Vivo Y81i (1812) Flashing done with Hydra Tool
- First Keep Press Boot Info
- Select firmware and click execute
- First Keep Press Boot Info
Code:
-------------------------------------------------------
To Enable BROM Mode :
Method 1 - Bootkey (Vol + - Power) or any combination
Method 2 - Enable Preloader to brom(crashing Method)
Method 3 - Test Point Data0 + ground
To Enable Preloader Mode :
Method 1 - Just Insert cable
-------------------------------------------------------
Searching for MTK Device...Found
MTK Port Type : Flashmode BROM
FriendlyName : MediaTek USB Port_V1633 (COM4)
Device : /6&37254210&0&4
SymbolicName : \\?\usb#vid_0e8d&pid_0003#6&37254210&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Service : wdm_usb
Openning Port [COM4] Ok
Handshaking...Ok
HwCode : 0717 {MT6761/MT6762/MT3369/MT8766B}
Hwver : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Connection : BROM
HW Subcode : 8A00
HW Subcode : CA01
SW Ver : 0200
ME_ID : 820D42FD152D436532D17D77D6118563
SOC_ID : F4D91C36D3D43BA509BF9E2EBF5C5DDFA6CC7E1F565A7414884E8613CC43E70C
Exploiting Device...
Successfully Exploited..
Handshaking...Ok
Dumping Preloader from Bootrom..
Seeking preloader address..Found @ 0x00200BC4
Starting to dump...
Prel Size : 0x0003B72C
Successfully dump preloader.. [C:\Hydra Tool\Boot\PreloaderDump\preloader_k61v1_64_bsp.bin]
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
Connection : BROM
Preparing Download Agent..[MTK_AllInOne_DA_5.2152.bin]
Patching da2 ... Ok
Uploading Stage 1....
Successfully uploaded stage 1, jumping ..
Executing JUMP_DA Address @ 0x00200000
Jumping to 0x00200000 Ok 0xC0
Successfully received DA sync
ONNECTION_AGENT : brom
DRAM config needed for : 90014A4841473461
Sending auto preloader from dump... [preloader_k61v1_64_bsp.bin]
Sending emi data.. [DRAM setup passed.]
Sending emi data succeeded.
Uploading stage 2...
Upload data was accepted. Jumping to stage 2...
Successfully uploaded stage 2
ERAM Size : 0x000000000003A500-233.25 KB
IRAM Size : 0x0000000080000000-2 GB
EMMC Boot1 Size : 0x0000000000400000-4 MB
EMMC Boot2 Size : 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000000400000-4 MB
EMMC USER Size : 0x00000003AB400000-14.676 GB
EMMC CID : 90014A484147346132A52EEB687D660D - HAG4a2
HW-CODE : 0x717
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA01
SW-VERSION : 0x200
CHIP-EVOLUTION : 0x0
DA-VERSION : 1.0
Speed : high-speed
Upload data was accepted. Jumping to stage 2...
DA Extensions successfully added
Reading Partition Table ..
Partition Count : 44
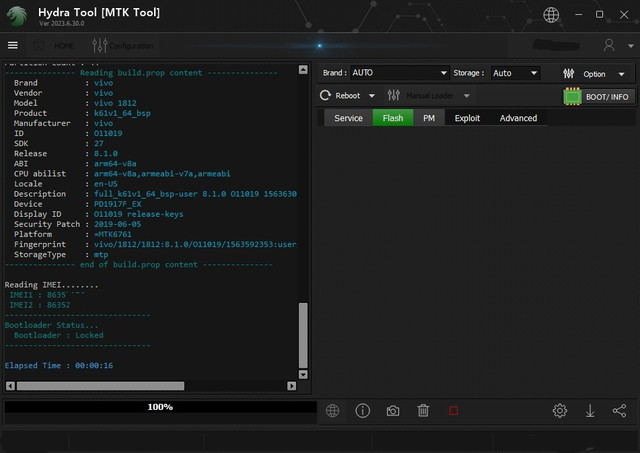
--------------- Reading build.prop content ---------------
Brand : vivo
Vendor : vivo
Model : vivo 1812
Product : k61v1_64_bsp
Manufacturer : vivo
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k61v1_64_bsp-user 8.1.0 O11019 1563630544 release-keys
Device : PD1917F_EX
Display ID : O11019 release-keys
Security Patch : 2019-06-05
Platform : =MTK6761
Fingerprint : vivo/1812/1812:8.1.0/O11019/1563592353:user/release-keys
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 86352***********
IMEI2 : 86352***********
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Elapsed Time : 00:00:16
- Select firmware and click execute
Code:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
MTK Flash Function...
