★★★ Post All Successfully Repaired Phones By Hydra Tool ★★★
- Thread starter Hydra Tool
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Neeraj2020
Junior Member
Aminkhan
Active Member
hydra team help me with huawei qualcomm repair, ie dub-lx1, ldn-l21, which are supported for repair, while i am not able to do operation in main module.
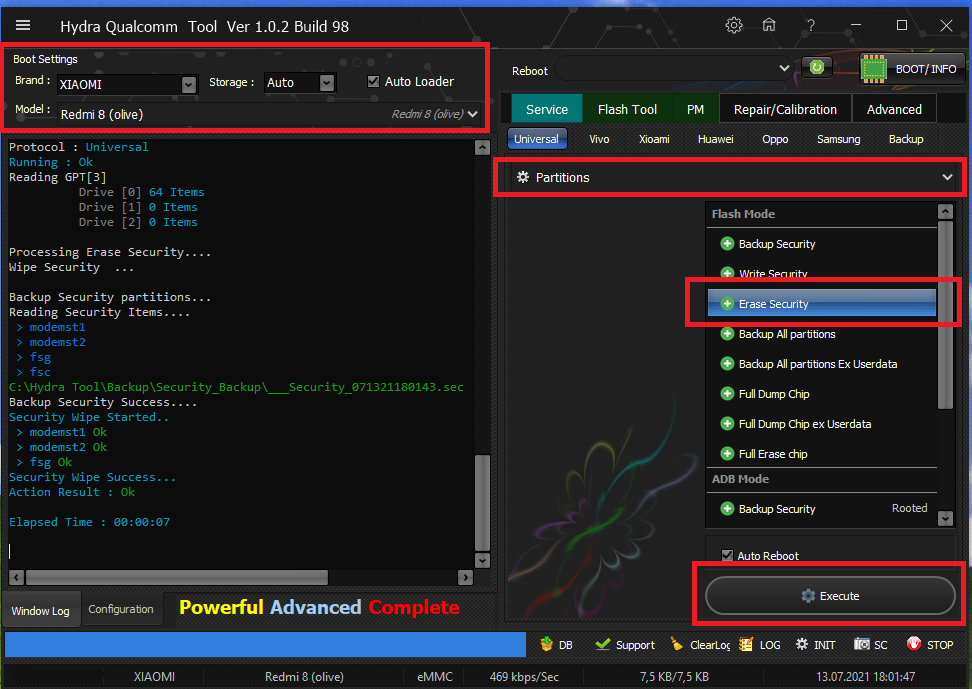
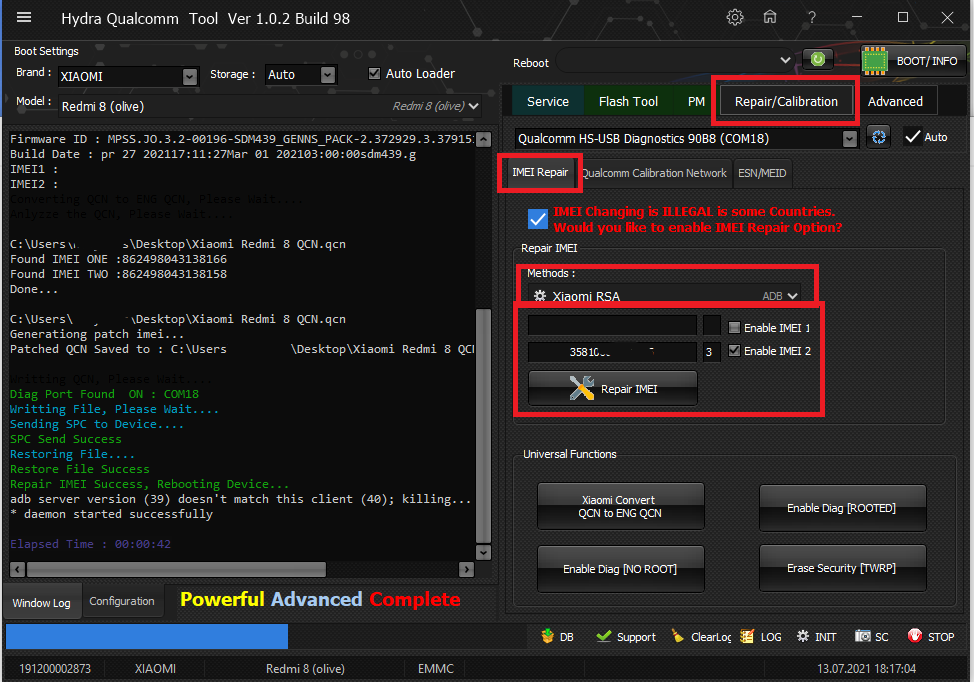
Xiaomi Redmi 8 olive IMEI Repair, All MIUI and Android versions are supported.
Without Unlock Bootloader
Without Root
Without Flash ENG ROM
Full Network with 4G
Note : Only 2nd imei supported this device.
Erase Security by EDL Mode :
Repair IMEI LOG :
Without Unlock Bootloader
Without Root
Without Flash ENG ROM
Full Network with 4G
- Run Qualcomm Module, Select Brand and Model
- Put your device EDL Mode by Testpoint
- From Service -> Partitions Tab Select Erase Security
- Power on device Enable Diag by Dial code *#*#717717#*#*
- Go to Repair Tab, Select Xiaomi RSA Method
- Fill IMEI 2 only and Repair
Note : Only 2nd imei supported this device.
Erase Security by EDL Mode :
Repair IMEI LOG :
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM54)
Device :7&31189216&0&4
SymbolicName :\??\USB#VID_0E8D&PID_0003#7&31189216&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :09/11/2014,3.0.1437.1
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0886MT6873 [6873]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting BROM...
Exploit Sent..
Successfully Exploited..
Reading Flash Init...
Flash init Size 0x0750
Security Authorization....
