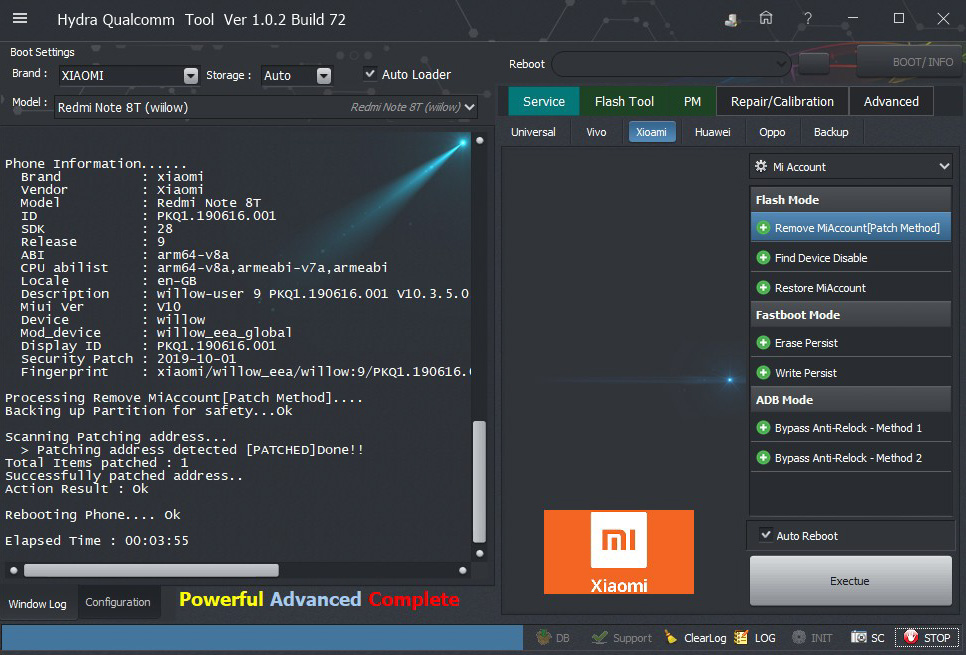
Xiaomi Redmi Note 8T (Willow) Mi Account Successfully Patched by Hydra Tool
Screen Short:
Logs:
Screen Short:
Logs:
BRPreOperation Configuration
Brand : XIAOMI Model : Redmi Note 8T (wiilow) Storage : Auto
Loader: Xiaomi_redminote8_loader.elf
Port : Auto
Connection :
Searching for Qualcomm 9008 Device...Found
FriendlyName :Qualcomm HS-USB QDLoader 9008 (COM11)
SymbolicName :\??\USB#VID_05C6&PID_9008#6&1192b386&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :08/02/2017,2.1.2.7
Getting device info......
Serial No.: 0xC1ED534C
MSM ID : 0x0010A0E1, SM6125-Qualcomm Snapdragon 665
PBL Ver : 00000000
PK HASH : 1BEBE3863A6781DB4B01086063007334
DE9E5CA14971C7C4F4358EC9D79CDA46
Firehose Loader[Xiaomi_redminote8_loader.elf]
SaharaBoot... Ok
Sending ..............................Ok
Connecting to Firehose...
Ping..................... Ok
Configuration.........
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes :
MaxXMLSizeInBytes : 4096
TargetName :
Version : 1
DateTime : Jul 3 2019 - 22:23:56
*** STORAGE DEVICE INFO ***
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 19
Serial Number : 402832172
Firmware Version : 4
Product Name : S0J9K8
Physical Partitions : 4
Total Logical Blocks:
Drive [0] 122142720[58.242 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Drive [3] 32768[16 MB]
Protocol : Universal
Running : Ok
Reading GPT[4]
Drive [0] 88 Items
Drive [1] 0 Items
Drive [2] 0 Items
Drive [3]
Phone Information......
Brand : xiaomi
Vendor : Xiaomi
Model : Redmi Note 8T
ID : PKQ1.190616.001
SDK : 28
Release : 9
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Locale : en-GB
Description : willow-user 9 PKQ1.190616.001 V10.3.5.0.PCXEUXM release-keys
Miui Ver : V10
Device : willow
Mod_device : willow_eea_global
Display ID : PKQ1.190616.001
Security Patch : 2019-10-01
Fingerprint : xiaomi/willow_eea/willow:9/PKQ1.190616.001/V10.3.5.0.PCXEUXM:user/release-keys
Processing Remove MiAccount[Patch Method]....
Backing up Partition for safety...Ok
Scanning Patching address...
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]
> Patching address detected [PATCHED]Done!!
Total Items patched : 3
Successfully patched address..
Action Result : Ok
Rebooting Phone.... Ok
Elapsed Time : 00:03:15
Mount Everest