A14 | 12 Pro Bypass (iPhone13,3)
iOS Version: 26.1
Preparing Environment : OK
Monitoring for device...
✓ Device Connected
Model: A14 | 12 Pro Bypass (iPhone13,3)
iOS Version: 26.1
Serial Number: DNPF6B4B0D83
UDID: 00008101-00120DE026FA001E
Activation State: Unactivated
Unsupported iOS version: 26.1
User chose to proceed although the version is under testing.
Starting activation process...
Starting attempt 1/6
Activation attempt 1 in progress...
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device reconnected successfully
Collecting system logs...
System logs collected successfully via IosClass_ method
Extracting log archive: 00008101-00120DE026FA001E.logarchive
Log archive extracted successfully to: C:/Program Files (x86)/EFT Dongle/./00008101-00120DE026FA001E.logarchive
Analyzing device data...
Contacting activation server...
Server response received successfully
Downloading activation data...
Activation data downloaded successfully
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Applying activation data to device via IosClass_ method...
Activation data applied successfully via exe method
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device reconnected successfully
Attempt 1 failed
Preparing next attempt...
Starting attempt 2/6
Activation attempt 2 in progress...
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device reconnected successfully
Collecting system logs...
System logs collected successfully via IosClass_ method
Extracting log archive: 00008101-00120DE026FA001E.logarchive
Log archive extracted successfully to: C:/Program Files (x86)/EFT Dongle/./00008101-00120DE026FA001E.logarchive
Analyzing device data...
Contacting activation server...
Server response received successfully
Downloading activation data...
Activation data downloaded successfully
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Applying activation data to device via IosClass_ method...
Activation data applied successfully via exe method
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device reconnected successfully
Attempt 2 failed
Preparing next attempt...
Starting attempt 3/6
Activation attempt 3 in progress...
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device reconnection timeout
Device did not reconnect after reboot
Attempt 3 failed
Preparing next attempt...
Starting attempt 4/6
Cannot detect device, waiting...
Starting attempt 5/6
Activation attempt 5 in progress...
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device activated during reconnection
Collecting system logs...
System logs collected successfully via IosClass_ method
Extracting log archive: 00008101-00120DE026FA001E.logarchive
Log archive extracted successfully to: C:/Program Files (x86)/EFT Dongle/./00008101-00120DE026FA001E.logarchive
Analyzing device data...
Contacting activation server...
Server response received successfully
Downloading activation data...
Activation data downloaded successfully
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Removing file from device
File removed successfully from device
Applying activation data to device via IosClass_ method...
Activation data applied successfully via exe method
Rebooting device via IosClass_ method...
Device rebooted successfully
Waiting for device to reconnect...
Device activated during reconnection
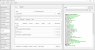
=== ACTIVATION SUCCESSFUL ===
Device has been successfully activated!
Operation {Bypass A12} ID: 30F3020D76BFD773
Elapsed time 08:18 -- Version 5.3.3 Release 0001 B[/COLOR