Sending Accepted
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0886MT6873 [6873]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 05
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 556B959C81EAE924F3D6B5871BF4966D
Stage 1..[Size:327816]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing preloader_oppo6873.bin
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BBDC77D666D754C9D3FA6C70A6F858CE
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM8V8001JM-B813
UFS UNIQID : 00340063003200620032006600620064
Executing : ACCEPTED...
Reading GPT-UFS [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader....
Creating Scatter file... C:\Hydra Tool\HydraTool_FullPackage_04-09-2021\\Backup\Auto\0886__080121191836\MT6873_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x11E08000]1024 KB ->frp.bin...Ok
-nvdata[0x15708000]64 MB ->nvdata.bin...Ok
-persist[0x1CDA2000]50.367 MB ->persist.bin...Ok
-protect1[0x20000000]8 MB ->protect1.bin...Ok
-protect2[0x20800000]8 MB ->protect2.bin...Ok
-nvram[0x24D00000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\HydraTool_FullPackage_04-09-2021\\Backup\Auto\0886__080121191836
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BBDC77D666D754C9D3FA6C70A6F858CE
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM8V8001JM-B813
UFS UNIQID : 00340063003200620032006600620064
Reading GPT-UFS [0x00008000] 130 Items
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Action Result : Ok
Elapsed Time : 00:00:49
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM54)
Device :7&31189216&0&4
SymbolicName :\??\USB#VID_0E8D&PID_0003#7&31189216&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :09/11/2014,3.0.1437.1
Handshaking...Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0886MT6873 [6873]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting BROM...
Exploit Sent..
Successfully Exploited..
Reading Flash Init...
Flash init Size 0x0750
Security Authorization....
Sending Accepted
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0886MT6873 [6873]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 05
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : 556B959C81EAE924F3D6B5871BF4966D
Stage 1..[Size:327816]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization...SYNC
Preloader Initialization...
Parsing preloader_oppo6873.bin
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BBDC77D666D754C9D3FA6C70A6F858CE
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM8V8001JM-B813
UFS UNIQID : 00340063003200620032006600620064
Executing : ACCEPTED...
Reading GPT-UFS [0x00008000] 130 Items
Autobackup Partitions
-preloader[0x00000000]512 KB ->preloader.bin...Ok
-> Renaming Preloader....
Creating Scatter file... C:\Hydra Tool\HydraTool_FullPackage_04-09-2021\\Backup\Auto\0886__080121191836\MT6873_Android_scatter.txt
-pgpt[0x00000000]32 KB ->pgpt.bin...Ok
-frp[0x11E08000]1024 KB ->frp.bin...Ok
-nvdata[0x15708000]64 MB ->nvdata.bin...Ok
-persist[0x1CDA2000]50.367 MB ->persist.bin...Ok
-protect1[0x20000000]8 MB ->protect1.bin...Ok
-protect2[0x20800000]8 MB ->protect2.bin...Ok
-nvram[0x24D00000]64 MB ->nvram.bin...Ok
Done!!!
C:\Hydra Tool\HydraTool_FullPackage_04-09-2021\\Backup\Auto\0886__080121191836
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BBDC77D666D754C9D3FA6C70A6F858CE
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
UFS LU0 Size: 0x0000000000400000 -4 MB
UFS LU1 Size: 0x0000000000400000 -4 MB
UFS LU2 Size: 0x0000001DCB000000 -119.172 GB
UFS CID : ÎKM8V8001JM-B813
UFS UNIQID : 00340063003200620032006600620064
Reading GPT-UFS [0x00008000] 130 Items
-------------------------------------
Operation : Auto
Processing...
ZeroWipe FRP Partition...
Action Result : Ok
Elapsed Time : 00:00:49
Varoxx
Active Member
- Nov 6, 2019
- 85
- 51
Redmi 9A dendelion Bootloader unlock Done for 3 seconds with Hydar Mtk 
=====================================
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM14)
Device :6&10c694e1&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&10c694e1&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : D20E9A4CCB738FC3D81F7F4F41FAB91B
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 450100444134303332013F47581337E7 - DA4032
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02

=====================================
Searching for MTK Device...Found
Port Identification :Flashmode BROM
FriendlyName :MediaTek USB Port (COM14)
Device :6&10c694e1&0&1
SymbolicName :\??\USB#VID_0E8D&PID_0003#6&10c694e1&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver :01/22/2015,3.0.1504.0
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : D20E9A4CCB738FC3D81F7F4F41FAB91B
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 450100444134303332013F47581337E7 - DA4032
Reading GPT-EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Rebooting Device [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:00:02
ismail2cnr
Member
- Sep 19, 2018
- 8
- 3
- Skype
- ismail2cnr
poco c3 frp+mi account done by hydra
Operation : Remove MiAccount[Erase Method]
Processing...
-persist.bin[0x47000000]48 MB ->persist.bin...Ok
-frp.bin[0x3BD88000]1024 KB ->frp.bin...Ok
Action Result : Ok
Elapsed Time : 00:01:05
Operation : Remove MiAccount[Erase Method]
Processing...
-persist.bin[0x47000000]48 MB ->persist.bin...Ok
-frp.bin[0x3BD88000]1024 KB ->frp.bin...Ok
Action Result : Ok
Elapsed Time : 00:01:05
ismail2cnr
Member
- Sep 19, 2018
- 8
- 3
- Skype
- ismail2cnr
Sir Did You Have Prog.firehouse. elf file for Rog 5 ..??
