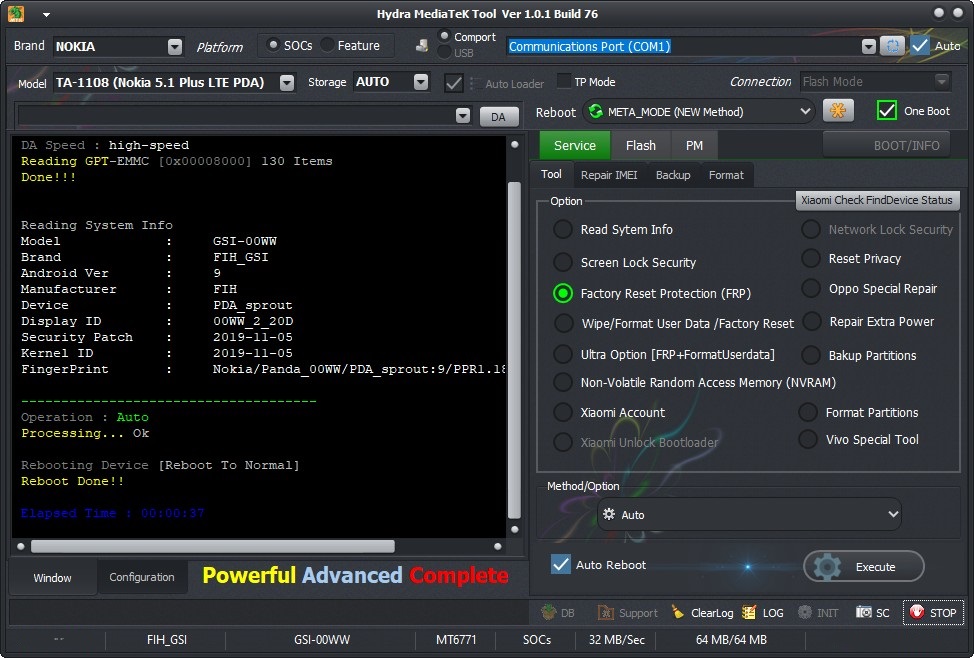
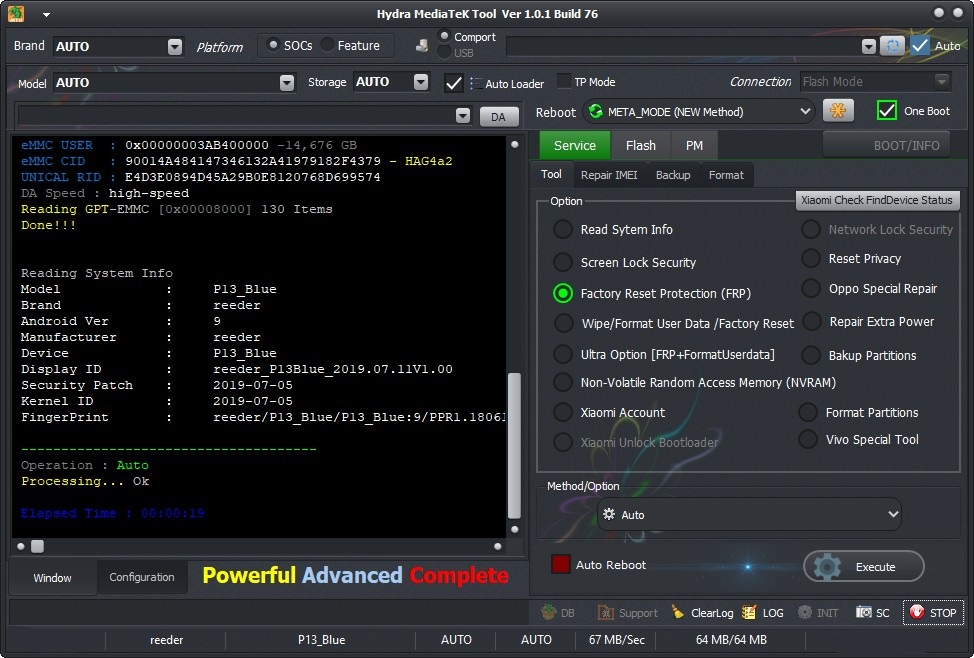
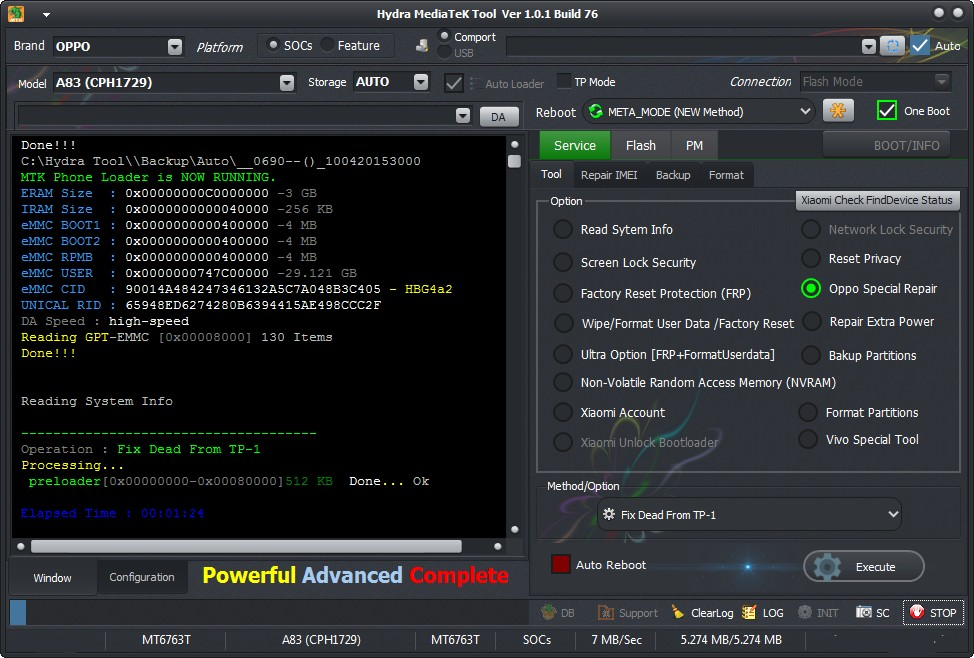
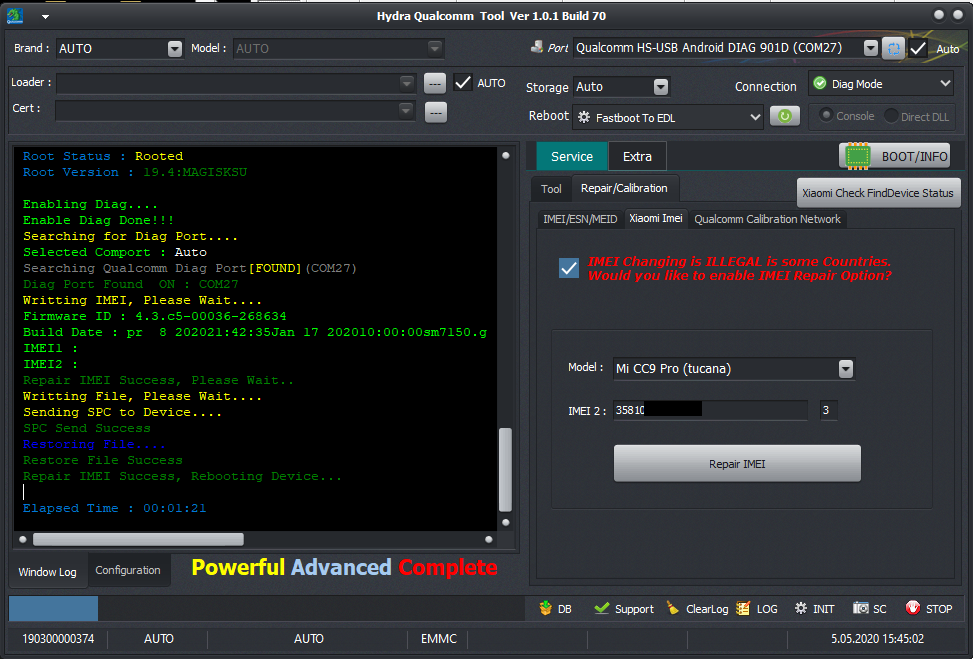
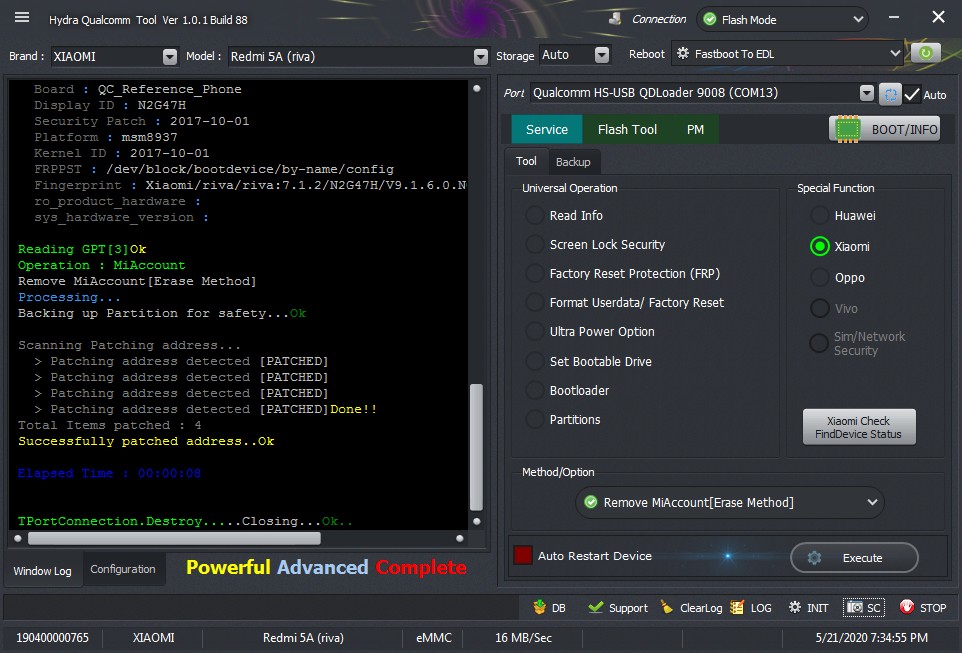
17:39:46 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:39:46 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:39:46 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:39:46 : Intel(R) HD Graphics 630
17:39:46 : Ram Installed :
17:39:46 : 3 GB
17:39:46 : Windows Access Right
17:39:46 : Admin
17:39:46 :
