UFI Software version 1.4.0.1464
UFI 4th Anniversary Update is out

Whats NEW :
Mirror Link :
Mega
Mediafire
GDrive

UFI 4th Anniversary Update is out

Whats NEW :
Code:
!!! WARNING: Do not rename "BRAND" and "MODEL" list to be different as at support site, certain features might not working properly !!!
General changes:
Introducing UFIBox firmware version 1.13
Latest firmware for supported models (Nokia, Meizu, Xiaomi, Oppo, Vivo and others) was uploaded to support servers
Remapped [USB] Device Manager toolbox menu
Revised upgrade firmware routine for boxed with new hardware version
eMMC ToolBox changes:
ADD: Improved reading system information for Android with Project Treble and Android A/B system
BUGFIX: Handing extracted OFP files
WARNING: Extracted OFP firmwares is still encrypted and can only be used from within the UFI Software(including eMMC ToolBox)
Always use self extracted firmware image from OFP file, never use firmware extracts downloaded from internet that are known to have been extracted using UFI software
Using this fimware with other tools may result in bricked devices !!!
BUGFIX: Minor bugfixes and improvements
Android ToolBox changes:
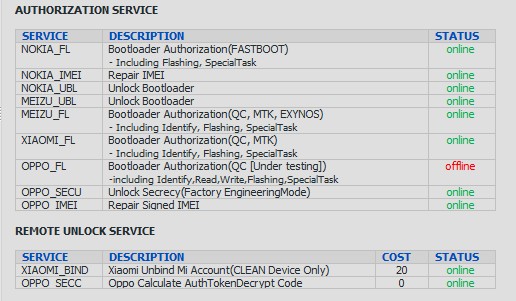
ADD: Introducing UFI CREDIT for flash authentication, unlock bootloader and repair signed imei for new security phones
Currently implemented:
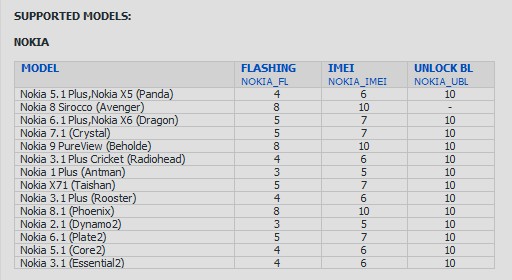
Nokia (by HMD Global) supports for flashing(QC, MTK), repair imei, unlock bootloader
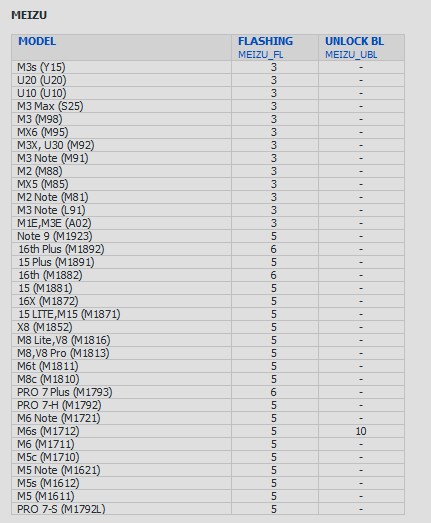
Meizu supports for flashing(QC, MTK, EXYNOS), unlock bootloader(EXYNOS)
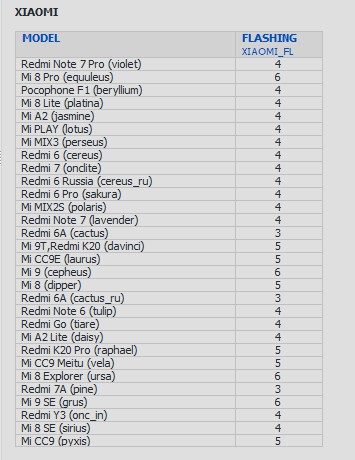
Xiaomi supports for flashing(QC, MTK), unlock bootloader for some devices
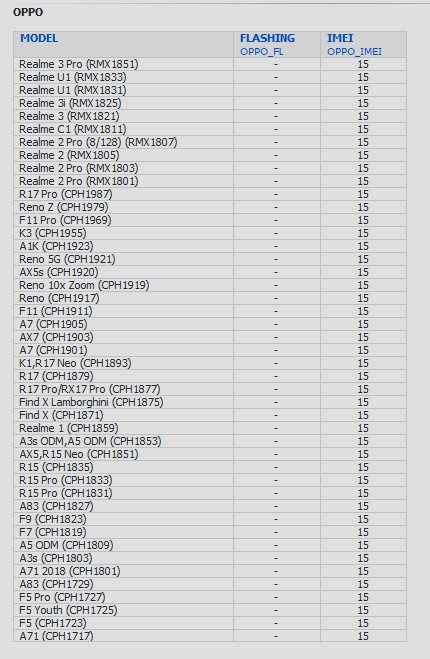
Oppo supports for flashing(QC) and repair imei(QC, MTK)
ADD: Full support for Nokia phones (by HMD Global)
- Support for phones with old security and new security version: 4 and security version: 8
- Normal flashing via Fastboot mode (both for old and newer phones, requires authentication)
- Unlock Bootloader via "FASTBOOT->Special Task" (requires credits)
- Repair IMEI via "SERVICE->IMEI & PROD ID", need to run in FTM MODE before IMEI tasks(requires authentication)
ADD: Support for Meizu with Exynos platform
- Normal flashing via Fastboot mode(requires authentication)
- Unlock Bootloader via "FASTBOOT->Special Task" (requires credits)
ADD: Support for Latest Oppo phones(Qualcomm platform)