Xiaomi Redmi Note 8 Pro Bootloader Unlock Instant by Hydra
without wait 7 days
Quote:
without wait 7 days
Quote:
| ===================================== Searching for MTK Device... Found Port Identification : Flashmode BROM FriendlyName : MediaTek USB Port (COM6) Device : 5&356b5377&0&10 SymbolicName :??USB#VID_0E8D&PID_0003#5&356b5377&0&10#{a5dcbf10-6530-11d2-901f-00c04fb951ed} Driver Ver : 01/22/2015,3.0.1504.0 Opened handle.. Handshaking... Ok Identifying Hardware ID..... Reading Device hardware info.. hw code : 0813 MT6785 [6785] hw subcode : 8A00 hw version : CA00 sw version : 0000 Target config : E7 SBC : 01 (True) SLA : 02 (True) DAA : 04 (True) SWJTAG : 06 (True) EPP : 00 (False) CERT : 00 (False) MEMREAD : 20 (True) MEMWRITE : 40 (True) CMD_C8 : 80 (True) Exploiting Device... Exploit Sent.. Successfully Exploited... Handshaking... Ok C:Hydra ToolBackupPreloader_dumpprel.tmp Handshaking... Identifying Hardware ID..... Reading Device hardware info.. hw code : 0813 MT6785 [6785] hw subcode : 8A00 hw version : CA00 sw version : 0000 Target config : 00 SBC : 00 (False) SLA : 00 (False) DAA : 00 (False) SWJTAG : 00 (False) EPP : 00 (False) CERT : 00 (False) MEMREAD : 00 (False) MEMWRITE : 00 (False) CMD_C8 : 00 (False) MEID : 15C3C23BC7CA0998FBF572DEB128FB1B Stage 1.. [Size:234968] Sending : Please wait.. Accepted Identifying Protocol... Protocol : New Synchronization... SYNC Preloader Initialization... sing prel.tmp Init : Accepted Executing : SYNC Reading Device UniqueID, RAM and Flash Chip Info... UNIQUE ID : FD4ED100FB65182DBB9E95F257E45019 ERAM Size : 0x0000000000080000 -512 KB IRAM Size : 0x0000000180000000 -6 GB UFS LU0 Size: 0x0000000000400000 -4 MB UFS LU1 Size: 0x0000000000400000 -4 MB UFS LU2 Size: 0x0000000EE5800000 -59.586 GB UFS CID : -'01H9HQ53AECMMDAR UFS UNIQID : 0d9898607b46000000000000 Executing : ACCEPTED... Reading GPT0 -UFS [0x00008000] 0 130 Items Reading System Info Vendor : Xiaomi ID : QP1A.190711.020 SDK : 29 Release : 10 ABI : arm64-v8a CPU abilist : arm64-v8a,armeabi-v7a,armeabi Locale : en-GB Description : begonia-user 10 QP1A.190711.020 V12.0.4.0.QGGIDXM release-keys Miui Ver : V12 Mod_device : begonia_id_global Display ID : QP1A.190711.020 Security Patch : 2021-01-01 StorageType : mtp Userdata State : Not Encrypted Autobackup titions -preloader [0x00000000] 512 KB -> preloader.bin... Ok0 -> Renaming Preloader.... preloader_begonia.bin0 Creating Scatter file... C:Hydra ToolBackupAuto0813__100821113946MT6785_Android_sca tter.txt -pgpt [0x00000000] 32 KB -> pgpt.bin... Ok -frp [0x05888000] 1024 KB -> frp.bin... Ok -nvdata [0x08188000] 64 MB -> nvdata.bin... Ok -persist [0x0E188000] 70.469 MB -> persist.bin... Ok -protect1 [0x12800000] 8 MB -> protect1.bin... Ok -protect2 [0x13000000] 8 MB -> protect2.bin... Ok -nvram [0x17580000] 64 MB -> nvram.bin... Ok Done!!!0 C:Hydra ToolBackupAuto0813__100821113946 MTK Phone Loader is NOW RUNNING. Reading Device UniqueID, RAM and Flash Chip Info... UNIQUE ID : 1 FD4ED100FB65182DBB9E95F257E45019 ERAM Size : 1 0x0000000000080000 -512 KB IRAM Size : 1 0x0000000180000000 -6 GB UFS LU0 Size: 0x0000000000400000 -4 MB UFS LU1 Size: 0x0000000000400000 -4 MB UFS LU2 Size: 0x0000000EE5800000 -59.586 GB UFS CID : -'01H9HQ53AECMMDAR UFS UNIQID : 0d9898607b46000000000000 Reading GPT0 -UFS [0x00008000] 0 130 Items Reading System Info Vendor : Xiaomi ID : QP1A.190711.020 SDK : 29 Release : 10 ABI : arm64-v8a CPU abilist : arm64-v8a,armeabi-v7a,armeabi Locale : en-GB Description : begonia-user 10 QP1A.190711.020 V12.0.4.0.QGGIDXM release-keys Miui Ver : V12 Mod_device : begonia_id_global Display ID : QP1A.190711.020 Security Patch : 2021-01-01 StorageType : mtp Userdata State : Not Encrypted ------------------------------------- Operation : Unlock Bootloader Processing... ------------------------------- Bootloader Status... Bootloader : Locked ------------------------------- Verifying status after operation... ------------------------------- Bootloader Status... Bootloader : Unlocked ------------------------------- Action Result :Ok Elapsed Time : 00:00:40 |
Xioami Redmi Note 8 2021 Unlock Bootloader With by Hydra