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Searching for MTK Device...Found
MTK Port Type : Flashmode BROM
FriendlyName : MediaTek USB Port_V1633 (COM4)
Device : /6&37254210&0&4
SymbolicName : \\?\usb#vid_0e8d&pid_0003#6&37254210&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Service : wdm_usb
Openning Port [COM4] Ok
Reading Partition Table ..
ERAM Size : 0x000000000003A500-233.25 KB
IRAM Size : 0x0000000080000000-2 GB
EMMC Boot1 Size : 0x0000000000400000-4 MB
EMMC Boot2 Size : 0x0000000000400000-4 MB
EMMC RPMB Size : 0x0000000000400000-4 MB
EMMC USER Size : 0x00000003AB400000-14.676 GB
EMMC CID : 90014A484147346132A52EEB687D660D - HAG4a2
HW-CODE : 0x717
HWSUB-CODE : 0x8A00
HW-VERSION : 0xCA01
SW-VERSION : 0x200
CHIP-EVOLUTION : 0x0
DA-VERSION : 1.0
Speed : high-speed
Partition Count : 44
--------------- Reading build.prop content ---------------
Brand : vivo
Vendor : vivo
Model : vivo 1812
Product : k61v1_64_bsp
Manufacturer : vivo
ID : O11019
SDK : 27
Release : 8.1.0
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-US
Description : full_k61v1_64_bsp-user 8.1.0 O11019 1563630544 release-keys
Device : PD1917F_EX
Display ID : O11019 release-keys
Security Patch : 2019-06-05
Platform : =MTK6761
Fingerprint : vivo/1812/1812:8.1.0/O11019/1563592353:user/release-keys
StorageType : mtp
--------------- end of build.prop content ---------------
Reading IMEI........
IMEI1 : 86352*********
IMEI2 : 86352*********
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
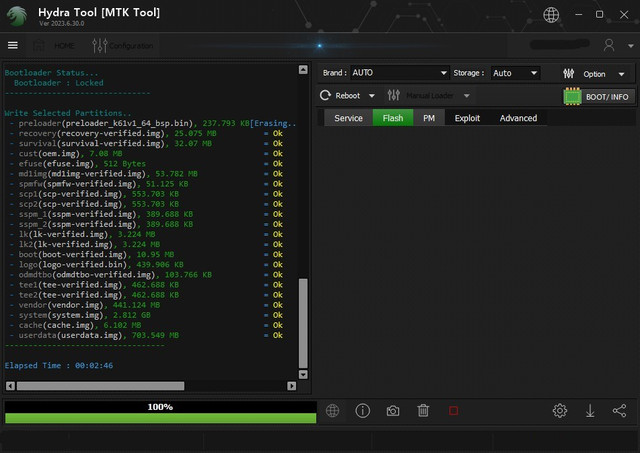
Write Selected Partitions..
- preloader(preloader_k61v1_64_bsp.bin), 237.793 KB[Erasing...Ok] Status :C0010001 Error= Failed
- recovery(recovery-verified.img), 25.075 MB = Ok
- survival(survival-verified.img), 32.07 MB = Ok
- cust(oem.img), 7.08 MB = Ok
- efuse(efuse.img), 512 Bytes = Ok
- md1img(md1img-verified.img), 53.782 MB = Ok
- spmfw(spmfw-verified.img), 51.125 KB = Ok
- scp1(scp-verified.img), 553.703 KB = Ok
- scp2(scp-verified.img), 553.703 KB = Ok
- sspm_1(sspm-verified.img), 389.688 KB = Ok
- sspm_2(sspm-verified.img), 389.688 = Ok
- lk(lk-verified.img), 3.224 MB = Ok
- lk2(lk-verified.img), 3.224 MB = Ok
- boot(boot-verified.img), 10.95 MB = Ok
- logo(logo-verified.bin), 439.906 KB = Ok
- odmdtbo(odmdtbo-verified.img), 103.766 KB = Ok
- tee1(tee-verified.img), 462.688 KB = Ok
- tee2(tee-verified.img), 462.688 KB = Ok
- vendor(vendor.img), 441.124 MB = Ok
- system(system.img), 2.812 GB = Ok
- cache(cache.img), 6.102 MB = Ok
- userdata(userdata.img), 703.549 MB = Ok
----------------------------------
Elapsed Time : 00:02:46


