Huawei JAT-L03 (Y6s 2019) FRPL successfully removed by Hydra Tool
Screen Short:
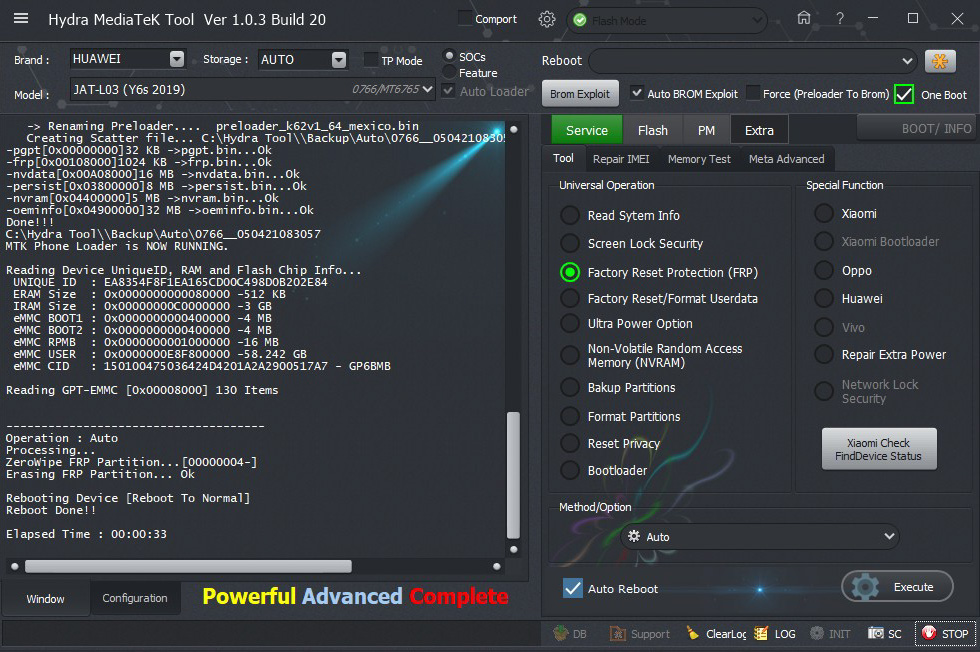
Logs:
1. Run MTK tool of Hydra Dongle.
2. Choose Correct Module and Brand.
3. Go to "Service" -- > "Tool"
4. choose "Factory Reset Protection (FRP)".
5. Choose "Auto" from "Method / Option" drop down menu.
6. Click on "Execute" and connect device with computer using USB cable.
7. Wait until the process is completed.
2. Choose Correct Module and Brand.
3. Go to "Service" -- > "Tool"
4. choose "Factory Reset Protection (FRP)".
5. Choose "Auto" from "Method / Option" drop down menu.
6. Click on "Execute" and connect device with computer using USB cable.
7. Wait until the process is completed.
Screen Short:

Logs:
BR=====================================
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM10)
SymbolicName :\??\USB#VID_0E8D&PID_0003#5&521a615&0&7#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Handshaking...Ok
Identifying Hardware ID.....
BROM CPUID : 0766MT6765[6765]
BROM HW_SW_VER : 8A00 CA00 0000 0000
getMTKPayloadExploit : 0766
#Executing Exploit..
#SUCCESS..
Handshaking...Ok
Identifying Hardware ID.....
BROM CPUID : 0766MT6765[6765]
BROM HW_SW_VER : 8A00 CA00 0000 0000
FUSEID : 00000000
SECURE VERSION : 05
BL VERSION : FE
BR Secured : E0
Preparing Download Agent..
DA : Huawei__6765_8A00CA0000000000_00001000_00030000.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2018/10/18.17:38_452898
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Mode : brom
Preloader Initialization...
Parsing preloader_k62v1_64_mexico.bin
Init : Accepted
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : EA8354F8F1EA165CD00C498D0B202E84
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 150100475036424D4201A2A2900517A7 - GP6BMB
DA Speed : high-speed
Reading GPT-EMMC [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_k62v1_64_mexico.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__050421083057\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x00108000]1024 KB ->frp.bin...Ok
-nvdata[0x00A08000]16 MB ->nvdata.bin...Ok
-persist[0x03800000]8 MB ->persist.bin...Ok
-nvram[0x04400000]5 MB ->nvram.bin...Ok
-oeminfo[0x04900000]32 MB ->oeminfo.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__050421083057
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : EA8354F8F1EA165CD00C498D0B202E84
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 150100475036424D4201A2A2900517A7 - GP6BMB
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...[00000004-]
Erasing FRP Partition... Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:33
Mount Everest