Quote:
Quote:
| ===================================== Searching for MTK Device... Found Port Identification : Flashmode BROM FriendlyName : MediaTek USB Port (COM4) Device : 5&37162be&0&1 SymbolicName :??USB#VID_0E8D&PID_0003#5&37162be&0&1#{a5dcbf10-6530-11d2-901f-00c04fb951ed} Driver Ver : 01/22/2016,3.2 Opened handle.. Reading Device UniqueID, RAM and Flash Chip Info... UNIQUE ID : 61A93080CE107849145F8EB80869F2FC ERAM Size : 0x0000000000070000 -448 KB IRAM Size : 0x0000000100000000 -4 GB eMMC BOOT1 : 0x0000000000400000 -4 MB eMMC BOOT2 : 0x0000000000400000 -4 MB eMMC RPMB : 0x0000000001000000 -16 MB eMMC USER : 0x0000000E8F800000 -58,242 GB eMMC CID : 90014A68433861503E0310060CD6B779 - hC8aP> Reading GPT -EMMC [0x00008000] 130 Items ------------------------------------- Operation : Unlock Bootloader Processing... ------------------------------- Bootloader Status... Bootloader : Locked ------------------------------- Verifying status after operation... ------------------------------- Bootloader Status... Bootloader : Unlocked ------------------------------- Action Result : Ok Elapsed Time : 00:00:03 |
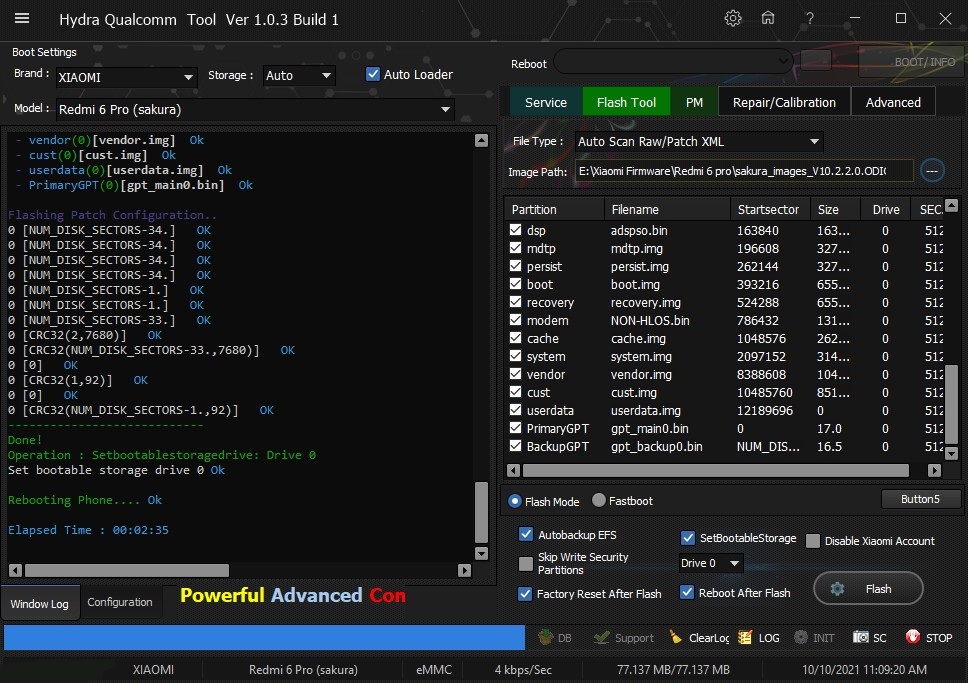
Xioami Redmi 6 Edl Flashıng With by Hydra
Quote:
Quote:
| Searching for Qualcomm 9008 Device... Found FriendlyName : Qualcomm HS-USB QDLoader 9008 (COM110) SymbolicName :??USB#VID_05C6&PID_9008#6&27800d7b&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed} Driver Ver : 08/02/2017,2.1.2.7 Getting device info .. . ... Serial No.: 0xD599C1D5 HW_ID : 000460E100000000 MSM ID : 0x000460E1, MSM8953-Qualcomm Snapdragon 625 MODEL_ID : 0x0000 OEM_ID : 0x0000 - QUALCOMM PBL Ver : 00000002 PK HASH : 57158eaf1814d78fd2b3105ece4db18a817a08ac664a5782a9 25f3ff8403d39a Firehose Loader [Xiaomi_Remi 6 pro_******_8953_ddr.mbn] -------------------------------------------------- Header Type : OLD TargetMSM : 8953 Tag : _auth_peek Version : 3 Code_size : 288 Signature_size : 256 fhVendor : XIAOMI HW_ID : 000460E100000000 Vendor : QUALCOMM OEM_ID : 0000 MODEL_ID : 0000 SW_ID : 0000000200000003 APP_ID : pk_hash : 57158eaf1814d78fd2b3105ece4db18a817a08ac664a5782a9 25f3ff8403d39a OEM_VERSION : c3-bsp-builder-job002.bj IMAGE_VARIANT : JAADANAZA QC_VERSION : BOOT.BF.3.3-00228 -------------------------------------------------- SaharaBoot... Ok Sending ....................b Okb0 Connecting to Firehose... Ping ... Ok Configuration. Xiaomi Authentication needed... Signature Request -> bob[BX0rp42lF0fZ7vuQQDljIsuP2cJ] Signature @256bytes Authentication.... Accepted ...... Identifying Chip.... Ok Chip Configuration : MemoryName : eMMC MaxPayloadSizeToTargetInBytes : 1048576 MaxPayloadSizeToTargetInBytesSupported : 1048576 MaxPayloadSizeFromTargetInBytes : 4096 MaxXMLSizeInBytes : 4096 TargetName : 8953 Version : 1 *** STORAGE DEVICE INFO *** Memory Type : eMMC Block Size in Bytes : 512 Page Size : 512 Manufacturer ID : 144 Serial Number : 3281161589 Firmware Version : 162 Product Name : HCG8a4 Physical titions : 3 Total Logical Blocks: Drive [0] 122142720 [58.242 GB] Drive [1] 8192 [4 MB] Drive [2] 8192 [4 MB] Protocol : Universal Running : Ok Phone Information ..... Brand : xiaomi Vendor : Xiaomi Model : Redmi 6 Pro ID : PKQ1.180917.001 SDK : 28 Release : 9 ABI : arm64-v8a CPU abilist : arm64-v8a,armeabi-v7a,armeabi Locale : zh-CN Description : ******-user 9 PKQ1.180917.001 V12.0.1.0.PDICNXM release-keys Miui Ver : V12 Device : ****** Display ID : ZQL1715-******-build-20200728120204 Security Patch : 2020-07-01 Emmc_size : 16GB Fingerprint : xiaomi/******/******:9/PKQ1.180917.001/V12.0.1.0.PDICNXM:user/release-keys Reading GPT[3] Drive [0] 60 Items Drive [1] 0 Items Drive [2] 0 Items Backup Security titions... Reading Security Items.... > modemst1 > modemst2 > fsg > fsc C:UsersThiha MobileDesktopHydraTool_Fullpackage_05-16-2021_ps_hydratoolBackupSecurity_BackupRedmi 6 Pro__9_Security_101021110652.sec Backup Security Success.... ---------------------------- Flashing Selected titions.... - sec (0)b [sec.dat] b0 Ok - config (0)b [config.bin] b0 Ok - lksecapp (0)b [lksecapp.mbn] b0 Ok - lksecappbak (0)b [lksecapp.mbn] b0 Ok - devcfg (0)b [devcfg.mbn] b0 Ok - devcfgbak (0)b [devcfg.mbn] b0 Ok - apdp (0)b [dummy.img] b0 Ok - msadp (0)b [dummy.img] b0 Ok - sbl1 (0)b [sbl1.mbn] b0 Ok - sbl1bak (0)b [sbl1.mbn] b0 Ok - rpm (0)b [rpm.mbn] b0 Ok - rpmbak (0)b [rpm.mbn] b0 Ok - cmnlib (0)b [cmnlib_30.mbn] b0 Ok - cmnlibbak (0)b [cmnlib_30.mbn] b0 Ok - cmnlib64 (0)b [cmnlib64_30.mbn] b0 Ok - cmnlib64bak (0)b [cmnlib64_30.mbn] b0 Ok - keymaster (0)b [keymaster64.mbn] b0 Ok - keymasterbak (0)b [keymaster64.mbn] b0 Ok - misc (0)b [misc.img] b0 Ok - aboot (0)b [emmc_appsboot.mbn] b0 Ok - abootbak (0)b [emmc_appsboot.mbn] b0 Ok - tz (0)b [tz.mbn] b0 Ok - tzbak (0)b [tz.mbn] b0 Ok - splash (0)b [splash.img] b0 Ok - dsp (0)b [adspso.bin] b0 Ok - mdtp (0)b [mdtp.img] b0 Ok - persist (0)b [persist.img] b0 Ok - boot (0)b [boot.img] b0 Ok - recovery (0)b [recovery.img] b0 Ok - modem (0)b [NON-HLOS.bin] b0 Ok - cache (0)b [cache.img] b0 Ok - system (0)b [system.img] b0 Ok - vendor (0)b [vendor.img] b0 Ok - cust (0)b [cust.img] b0 Ok - userdata (0)b [userdata.img] b0 Ok - PrimaryGPT (0)b [gpt_main0.bin] b0 Ok Flashing Patch Configuration.. 0 [NUM_DISK_SECTORS-34.] OK 0 [NUM_DISK_SECTORS-34.] OK 0 [NUM_DISK_SECTORS-34.] OK 0 [NUM_DISK_SECTORS-34.] OK 0 [NUM_DISK_SECTORS-1.] OK 0 [NUM_DISK_SECTORS-1.] OK 0 [NUM_DISK_SECTORS-33.] OK 0 [CRC32(2,7680)] OK 0 [CRC32(NUM_DISK_SECTORS-33.,7680)] OK 0 [0] OK 0 [CRC32(1,92)] OK 0 [0] OK 0 [CRC32(NUM_DISK_SECTORS-1.,92)] OK ---------------------------- Done! Operation : Setbootablestoragedrive: Drive 0 Set bootable storage drive 0 Ok Rebooting Phone.... Ok Elapsed Time : 00:02:35 |
Huawei Y6P (MED-LX9) Remove Account With by Hydra
=====================================
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port_V1632 (COM35)
Device : 5&388db30c&0&2
SymbolicName :??USB#VID_0E8D&PID_0003#5&388db30c&0&2#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Handshaking... Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766 MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E5
SBC : 01 (True)
SLA : 00 (False)
DAA : 04 (True)
SWJTAG : 04 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking... Ok
C:Hydra ToolBackupPreloader_dumpprel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0766 MT6765 [6765]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : AD4FA940A7CC82CAC9F4E5B8BE8FEE05
Stage 1.. [Size:216440]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization... [ERROR]- NOT SYNC
=============================================
Reasons why it fails due to the following"
1. Harware problem/issues
2. If you did Testpoint Kindly check the ts you Touch/TP
3. Powershortage, try to connect Battery
4. Check or replace usb cable and plug directly to your pc usb port.
=============================================
SYNC
Preloader Initialization...
sing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 89CCE42A703A08E60F8BD51D1183A49C
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 90014A68433961503301008819208727 - hC9aP3
Executing : ACCEPTED...
Reading GPT0 -EMMC [0x00008000] 0 130 Items
0
Autobackup titions
-preloader [0x00000000] 512 KB -> preloader.bin...1 Ok0
-> Renaming Preloader.... preloader_k62v1_64_mex_a32.bin0
Creating Scatter file... C:Hydra ToolBackupAuto0766__101021104722MT6765_Android_scatter.txt
-pgpt [0x00000000] 32 KB -> pgpt.bin...1 Ok
-frp [0x00108000] 1024 KB -> frp.bin...1 Ok
-nvdata [0x00A08000] 16 MB -> nvdata.bin...1 Ok
-protect1 [0x01A08000] 8 MB -> protect1.bin...1 Ok
-protect2 [0x02208000] 13.969 MB -> protect2.bin...1 Ok
-persist [0x03800000] 8 MB -> persist.bin...1 Ok
-nvram [0x04400000] 5 MB -> nvram.bin...1 Ok
-oeminfo [0x04900000] 32 MB -> oeminfo.bin...1 Ok
Done!!!0
C:Hydra ToolBackupAuto0766__101021104722
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 2 89CCE42A703A08E60F8BD51D1183A49C
ERAM Size : 2 0x0000000000038000 -224 KB
IRAM Size : 2 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 90014A68433961503301008819208727 - hC9aP3
Reading GPT0 -EMMC [0x00008000] 0 130 Items
-------------------------------------
Operation : Remove Account
Processing...
Backing up tition for safety...
-oeminfo_101021104734.bin [0x04900000] 32 MB -> oeminfo_101021104734.bin...1 Ok
Action Result : 0 Ok
Rebooting Device 0 [Reboot To Normal]
Reboot Done!!
Elapsed Time : 00:01:41
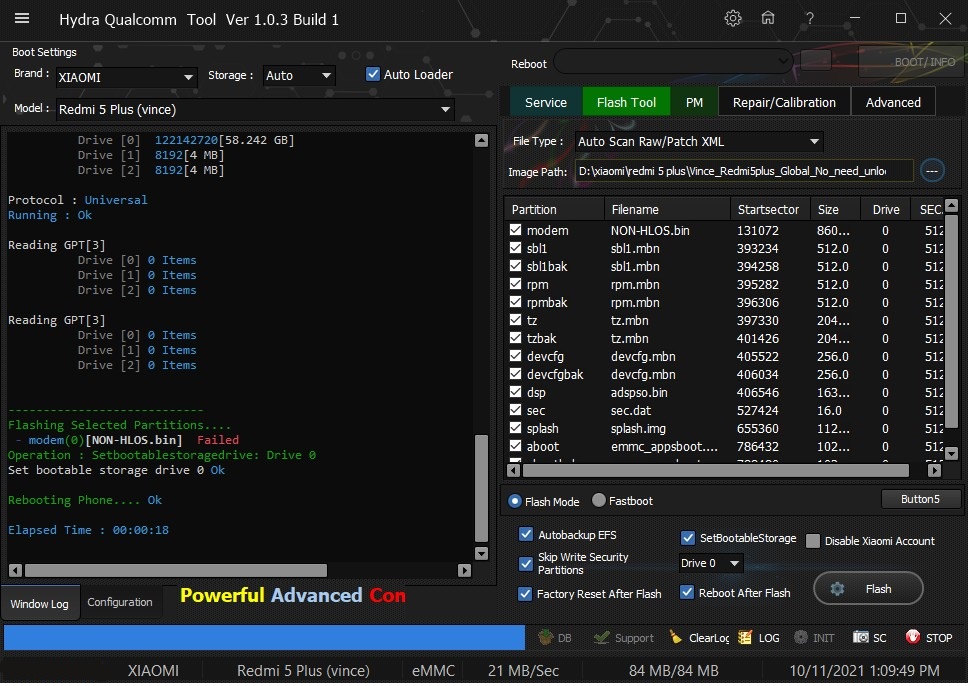
Xioami Redmi 5 Plus (Vince) Edl Flash With by Hydra
Quote:
Quote:
| Searching for Qualcomm 9008 Device... Found FriendlyName : Qualcomm HS-USB QDLoader 9008 (COM26) SymbolicName :??USB#VID_05C6&PID_9008#5&2956bf20&0&3#{a5dcbf10-6530-11d2-901f-00c04fb951ed} Driver Ver : 02/05/2018,3.0.0.0 Getting device info .. . ... Serial No.: 0x3F11B7B0 HW_ID : 000460E100000000 MSM ID : 0x000460E1, MSM8953-Qualcomm Snapdragon 625 MODEL_ID : 0x0000 OEM_ID : 0x0000 - QUALCOMM PBL Ver : 00000000 PK HASH : 57158eaf1814d78fd2b3105ece4db18a817a08ac664a5782a9 25f3ff8403d39a Firehose Loader [mi_3_1.mbn] -------------------------------------------------- Header Type : OLD TargetMSM : 8953 Tag : _peek Version : 3 Code_size : 288 Signature_size : 256 fhVendor : XIAOMI HW_ID : 000460E100000000 Vendor : QUALCOMM OEM_ID : 0000 MODEL_ID : 0000 SW_ID : 0000000000000003 APP_ID : pk_hash : 57158eaf1814d78fd2b3105ece4db18a817a08ac664a5782a9 25f3ff8403d39a OEM_VERSION : c3-bsp-builder-job001.bj IMAGE_VARIANT : JAADANAZA QC_VERSION : BOOT.BF.3.3-00221 -------------------------------------------------- SaharaBoot... Ok Sending ..................b Okb0 Connecting to Firehose... Ping ... Ok Configuration...... Identifying Chip.... Ok Chip Configuration : MemoryName : eMMC MaxPayloadSizeToTargetInBytes : 1048576 MaxPayloadSizeToTargetInBytesSupported : 1048576 MaxPayloadSizeFromTargetInBytes : 4096 MaxXMLSizeInBytes : 4096 TargetName : 8953 Version : 1 *** STORAGE DEVICE INFO *** Memory Type : eMMC Block Size in Bytes : 512 Page Size : 512 Manufacturer ID : 144 Serial Number : 877091852 Firmware Version : 162 Product Name : HCG8a4 Physical titions : 3 Total Logical Blocks: Drive [0] 122142720 [58.242 GB] Drive [1] 8192 [4 MB] Drive [2] 8192 [4 MB] Protocol : Universal Running : Ok Reading GPT[3] Drive [0] 0 Items Drive [1] 0 Items Drive [2] 0 Items Reading GPT[3] Drive [0] 0 Items Drive [1] 0 Items Drive [2] 0 Items ---------------------------- Flashing Selected titions.... - modem (0)b [NON-HLOS.bin] 0b0 Failed Operation : Setbootablestoragedrive: Drive 0 Set bootable storage drive 0 Ok Rebooting Phone.... Ok Elapsed Time : 00:00:18 |
Xioami Redmi Note 9 (Merlin) Bootloader Unlock With by Hydra
=====================================
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port_V1633 (COM3)
Device : 6&6aaf50d&0&4
SymbolicName :??USB#VID_0E8D&PID_0003#6&6aaf50d&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Handshaking... Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707 MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking... Ok
C:Hydra ToolBackupPreloader_dumpprel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707 MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : E7E928F47DDFF925D9334FE7A5186E53
Stage 1.. [Size:256504]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization... SYNC
Preloader Initialization...
sing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BE2A97BBFF84596B740241C1866A268E
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000001D1F000000 -116,484 GB
eMMC CID : 13014E47314A395339100853CA6C7765 - G1J9S9
Executing : ACCEPTED...
Reading GPT -EMMC [0x00008000] 130 Items
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 0 BE2A97BBFF84596B740241C1866A268E
ERAM Size : 0 0x0000000000070000 -448 KB
IRAM Size : 0 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000001D1F000000 -116,484 GB
eMMC CID : 13014E47314A395339100853CA6C7765 - G1J9S9
Reading GPT -EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Elapsed Time : 00:00:34
=====================================
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port_V1633 (COM3)
Device : 6&6aaf50d&0&4
SymbolicName :??USB#VID_0E8D&PID_0003#6&6aaf50d&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Handshaking... Ok
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707 MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : E7
SBC : 01 (True)
SLA : 02 (True)
DAA : 04 (True)
SWJTAG : 06 (True)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 20 (True)
MEMWRITE : 40 (True)
CMD_C8 : 80 (True)
Exploiting Device...
Exploit Sent..
Successfully Exploited...
Handshaking... Ok
C:Hydra ToolBackupPreloader_dumpprel.tmp
Handshaking...
Identifying Hardware ID.....
Reading Device hardware info..
hw code : 0707 MT6768 [6768]
hw subcode : 8A00
hw version : CA00
sw version : 0000
Target config : 00
SBC : 00 (False)
SLA : 00 (False)
DAA : 00 (False)
SWJTAG : 00 (False)
EPP : 00 (False)
CERT : 00 (False)
MEMREAD : 00 (False)
MEMWRITE : 00 (False)
CMD_C8 : 00 (False)
MEID : E7E928F47DDFF925D9334FE7A5186E53
Stage 1.. [Size:256504]
Sending : Please wait.. Accepted
Identifying Protocol...
Protocol : New
Synchronization... SYNC
Preloader Initialization...
sing prel.tmp
Init : Accepted
Executing : SYNC
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : BE2A97BBFF84596B740241C1866A268E
ERAM Size : 0x0000000000070000 -448 KB
IRAM Size : 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000001D1F000000 -116,484 GB
eMMC CID : 13014E47314A395339100853CA6C7765 - G1J9S9
Executing : ACCEPTED...
Reading GPT -EMMC [0x00008000] 130 Items
MTK Phone Loader is NOW RUNNING.
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 0 BE2A97BBFF84596B740241C1866A268E
ERAM Size : 0 0x0000000000070000 -448 KB
IRAM Size : 0 0x0000000100000000 -4 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000001000000 -16 MB
eMMC USER : 0x0000001D1F000000 -116,484 GB
eMMC CID : 13014E47314A395339100853CA6C7765 - G1J9S9
Reading GPT -EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Elapsed Time : 00:00:34
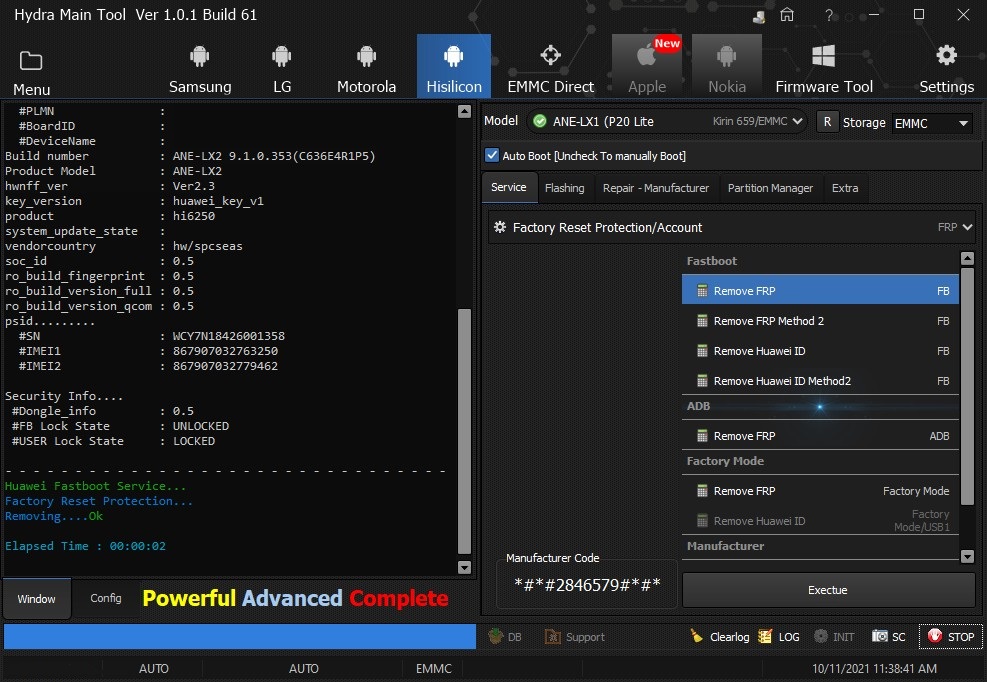
Huawei P20 Lite (ANE-LX1) Frp Remove With by Hydra
Quote:
Quote:
| Searching Device By Fastboot Device Found... - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Reading Device Information... - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - hotainfo...... #hotainfo_len : #C_version : #D_version : #PLMN : #BoardID : #DeviceName : Build number : ANE-LX2 9.1.0.353(C636E4R1P5) Product Model : ANE-LX2 hwnff_ver : Ver2.3 key_version : huawei_key_v1 product : hi6250 system_update_state : vendorcountry : hw/spcseas soc_id : 0.5 ro_build_fingerprint : 0.5 ro_build_version_full : 0.5 ro_build_version_qcom : 0.5 psid......... #SN : WCY7N18426001358 #IMEI1 : 867************ #IMEI2 : 867************ Security Info.... #Dongle_info : 0.5 #FB Lock State : UNLOCKED #USER Lock State : LOCKED - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Huawei Fastboot Service... Factory Reset Protection... Removing.... Ok Elapsed Time : 00:00:02 |
Oppo F1 Plus Read Screen Security With by Hydra
=====================================
Searching for MTK Device... Found
Port Identification : DA_HIGHSPEED_VCOM
FriendlyName : MediaTek DA USB VCOM (Android) (COM68)
Device : 6&2550cee7&0&4
SymbolicName :??USB#VID_0E8D&PID_2001#6&2550cee7&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : E49E7326A020745C2E9CC406613AF5BC
ERAM Size : 0x0000000000040000 -256 KB
IRAM Size : 0x0000000080000000 -2 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000747C00000 -29.121 GB
eMMC CID : 90014A484247346132A434F2E8337393 - HBG4a2
Reading GPT -EMMC [0x00008000] 130 Items
Reading System Info
Brand : OPPO
Vendor : OPPO
Model : A1601
ID : LMY47I
SDK : 22
Release : 5.1
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Description : full_oppo6750_15331-user 5.1 LMY47I 1502723706 release-keys
Device : A1601
Board : full_oppo6750_15331
Display ID : A1601EX_11_A.33_170814
Security Patch : 2017-08-05
Platform : mt6750
FRPPST : /dev/block/platform/mtk-msdc.0/by-name/frp
StorageType : mtp,mass_storage
Userdata State : Not Encrypted
-------------------------------------
Operation : Read Pattern
Processing...
Searching PatternKey : .0 Found
Gesture Data : C8C0B24A15DC8BBFD411427973574695230458F0
Bruteforcing pattern hash..Please wait for few seconds
Pattern Code : 14789
1 2 3
4 5 6
7 8 9
Action Result : Ok
Elapsed Time : 00:00:03
Oppo A37F (neo9) Remove Frp With by Hydra
Brand : OPPO Model : A37F (Neo 9) Storage : Auto
Loader: 8916.mbn
Port : Auto
Searching for Qualcomm 9008 Device... Found
FriendlyName : Qualcomm HS-USB QDLoader 9008 (COM3)
SymbolicName :??USB#VID_05C6&PID_9008#5&32474d1b&0&4#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 07/08/2015,2.1.2.0
Getting device info . . ...
Serial No.: 0x25A464D4
HW_ID : 007050E100000000
MSM ID : 0x007050E1, MSM8916-Qualcomm Snapdragon 410
MODEL_ID : 0x0000
OEM_ID : 0x0000 - QUALCOMM
PBL Ver : 00000000
PK HASH : cc3153a80293939b90d02d3bf8b23e0292e452fef662c74998421adad42a380f
Firehose Loader [8916.mbn]
--------------------------------------------------
Header Type : OLD
TargetMSM : 8916
Tag : _peek
Version : 3
Code_size : 96
Signature_size : 256
fhVendor : LENOVO
HW_ID : 007050E100000000
Vendor : QUALCOMM
OEM_ID : 0000
MODEL_ID : 0000
SW_ID : 0000000000000003
APP_ID :
pk_hash : 99c8c13e374c34d8f9afb065ea4c733e6b1b21cbc5a78705f041eb24acdd5fe5
OEM_VERSION :
IMAGE_VARIANT :
QC_VERSION :
--------------------------------------------------
SaharaBoot... Ok
Sending .....b Okb0
Connecting to Firehose...
Ping ... Ok
Configuration.......
Identifying Chip....
Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes : 4096
MaxXMLSizeInBytes : 4096
TargetName : 8916
Version : 1
Protocol : Universal
Running : Ok
Phone Information .....
Brand : OPPO
Vendor : OPPO
Model : A37f
ID : LMY47V
SDK : 22
Release : 5.1.1
ABI : arm64-v8a
CPU abilist : arm64-v8a,armeabi-v7a,armeabi
Description : msm8916_64-user 5.1.1 LMY47V eng.root.20180817.014458 release-keys
Board : msm8916
Display ID : A37fEX_11_180817
Security Patch : 2018-03-01
Platform : msm8916
FRPPST : /dev/block/bootdevice/by-name/config
Reading GPT[3]
Drive [0] 40 Items
Drive [1] 0 Items
Drive [2] 4 Items
Removing FRPta...
Method : 0
Auto
Processing...
- Removing FRP
Executing ...
- Removing FRP [Zero Wipe] OkOk Ok
Rebooting Phone.... Ok
If not rebooted, Please Power on Manually
Elapsed Time : 00:00:07
Redmi 9C (angelica) Unlock Bootloader With by Hydra
=====================================
Searching for MTK Device... Found
Port Identification : Flashmode BROM
FriendlyName : MediaTek USB Port (COM26)
Device : 5&6f73c6d&0&3
SymbolicName :??USB#VID_0E8D&PID_0003#5&6f73c6d&0&3#{a5dcbf10-6530-11d2-901f-00c04fb951ed}
Driver Ver : 01/22/2015,3.0.1504.0
Opened handle..
Reading Device UniqueID, RAM and Flash Chip Info...
UNIQUE ID : 8204F711E2EBC59A9FBA5720D554F508
ERAM Size : 0x0000000000038000 -224 KB
IRAM Size : 0x00000000C0000000 -3 GB
eMMC BOOT1 : 0x0000000000400000 -4 MB
eMMC BOOT2 : 0x0000000000400000 -4 MB
eMMC RPMB : 0x0000000000400000 -4 MB
eMMC USER : 0x0000000E8F800000 -58.242 GB
eMMC CID : 150100434A54443452041C564C24976F - CJTD4R
Reading GPT -EMMC [0x00008000] 130 Items
-------------------------------------
Operation : Unlock Bootloader
Processing...
-------------------------------
Bootloader Status...
Bootloader : Locked
-------------------------------
Verifying status after operation...
-------------------------------
Bootloader Status...
Bootloader : Unlocked
-------------------------------
Action Result : Ok
Elapsed Time : 00:00:03
nauman jan
Active Member
Hello Team Hydra Tools Please Give Me The Solution What Is Issue I Am Repair Imei Number For Huawei But Showing This Error Please Solve My Problem..