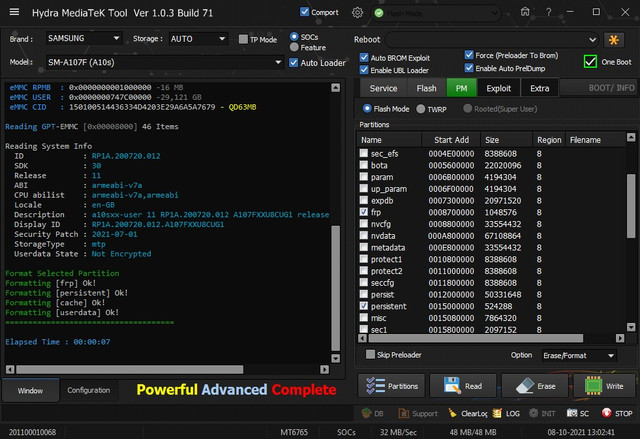
Brand : SAMSUNG Model : SM-A107F (A10s) Connection : Flash Mode
=====================================
How To Boot : Power off phone
* BROM Mode : Press VOL + or Press VOL -+
* Preloader Mode : Just Insert cable
Searching for MTK Device...Found
Port Identification :Flashmode Preloader
FriendlyName :MediaTek PreLoader USB VCOM (Android) (COM18)
Device :5&2fed3dae&0&6
SymbolicName :\??\USB#VID_0E8D&PID_2000#5&2fed3dae&0&6#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2016,3.2
Opened handle..
Handshaking...Ok
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM21)
Device :5&2fed3dae&0&6
SymbolicName :\??\USB#VID_0E8D&PID_0003#5&2fed3dae&0&6#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2016,3.2
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking...Ok
C:\Hydra Tool\Backup\Preloader_dump\prel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 09D9667D48A7CD40AA4F89ABF333A2ED
Stage 1..[Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 4B6F962096B0254E16F1D23011E1EA6B
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29,121 GB
eMMC CID : 150100514436334D4203E29A6A5A7679 - QD63MB
Executing : ACCEPTED...
Reading GPT-EMMC [0x00008000] 46 Items
Reading System Info
ID : RP1A.200720.012
SDK : 30
Release : 11
ABI : armeabi-v7a
CPU abilist : armeabi-v7a,armeabi
Locale : en-GB
Description : a10sxx-user 11 RP1A.200720.012 A107FXXU8CUG1 release-keys
Display ID : RP1A.200720.012.A107FXXU8CUG1
Security Patch : 2021-07-01
StorageType : mtp
Userdata State : Not Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_s96116ca1.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\0766__100821125810\MT6765_Android_scatter.txt
-pgpt[0x00000000]4 MB ->pgpt.bin...Ok
-nvram[0x00600000]64 MB ->nvram.bin...Ok
-frp[0x08700000]1024 KB ->frp.bin...Ok
-nvdata[0x0A800000]64 MB ->nvdata.bin...Ok
-protect1[0x10800000]8 MB ->protect1.bin...Ok
-protect2[0x11000000]8 MB ->protect2.bin...Ok
-persist[0x12000000]48 MB ->persist.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\0766__100821125810
MTK Phone Loader is NOW RUNNING.
=====================================
Elapsed Time : 00:00:47