17:39:46 :
17:39:47 : ******* Dongle Info *******
17:39:47 : Version :
17:39:47 : Hydra Tool v 1.1
17:39:47 : Serial :
17:39:47 : 190400000765
17:39:47 : Initialize :
17:39:47 : OKAY
17:39:47 : Status :
17:39:47 : Activated
17:39:47 : Life :
17:39:47 : 0-
17:39:47 : [3-
17:39:47 : 0-
17:39:48 : 0-
17:39:48 : 0-
17:39:48 : 0]
17:39:48 :
17:39:58 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:39:58 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:39:58 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:39:58 : Intel(R) HD Graphics 630
17:39:58 : Ram Installed :
17:39:58 : 3 GB
17:39:58 : Windows Access Right
17:39:58 : Admin
17:39:59 : ******* Dongle Info *******
17:39:59 : Version :
17:39:59 : Hydra Tool v 1.1
17:39:59 : Serial :
17:39:59 : 190400000765
17:40:00 : Initialize :
17:40:00 : OKAY
17:40:00 : Status :
17:40:00 : Activated
17:40:00 : Life :
17:40:00 : 0-
17:40:00 : [3-
17:40:00 : 0-
17:40:00 : 0-
17:40:00 : 0-
17:40:00 : 0]
17:40:00 :
17:40:00 :
17:40:01 : Searching Device By Fastboot
17:40:02 : Device Found...
17:40:02 :
17:40:02 : Reading Information...
17:40:02 : Product :
17:40:02 : product: beryllium
17:40:02 : Serial No. :
17:40:02 : serialno: b4a4f031
17:40:02 : version :
17:40:02 : getvar:version FAILED (remote: GetVar Variable Not found)
17:40:02 : Secure :
17:40:02 : secure: yes
17:40:02 : Device Info:
17:40:02 : Verity mode: true
17:40:02 : Device unlocked: true
17:40:02 : Device critical unlocked: true
17:40:02 : Charger screen enabled: false
17:40:02 :
17:40:02 : Rebooting Fastboot To EDL Mode...
17:40:02 :
17:40:02 : Reboot Successfully.
17:40:15 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:40:15 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:40:15 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:40:15 : Intel(R) HD Graphics 630
17:40:15 : Ram Installed :
17:40:15 : 3 GB
17:40:15 : Windows Access Right
17:40:15 : Admin
17:40:16 : ******* Dongle Info *******
17:40:16 : Version :
17:40:16 : Hydra Tool v 1.1
17:40:16 : Serial :
17:40:16 : 190400000765
17:40:17 : Initialize :
17:40:17 : OKAY
17:40:17 : Status :
17:40:17 : Activated
17:40:17 : Life :
17:40:17 : 0-
17:40:17 : [3-
17:40:17 : 0-
17:40:17 : 0-
17:40:17 : 0-
17:40:17 : 0]
17:40:17 :
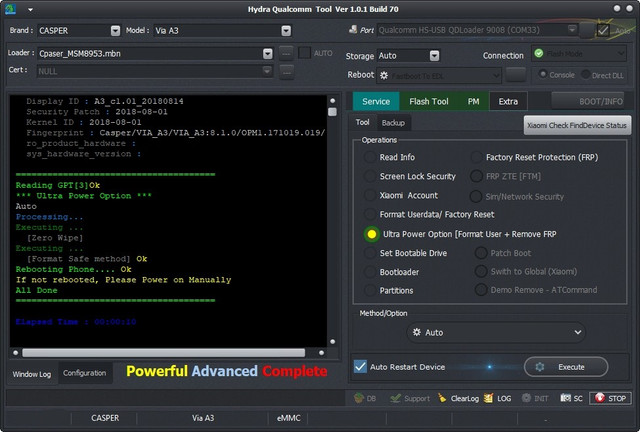
17:40:17 : PreOperation Configuration
17:40:17 : Brand :
17:40:17 : AUTO
17:40:17 : Model :
17:40:17 : AUTO
17:40:17 : Storage :
17:40:17 : Auto
17:40:17 : Loader:
17:40:17 : Auto
17:40:17 : Port :
17:40:17 : Auto
17:40:17 : Connection :
17:40:17 : Flash Mode
17:40:17 :
17:40:17 : Searching EDL Port..
17:40:17 : [COM13]
17:40:17 : TPortConnection.Create...
17:40:17 : (COM13)
17:40:17 : ..Opening...
17:40:17 : Ok
17:40:18 : Getting device info
17:40:18 : .
17:40:18 : .
17:40:18 : .
17:40:19 : .
17:40:19 : .
17:40:20 : .
17:40:20 : .
17:40:20 : Serial No.:
17:40:20 : 0x797E85D8
17:40:20 : MSM ID :
17:40:20 : 0x0008B0E1
17:40:21 : , SDM845-Qualcomm Snapdragon 845
17:40:21 : PBL Ver :
17:40:21 : 00000001
17:40:21 : PK HASH :
17:40:21 : C924A35F39CE1CDD1B8D5A9F3B8E3C51
17:40:21 : 317930431D7A9DD5A55028CF6965FE65
17:40:21 :
17:40:21 : Firehose Loader
17:40:21 : [prog_ufs_firehose_sdm845_ddr_2.elf]
17:40:21 : Initializing SaharaBoot...
17:40:21 : Ok
17:40:21 : Sending
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:21 : .
17:40:26 : Ok
17:40:26 :
17:40:26 : Connecting to Firehose...
17:40:27 : Ping
17:40:27 : .
17:40:27 : .
17:40:27 : .
17:40:27 : .
17:40:27 : .
17:40:27 : NOTE : FILTERED : <
17:40:27 : .
17:40:27 : NOTE : FILTERED : ?
17:40:27 : .
17:40:27 : NOTE : FILTERED : x
17:40:27 : .
17:40:27 : NOTE : FILTERED : m
17:40:27 : .
17:40:27 : NOTE : FILTERED : l
17:40:27 : .
17:40:27 : Ok
17:40:27 : Configuration
17:40:27 : .
17:40:27 : Xiaomi Authentication needed...
17:40:33 : User Cancelled Authentication Process.
17:40:33 : Running :
17:40:33 : Failed
17:40:33 : Device is not in Firehose Mode
17:40:33 :
17:40:33 : Elapsed Time : 00:00:15
17:40:33 :
17:40:33 :
17:40:33 : TPortConnection.Destroy...
17:40:33 : ..Closing...
17:40:33 : Ok..
17:40:40 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:40:40 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:40:40 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:40:40 : Intel(R) HD Graphics 630
17:40:40 : Ram Installed :
17:40:40 : 3 GB
17:40:40 : Windows Access Right
17:40:40 : Admin
17:40:41 : ******* Dongle Info *******
17:40:41 : Version :
17:40:41 : Hydra Tool v 1.1
17:40:41 : Serial :
17:40:41 : 190400000765
17:40:41 : Initialize :
17:40:41 : OKAY
17:40:41 : Status :
17:40:41 : Activated
17:40:41 : Life :
17:40:41 : 0-
17:40:41 : [3-
17:40:41 : 0-
17:40:41 : 0-
17:40:41 : 0-
17:40:41 : 0]
17:40:41 :
17:40:42 : PreOperation Configuration
17:40:42 : Brand :
17:40:42 : AUTO
17:40:42 : Model :
17:40:42 : AUTO
17:40:42 : Storage :
17:40:42 : Auto
17:40:42 : Loader:
17:40:42 : Auto
17:40:42 : Port :
17:40:42 : Auto
17:40:42 : Connection :
17:40:42 : Flash Mode
17:40:42 :
17:40:42 : Searching EDL Port..
17:40:42 : [COM13]
17:40:42 : TPortConnection.Create...
17:40:42 : (COM13)
17:40:42 : ..Opening...
17:40:42 : Ok
17:40:43 : Getting device info
17:40:43 : .
17:40:43 : .
17:40:43 : Device MODE :
17:40:43 : SAHARA
17:40:43 :
17:40:43 : Connecting to Firehose...
17:40:44 : Ping
17:40:44 : .
17:40:44 : .
17:40:44 : .
17:40:44 : .
17:40:44 : .
17:40:44 : NOTE : FILTERED : <
17:40:44 : .
17:40:44 : NOTE : FILTERED : ?
17:40:44 : .
17:40:44 : NOTE : FILTERED : x
17:40:44 : .
17:40:44 : NOTE : FILTERED : m
17:40:44 : .
17:40:44 : NOTE : FILTERED : l
17:40:44 : .
17:40:44 : Ok
17:40:44 : Configuration
17:40:44 : .
17:40:44 : Xiaomi Authentication needed...
17:40:46 : Signature Request ->
17:40:46 : .
17:40:46 : blob[AQAAAEEBAADYhX55_fCpkG6MNylo91gD_7TZPg]
17:40:46 : Checking Internet connection....
17:40:46 :
17:40:47 : - Hydra Is Online
17:40:47 : Connecting to Hydra Xiaomi Server...
17:40:48 : - ERROR : XIAOMI SERVER IS CURRENTLY OFFLINE
17:40:48 :
17:40:48 : - Unable to generate authkey...
17:40:48 : Running :
17:40:48 : Failed
17:40:48 : Device is not in Firehose Mode
17:40:48 :
17:40:48 : Elapsed Time : 00:00:05
17:40:48 :
17:40:48 :
17:40:48 : TPortConnection.Destroy...
17:40:48 : ..Closing...
17:40:48 : Ok..
17:42:02 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:42:02 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:42:02 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:42:02 : Intel(R) HD Graphics 630
17:42:02 : Ram Installed :
17:42:02 : 3 GB
17:42:02 : Windows Access Right
17:42:02 : Admin
17:42:03 : ******* Dongle Info *******
17:42:03 : Version :
17:42:03 : Hydra Tool v 1.1
17:42:03 : Serial :
17:42:03 : 190400000765
17:42:04 : Initialize :
17:42:04 : OKAY
17:42:04 : Status :
17:42:04 : Activated
17:42:04 : Life :
17:42:04 : 0-
17:42:04 : [3-
17:42:04 : 0-
17:42:04 : 0-
17:42:04 : 0-
17:42:04 : 0]
17:42:04 :
17:42:04 : PreOperation Configuration
17:42:04 : Brand :
17:42:04 : XIAOMI
17:42:04 : Model :
17:42:04 : PocoPhone F1 (beryllium)
17:42:04 : Storage :
17:42:04 : Auto
17:42:04 : Loader:
17:42:04 : prog_ufs_firehose_sdm845_ddr.elf
17:42:04 : Port :
17:42:04 : Auto
17:42:04 : Connection :
17:42:04 : Flash Mode
17:42:04 :
17:42:04 : Searching EDL Port..
17:42:04 : [COM13]
17:42:04 : TPortConnection.Create...
17:42:04 : (COM13)
17:42:04 : ..Opening...
17:42:05 : Ok
17:42:05 : Getting device info
17:42:05 : .
17:42:05 : .
17:42:05 : Device MODE :
17:42:05 : SAHARA
17:42:05 :
17:42:05 : Connecting to Firehose...
17:42:06 : Ping
17:42:06 : .
17:42:06 : .
17:42:06 : .
17:42:06 : .
17:42:06 : .
17:42:06 : NOTE : FILTERED : <
17:42:06 : .
17:42:06 : NOTE : FILTERED : ?
17:42:06 : .
17:42:06 : NOTE : FILTERED : x
17:42:06 : .
17:42:06 : NOTE : FILTERED : m
17:42:06 : .
17:42:06 : NOTE : FILTERED : l
17:42:06 : .
17:42:06 : Ok
17:42:06 : Configuration
17:42:06 : .
17:42:06 : Xiaomi Authentication needed...
17:42:08 : User Cancelled Authentication Process.
17:42:08 : Running :
17:42:08 : Failed
17:42:08 : Device is not in Firehose Mode
17:42:08 :
17:42:08 : Elapsed Time : 00:00:03
17:42:08 :
17:42:08 :
17:42:08 : TPortConnection.Destroy...
17:42:08 : ..Closing...
17:42:08 : Ok..
17:42:30 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:42:30 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:42:30 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:42:30 : Intel(R) HD Graphics 630
17:42:30 : Ram Installed :
17:42:30 : 3 GB
17:42:30 : Windows Access Right
17:42:30 : Admin
17:42:31 : ******* Dongle Info *******
17:42:31 : Version :
17:42:31 : Hydra Tool v 1.1
17:42:31 : Serial :
17:42:31 : 190400000765
17:42:32 : Initialize :
17:42:32 : OKAY
17:42:32 : Status :
17:42:32 : Activated
17:42:32 : Life :
17:42:32 : 0-
17:42:32 : [3-
17:42:32 : 0-
17:42:32 : 0-
17:42:32 : 0-
17:42:32 : 0]
17:42:32 :
17:42:32 :
17:42:32 : Searching EDL Port..
17:42:32 : [COM13]
17:42:32 : TPortConnection.Create...
17:42:32 : (COM13)
17:42:32 : ..Opening...
17:42:32 : Ok
17:42:33 : Getting device info
17:42:33 : .
17:42:33 : .
17:42:33 : Device MODE :
17:42:33 : SAHARA
17:42:33 :
17:42:33 : Connecting to Firehose...
17:42:34 : Ping
17:42:34 : .
17:42:34 : .
17:42:34 : .
17:42:34 : .
17:42:34 : .
17:42:34 : NOTE : FILTERED : <
17:42:34 : .
17:42:34 : NOTE : FILTERED : ?
17:42:34 : .
17:42:34 : NOTE : FILTERED : x
17:42:34 : .
17:42:34 : NOTE : FILTERED : m
17:42:34 : .
17:42:34 : NOTE : FILTERED : l
17:42:34 : .
17:42:34 : Ok
17:42:34 : Rebooting Phone....
17:42:34 : Ok
17:42:34 : Ok
17:42:34 :
17:42:34 : TPortConnection.Destroy...
17:42:34 : ..Closing...
17:42:34 : Ok..
17:43:24 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
17:43:24 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
17:43:24 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
17:43:24 : Intel(R) HD Graphics 630
17:43:24 : Ram Installed :
17:43:24 : 3 GB
17:43:24 : Windows Access Right
17:43:24 : Admin
17:43:25 : ******* Dongle Info *******
17:43:25 : Version :
17:43:25 : Hydra Tool v 1.1
17:43:25 : Serial :
17:43:25 : 190400000765
17:43:26 : Initialize :
17:43:26 : OKAY
17:43:26 : Status :
17:43:26 : Activated
17:43:26 : Life :
17:43:26 : 0-
17:43:26 : [3-
17:43:26 : 0-
17:43:26 : 0-
17:43:26 : 0-
17:43:26 : 0]
17:43:26 :
17:43:26 : Searching Device By Fastboot
17:43:27 : Device Found...
17:43:27 :
17:43:27 : Reading Information...
17:43:27 : Product :
17:43:27 : product: beryllium
17:43:27 : Serial No. :
17:43:27 : serialno: b4a4f031
17:43:27 : version :
17:43:27 : getvar:version FAILED (remote: GetVar Variable Not found)
17:43:27 : Secure :
17:43:27 : secure: yes
17:43:27 : Device Info:
17:43:27 : Verity mode: true
17:43:27 : Device unlocked: true
17:43:27 : Device critical unlocked: true
17:43:27 : Charger screen enabled: false
17:43:27 :
17:43:27 : Elapsed Time : 00:00:01
17:43:27 :
18:28:10 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
18:28:10 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
18:28:10 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
18:28:10 : Intel(R) HD Graphics 630
18:28:10 : Ram Installed :
18:28:10 : 3 GB
18:28:10 : Windows Access Right
18:28:10 : Admin
18:28:10 :
18:28:10 :
18:28:11 : ******* Dongle Info *******
18:28:11 : Version :
18:28:11 : Hydra Tool v 1.1
18:28:11 : Serial :
18:28:11 : 190400000765
18:28:11 : Initialize :
