Huawei MED-L09 (Y6P) Remove Account is successfully done by Hydra Tool
Screen Short:
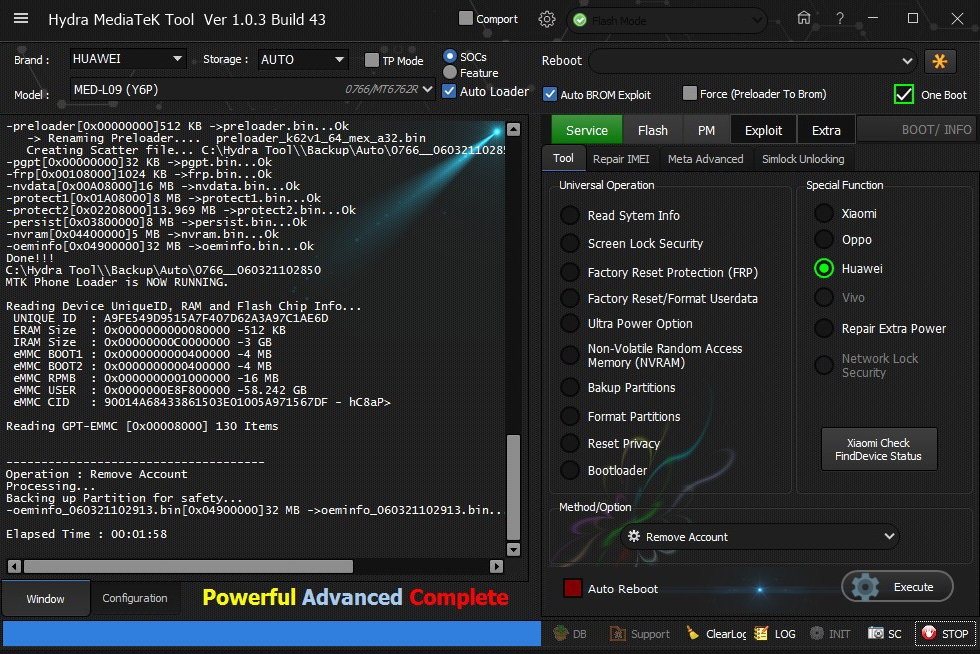
Logs:
1. Run Hydra MTK Module and choose "Sosc"
2. Select Brand and Model
3. Go to Service-->Tool
4. Choose "Huwei".
5. Choose "Remove Account" from "Option / Method" drop down menu
6. Click on "Execute".
7. connect the device to the computer with data cable
8. wait until the process is completed.
2. Select Brand and Model
3. Go to Service-->Tool
4. Choose "Huwei".
5. Choose "Remove Account" from "Option / Method" drop down menu
6. Click on "Execute".
7. connect the device to the computer with data cable
8. wait until the process is completed.
Screen Short:

Logs:
BR=====================================
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM15)
Device :7&6f3d3a3&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#7&6f3d3a3&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SB : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SB : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
FUSEID : 00000000
SECURE VERSION : 05
BL VERSION : FE
NORMAL BOOT
Preparing Download Agent..
DA : MT6765_Huawei_MED.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2018/10/18.17:38_452898
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : New
Synchronization...[ERROR]- NOT SYNC
=============================================
Reasons why it fails due to the following"
1. Harware problem/issues
2. If you did Testpoint Kindly check the parts you Touch/TP
3. Powershortage, try to connect Battery
4. Check or replace usb cable and plug directly to your pc usb port.
=============================================
SYNC
Mode : brom
Preloader Initialization...
Parsing preloader_k62v1_64_mexico.bin
Init : Accepted
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : A9FE549D9515A7F407D62A3A97C1AE6D
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 90014A68433861503E01005A971567DF - hC8aP>
DA Speed : high-speed
Reading GPT-EMMC [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_k62v1_64_mex_a32.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__060321102850\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x00108000]1024 KB ->frp.bin...Ok
-nvdata[0x00A08000]16 MB ->nvdata.bin...Ok
-protect1[0x01A08000]8 MB ->protect1.bin...Ok
-protect2[0x02208000]13.969 MB ->protect2.bin...Ok
-persist[0x03800000]8 MB ->persist.bin...Ok
-nvram[0x04400000]5 MB ->nvram.bin...Ok
-oeminfo[0x04900000]32 MB ->oeminfo.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__060321102850
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : A9FE549D9515A7F407D62A3A97C1AE6D
ERAM Size : 0x0000000000080000 -512 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 90014A68433861503E01005A971567DF - hC8aP>
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Remove Account
Processing...
Backing up Partition for safety...
-oeminfo_060321102913.bin[0x04900000]32 MB ->oeminfo_060321102913.bin...Ok Ok
Elapsed Time : 00:01:58
Mount Everest


