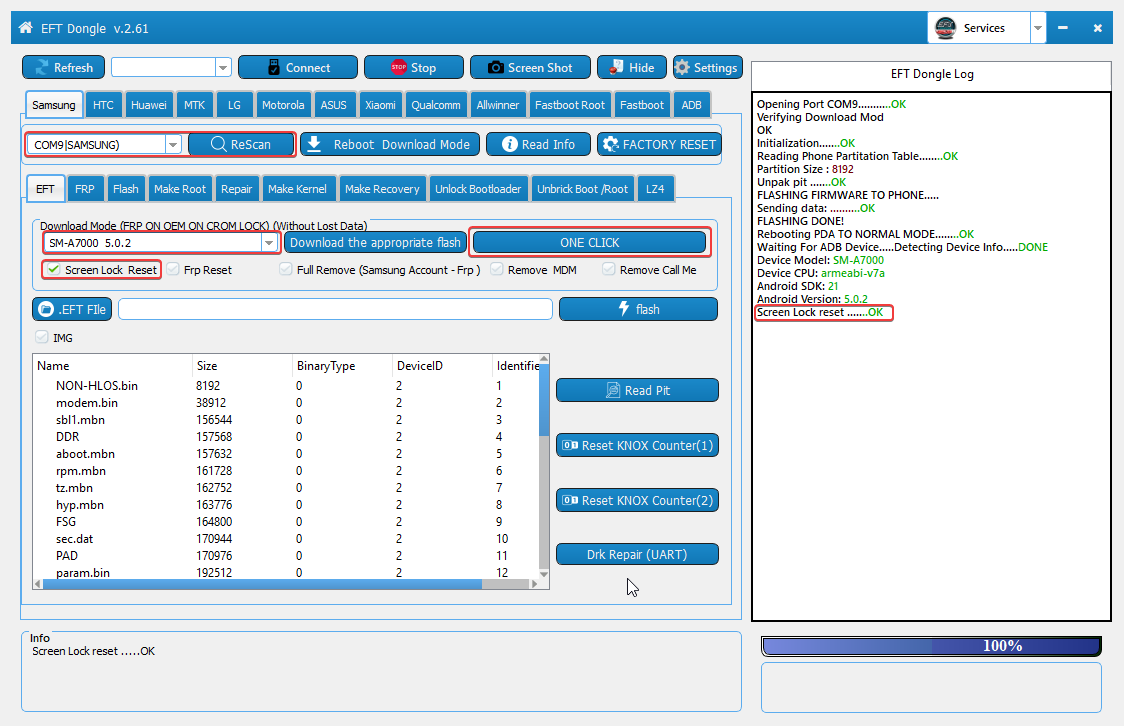
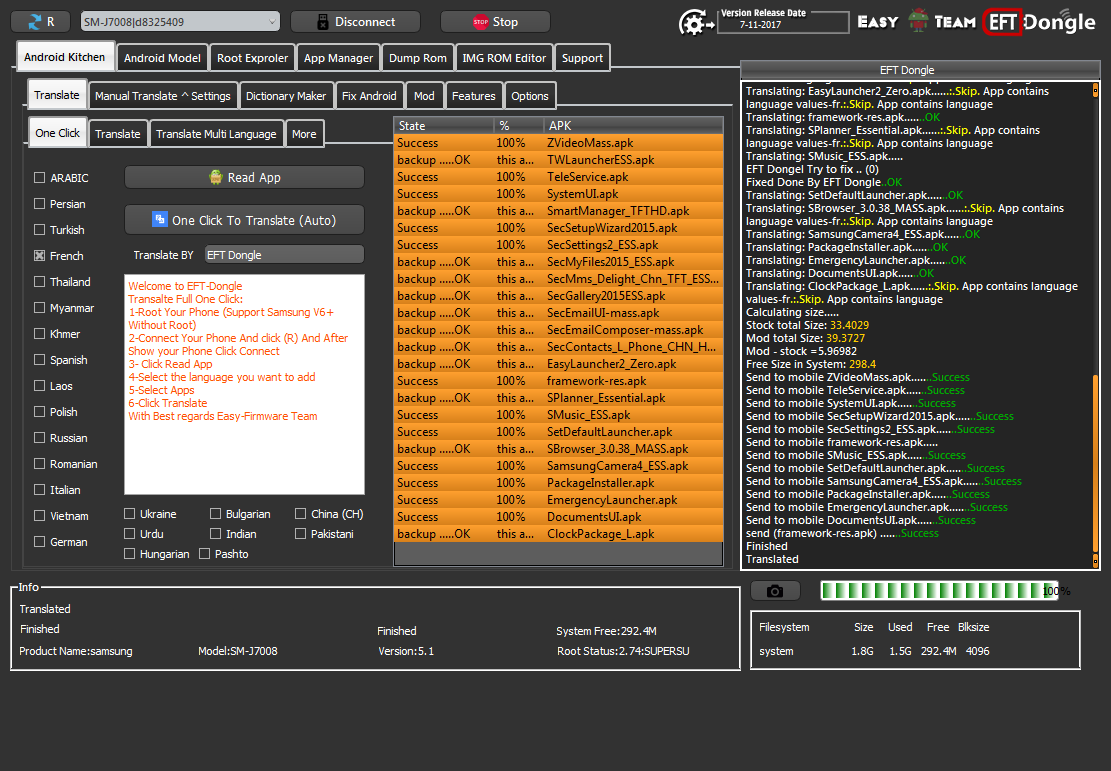
Samsung J 7008 Langauge CHange Sucess
Thx To Orignal Poster
Br
Martview Team
Thx To Orignal Poster
Br
Martview Team
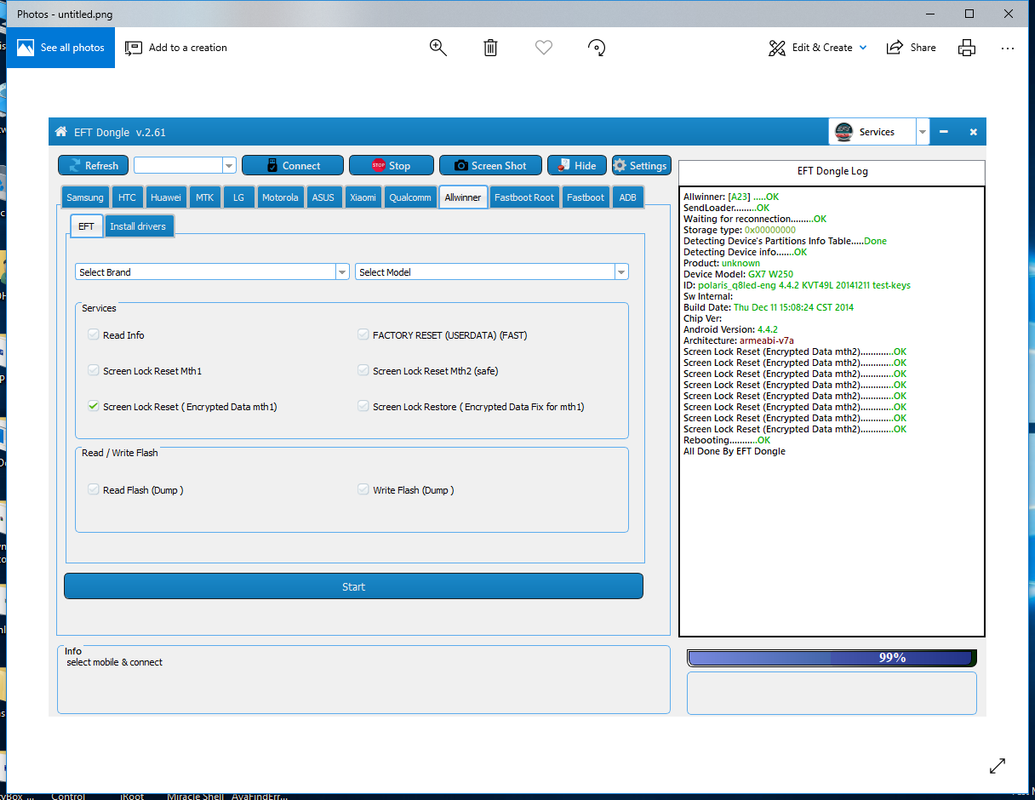
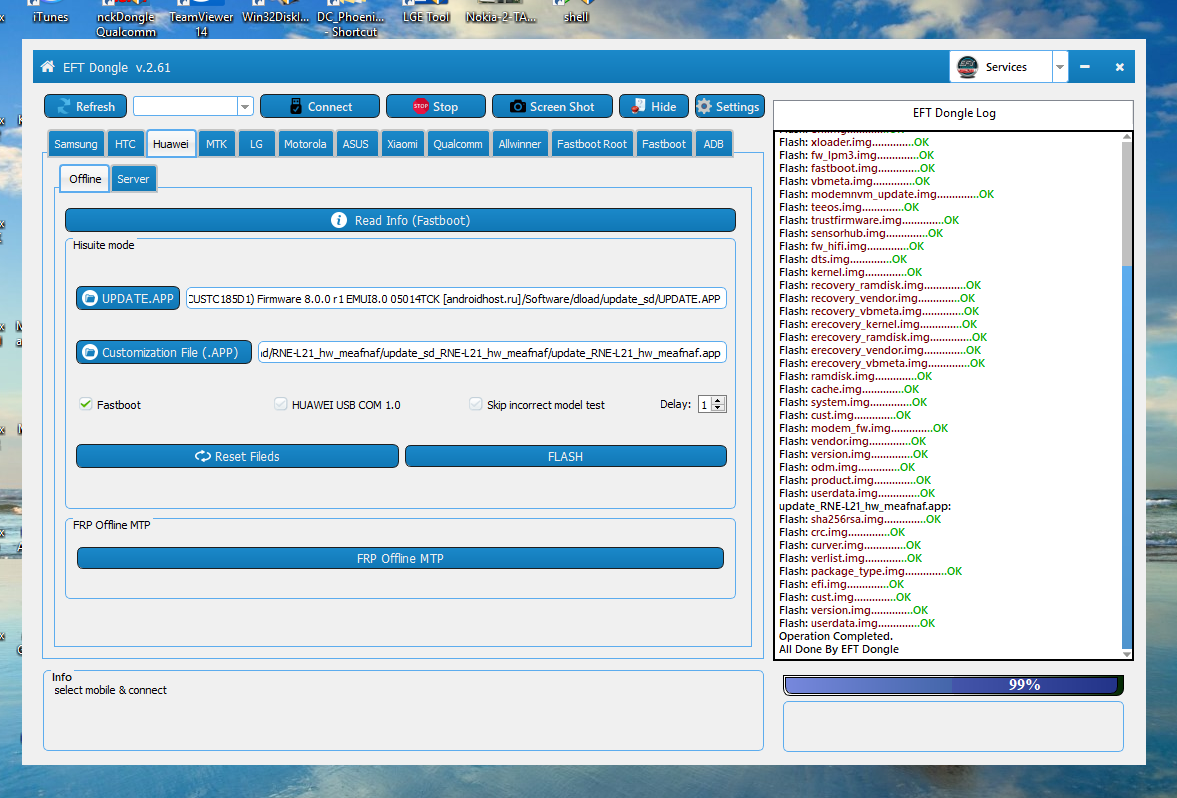
uccessfully remove by EFT dongle........
Wating Device..........OK
CPU: MT6582
Chip Version: 0x0000ca01
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 1.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 14.56 GB
Battery:
Battery Voltage: 3972
Injection..........OK
Detecting Parts info............OK
[ID: 255] [PRELOADER] BaseAddr(0x00000000) Size(0x01400000)
[ID: 255] [MBR] BaseAddr(0x01400000) Size(0x00080000)
[ID: 255] [EBR1] BaseAddr(0x01480000) Size(0x00080000)
[ID: 255] [PRO_INFO] BaseAddr(0x01500000) Size(0x00300000)
[ID: 255] [NVRAM] BaseAddr(0x01800000) Size(0x00500000)
[ID: 255] [PROTECT_F] BaseAddr(0x01d00000) Size(0x00a00000)
[ID: 255] [PROTECT_S] BaseAddr(0x02700000) Size(0x00a00000)
[ID: 255] [SECCFG] BaseAddr(0x03100000) Size(0x00020000)
[ID: 255] [UBOOT] BaseAddr(0x03120000) Size(0x00060000)
[ID: 255] [BOOTIMG] BaseAddr(0x03180000) Size(0x00600000)
[ID: 255] [RECOVERY] BaseAddr(0x03780000) Size(0x00600000)
[ID: 255] [SEC_RO] BaseAddr(0x03d80000) Size(0x00600000)
[ID: 255] [MISC] BaseAddr(0x04380000) Size(0x00080000)
[ID: 255] [LOGO] BaseAddr(0x04400000) Size(0x00300000)
[ID: 255] [EBR2] BaseAddr(0x04700000) Size(0x00080000)
[ID: 255] [EXPDB] BaseAddr(0x04780000) Size(0x00a00000)
[ID: 255] [ANDROID] BaseAddr(0x05180000) Size(0x41a00000)
[ID: 255] [CACHE] BaseAddr(0x46b80000) Size(0x07e00000)
[ID: 255] [USRDATA] BaseAddr(0x4e980000) Size(0x40000000)
[ID: 255] [FAT] BaseAddr(0x8e980000) Size(0x314b80000)
[ID: 255] [BMTPOOL] BaseAddr(0xffff00a8) Size(0x00000000)
Detecting Device info.......OK
Product: TECNO
Device Model: TECNO G9
ID: G9-T211-PIC-20140924
Sw Internal:
Build Date: Wed Sep 24 20:36:32 CST 2014
Chip Ver: S01
Android Version: 4.2.2
Architecture: armeabi-v7a
Screen Lock Reset:..........
Remove Security mth1........OK
Remove Security mth1........OK
Remove Security mth1........OK
Remove Security mth1........OK
Screen Lock Reset:.........OK
All Done By EFT Dongle
Wating Device..........OK
CPU: MT6582
Chip Version: 0x0000ca01
Chip Ext Clock: EXT_26M
Writing Mode..........OK
Internal RAM:
Internal SRAM Size: 128.00 KB
External RAM: Type DRAM
External Ram Size: 1.00 GB
EMMC:
EMMC PART BOOT1 Size: 4.00 MB
EMMC PART BOOT2 Size: 4.00 MB
EMMC PART RPMB Size: 4.00 MB
EMMC PART USER Size: 14.56 GB
Battery:
Battery Voltage: 3972
Injection..........OK
Detecting Parts info............OK
[ID: 255] [PRELOADER] BaseAddr(0x00000000) Size(0x01400000)
[ID: 255] [MBR] BaseAddr(0x01400000) Size(0x00080000)
[ID: 255] [EBR1] BaseAddr(0x01480000) Size(0x00080000)
[ID: 255] [PRO_INFO] BaseAddr(0x01500000) Size(0x00300000)
[ID: 255] [NVRAM] BaseAddr(0x01800000) Size(0x00500000)
[ID: 255] [PROTECT_F] BaseAddr(0x01d00000) Size(0x00a00000)
[ID: 255] [PROTECT_S] BaseAddr(0x02700000) Size(0x00a00000)
[ID: 255] [SECCFG] BaseAddr(0x03100000) Size(0x00020000)
[ID: 255] [UBOOT] BaseAddr(0x03120000) Size(0x00060000)
[ID: 255] [BOOTIMG] BaseAddr(0x03180000) Size(0x00600000)
[ID: 255] [RECOVERY] BaseAddr(0x03780000) Size(0x00600000)
[ID: 255] [SEC_RO] BaseAddr(0x03d80000) Size(0x00600000)
[ID: 255] [MISC] BaseAddr(0x04380000) Size(0x00080000)
[ID: 255] [LOGO] BaseAddr(0x04400000) Size(0x00300000)
[ID: 255] [EBR2] BaseAddr(0x04700000) Size(0x00080000)
[ID: 255] [EXPDB] BaseAddr(0x04780000) Size(0x00a00000)
[ID: 255] [ANDROID] BaseAddr(0x05180000) Size(0x41a00000)
[ID: 255] [CACHE] BaseAddr(0x46b80000) Size(0x07e00000)
[ID: 255] [USRDATA] BaseAddr(0x4e980000) Size(0x40000000)
[ID: 255] [FAT] BaseAddr(0x8e980000) Size(0x314b80000)
[ID: 255] [BMTPOOL] BaseAddr(0xffff00a8) Size(0x00000000)
Detecting Device info.......OK
Product: TECNO
Device Model: TECNO G9
ID: G9-T211-PIC-20140924
Sw Internal:
Build Date: Wed Sep 24 20:36:32 CST 2014
Chip Ver: S01
Android Version: 4.2.2
Architecture: armeabi-v7a
Screen Lock Reset:..........
Remove Security mth1........OK
Remove Security mth1........OK
Remove Security mth1........OK
Remove Security mth1........OK
Screen Lock Reset:.........OK
All Done By EFT Dongle
Opening Port COM11...........OK
Verifying Download Mod
OK
Initialization.......OK
Reading Phone Partitation Table........OK
Partition Size : 8192
Unpak pit .......OK
FLASHING FIRMWARE TO PHONE.....
Sending data: ..........OK
Sending data2: ........OK
FLASHING DONE!
Rebooting PDA TO NORMAL MODE........OK
Please Enter your device into recovery mode
Waiting Adb in Recovery Mode.....DONE
Detecting Device Info.....DONE
Device Model: SM-G532F
Device CPU: armeabi-v7a
Android SDK: 23
Android Version: 6.0.1
Found protection1
Protection1 has been deleted
Found protection2
Protection2 has been deleted..OK
Verifying Download Mod
OK
Initialization.......OK
Reading Phone Partitation Table........OK
Partition Size : 8192
Unpak pit .......OK
FLASHING FIRMWARE TO PHONE.....
Sending data: ..........OK
Sending data2: ........OK
FLASHING DONE!
Rebooting PDA TO NORMAL MODE........OK
Please Enter your device into recovery mode
Waiting Adb in Recovery Mode.....DONE
Detecting Device Info.....DONE
Device Model: SM-G532F
Device CPU: armeabi-v7a
Android SDK: 23
Android Version: 6.0.1
Found protection1
Protection1 has been deleted
Found protection2
Protection2 has been deleted..OK