- Normal flashing via Qualcomm EDL mode (requires authentication)
ADD: Full support for Latest Xiaomi phones(Qualcomm and MediaTek platform)
- Normal flashing via Qualcomm EDL mode and MTK BootRom mode(requires authentication)
- Unlock Bootloader for some phones via "FASTBOOT->Special Task"
ADD: IMEI repair support for Newer Oppo phones
- IMEI repair for Oppo requires to have a pair of PCBA Number and Both IMEI number(requires credits)
ADD: Erase FRP and Erase Userdata option while flashing
For effective flashing task, you can now automated Erase FRP and/or Userdata on flashing
ADD: On MediaTek devices, After Identify phones will stay in DA mode so next time you need to do -
some tasks(Write, Erase, Special Task, etc) the software will resume the DA session and continue the task
Note that: DA session will lost if USB disconnected, changing BROM version or you close the UFI software
ADD: Erase FRP and Userdata support with Newer Vivo phones with new security
ADD: Merged IMEI and Product ID functions to "SERVICE->IMEI & PROD ID" tab
ADD: "SERVICE->TOOLS" tab
[Oppo] Secrecy Unlock used to Decrypt Factory Engineering Mode, after unlock you can Unlock Region Lock, Enable DIAG or META mode
[META] Master Clear used to Erase Internal Storage (may work for some old models)
ADD: "SERVICE->REMOTE SERVICE" tab
All Remote Services will be available here(some services can be free or requires credits)
Currently available:
Xiaomi Unbind Mi Account(CLEAN Device Only) by SN
Oppo Calculate AuthTokenDecrypt Code, Similliar to Secrecy Unlock but it done remotely without access to the phone physically
ADD: Added Latest MediaTek BROM version 7.1917.3.0 for latest MediaTek chipset with new PL signature type
BUGFIX: Improved rawprogram.xml parsing to handle misconfigured items for unsplited/sparsed images(vivo)
BUGFIX: Improved ADB Logcat features
BUGFIX: Improved Debug Uart Terminal features (Note that Debug Uart for MediaTek platform requires 921600 baudrate)
BUGFIX: Minor bugfixes and improvements
NOTE:
All features which requires authentication will require credit
Some remote services are free but are required to have atleast 1 credits in your account
See "[ACCOUNT]" menu to see latest available services, status and the service cost
The credits top up system can be accessed directly there
Payment can be made with Paypal(for International) and GO-PAY(For Indonesia)
Credits can also be purchased from available resellersMirror Link :
Mega
Mediafire
GDrive

Last edited by a moderator: