SFT Dongle v1.0.19
Release DATE: 28th MAY 2019
-----------------------------------------------------------------------

DOWNLOAD LINK CLICK HERE
=================================================================================================================
BUY FROM RESELLER LISTED AT THIS OFFICIAL WEBSITE
=================================================================================================================
Release DATE: 28th MAY 2019
-----------------------------------------------------------------------
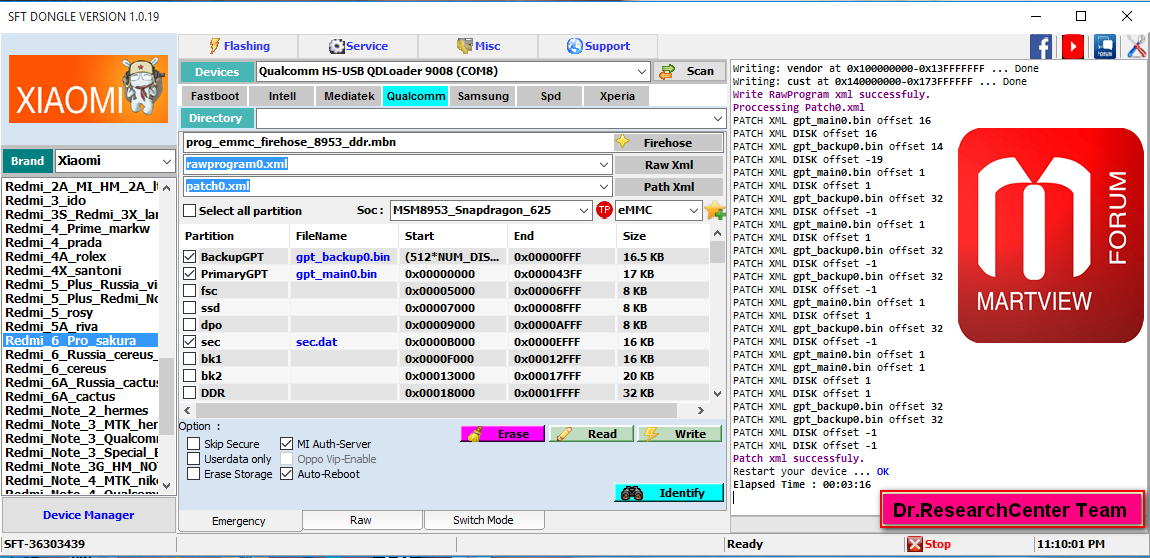
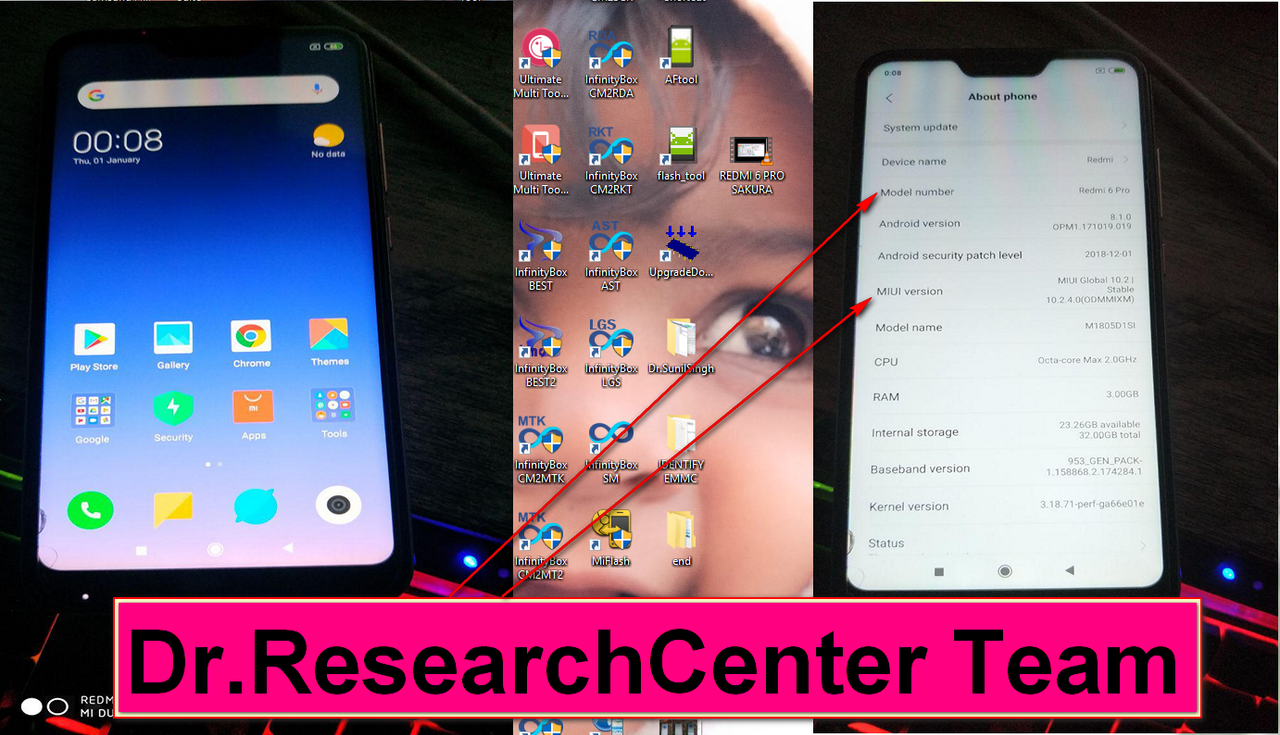
- ADD: Adding Sign auth for Mi Type New (free 1 month trial period )
- ADD: Identity,Read, Erase, Write with Mi-Auth Qualcomm [ First in the word ]
- ADD: Adding Mount Fs Info Mi-Account
- ADD: Adding Remove Paternlock vivo New Security Without lost data [ user data encrypted ]
- ADD: New command manual fastboot
- ADD: Brom MTK Support new model
- BUG: Repair remove pattern lock vivo ( clean data ) Qualcomm & mtk
- BUG: Repair micloud method 2 type old MI
- BUG: Repair Clean Micloud method 2
- BUG: Write Debrick Intell

DOWNLOAD LINK CLICK HERE
=================================================================================================================
BUY FROM RESELLER LISTED AT THIS OFFICIAL WEBSITE
=================================================================================================================
Last edited: