Vivo Y12 (1901 PD19013F ) FRP successfully removed by Hydra Tool
Screen Short:
Logs:
Screen Short:

Logs:
BRBrand : VIVO Model : Y12 (1901 PD19013F) Connection : Flash Mode
=====================================
Connection
-Please wait...
-Connect Phone...
-Found...
-PreLoader...[COM8]
TPortConnection.Create...(COM8)..Opening...Ok
Handshaking...Ok
Identifying Hardware ID.....
BROM CPUID : 0766 (0000)MT6765[6765]
BROM HW_SW_VER : 8A00 CA00 0000 0000
FUSEID : 00000000
SECURE VERSION : FF
BL VERSION : 03
BR Secured : 05
NORMAL BOOT
Preparing Download Agent..
DA : [Not Exist]
Trying Default 6765_PL.bin
Agent: MTK_DOWNLOAD_AGENT -HYDRA
Ver : MTK_AllInOne_DA_v3.3001.2018/03/20.21:09_402229+403250
Init : Loader [1]
Sending : Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Mode : preloader
Execute Secondary Loader
Init : Loader [2]
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : E4AE66F8078E46FF86652B0B8D431807
ERAM Size : 0x0000000000040000 -256 KB
IRAM Size : 0x0000000030000000 -768 MB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
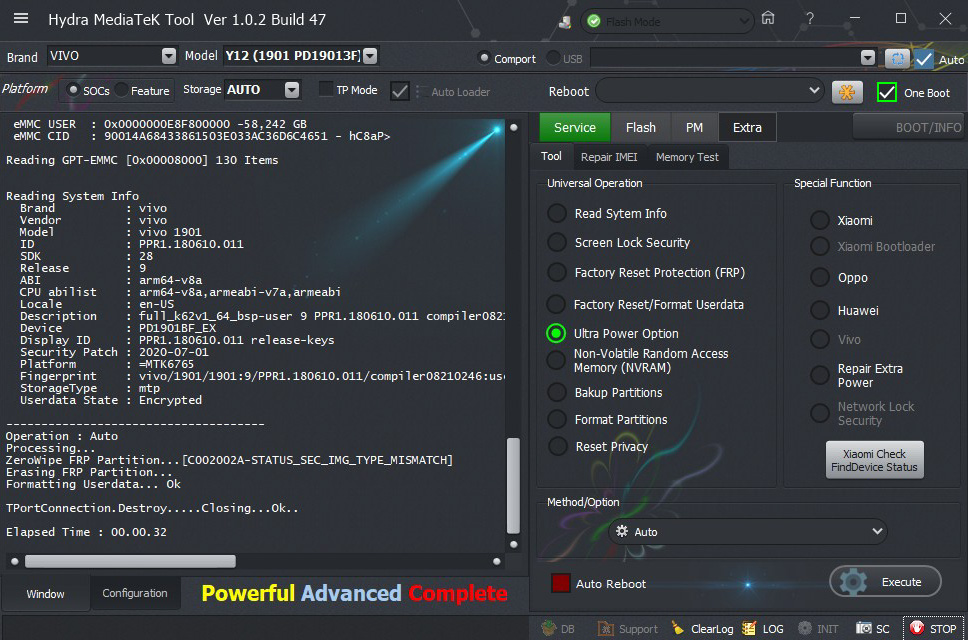
eMMC USER : 0x0000000E8F800000 -58,242 GB
eMMC CID : 90014A68433861503E033AC36D6C4651 - hC8aP>
DA Speed : high-speed
DA Speed : high-speed
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : vivo
Vendor : vivo
Model : vivo 1901
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k62v1_64_bsp-user 9 PPR1.180610.011 compiler08210246 release-keys
Device : PD1901BF_EX
Display ID : PPR1.180610.011 release-keys
Security Patch : 2020-07-01
Platform : =MTK6765
Fingerprint : vivo/1901/1901:9/PPR1.180610.011/compiler08210246:user/release-keys
StorageType : mtp
Userdata State : Encrypted
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader.... preloader_k62v1_64_bsp.bin
Creating Scatter file... C:\Hydra Tool\\Backup\Auto\vivo_vivo 1901_0766-=MTK6765-9_PPR1.180610.011 release-keys_220121143516\MT6765_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x05588000]1024 KB ->frp.bin...Ok
-nvdata[0x07688000]64 MB ->nvdata.bin...Ok
-persist[0x18800000]48 MB ->persist.bin...Ok
-nvram[0x24680000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\\Backup\Auto\vivo_vivo 1901_0766-=MTK6765-9_PPR1.180610.011 release-keys_220121143516
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : E4AE66F8078E46FF86652B0B8D431807
ERAM Size : 0x0000000000040000 -256 KB
IRAM Size : 0x0000000030000000 -768 MB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58,242 GB
eMMC CID : 90014A68433861503E033AC36D6C4651 - hC8aP>
Reading GPT-EMMC [0x00008000] 130 Items
Reading System Info
Brand : vivo
Vendor : vivo
Model : vivo 1901
ID : PPR1.180610.011
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k62v1_64_bsp-user 9 PPR1.180610.011 compiler08210246 release-keys
Device : PD1901BF_EX
Display ID : PPR1.180610.011 release-keys
Security Patch : 2020-07-01
Platform : =MTK6765
Fingerprint : vivo/1901/1901:9/PPR1.180610.011/compiler08210246:user/release-keys
StorageType : mtp
Userdata State : Encrypted
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...[C002002A-STATUS_SEC_IMG_TYPE_MISMATCH]
Erasing FRP Partition...
Formatting Userdata... Ok
TPortConnection.Destroy.....Closing...Ok..
Elapsed Time : 00.00.32
Mount Everest