18:28:11 : OKAY
18:28:11 : Status :
18:28:11 : Activated
18:28:11 : Life :
18:28:11 : 0-
18:28:11 : [3-
18:28:11 : 0-
18:28:11 : 0-
18:28:11 : 0-
18:28:11 : 0]
18:28:11 :
18:28:47 :
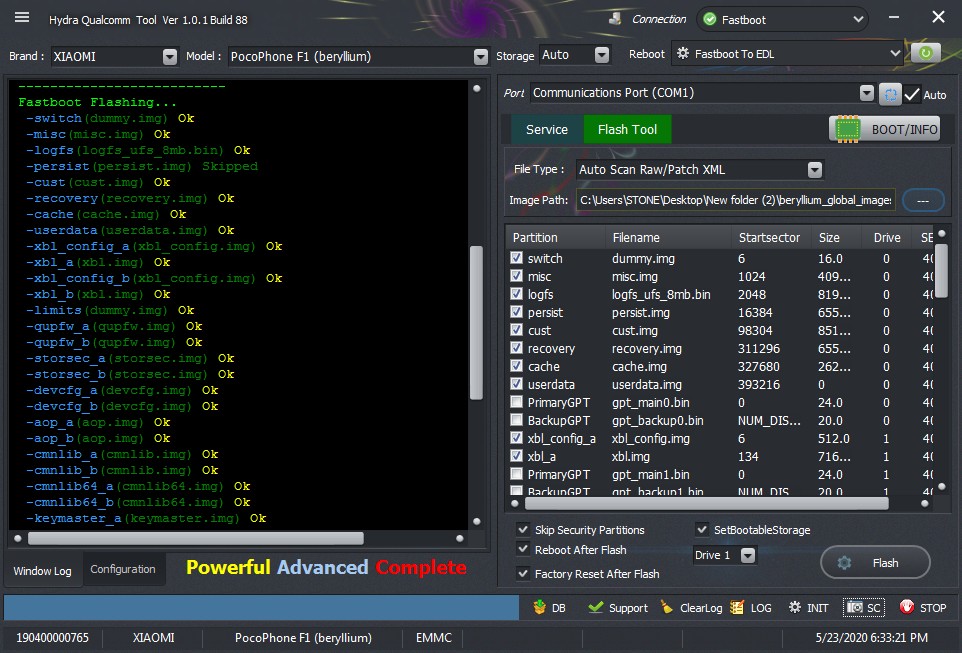
18:28:47 : Image Path : C:\Users\STONE\Desktop\New folder (2)\beryllium_global_images_V11.0.6.0.QEJMIXM_20200227.0000.00_10.0_global
18:28:47 : Scanning rawprogram xml
18:28:53 :
18:28:53 : Image Path : C:\Users\STONE\Desktop\New folder (2)\beryllium_global_images_V11.0.6.0.QEJMIXM_20200227.0000.00_10.0_global\images
18:28:53 : Scanning rawprogram xml
18:28:54 : * rawprogram0.xml
18:28:54 : * rawprogram1.xml
18:28:54 : * rawprogram2.xml
18:28:54 : * rawprogram3.xml
18:28:54 : * rawprogram4.xml
18:28:54 : * rawprogram5.xml
18:28:54 : 6 RawXML Detected and Loaded 102 Items
18:28:54 : C:\Users\STONE\Desktop\New folder (2)\beryllium_global_images_V11.0.6.0.QEJMIXM_20200227.0000.00_10.0_global\images\C:\Users\STONE\Desktop\New folder (2)\beryllium_global_images_V11.0.6.0.QEJMIXM_20200227.0000.00_10.0_global\images\System.img
18:28:56 :
18:28:56 : Reading System Image Info ..........
18:28:56 : Model :
18:28:56 : Brand :
18:28:56 : Android Ver : 10
18:28:56 : Miui Ver : V11
18:28:56 : Manufacturer : Xiaomi
18:28:56 : Device :
18:28:56 : Mod_device : beryllium_global
18:28:56 : Display ID :
18:28:56 : Security Patch : 2020-02-01
18:28:56 : Kernel ID : 2020-02-01
18:28:56 :
18:28:56 : ****** CHECK IF MATCH WITH YOUR PHONE *********
18:28:56 :
18:28:56 : * patch0.xml
18:28:56 : * patch1.xml
18:28:56 : * patch2.xml
18:28:56 : * patch3.xml
18:28:56 : * patch4.xml
18:28:56 : * patch5.xml
18:28:56 : 6 PatchXML Detected and Loaded 156 Items
18:29:07 : Hydra Qualcomm Tool Ver 1.0.1 Build 88
18:29:07 : Windows 7 Service Pack 1 (Version 6.1, Build 7601, 32-bit Edition)
18:29:07 : Intel(R) Core(TM) i3-7100 CPU @ 3.90GHz
18:29:07 : Intel(R) HD Graphics 630
18:29:07 : Ram Installed :
18:29:07 : 3 GB
18:29:07 : Windows Access Right
18:29:07 : Admin
18:29:08 : ******* Dongle Info *******
18:29:08 : Version :
18:29:08 : Hydra Tool v 1.1
18:29:08 : Serial :
18:29:08 : 190400000765
18:29:09 : Initialize :
18:29:09 : OKAY
18:29:09 : Status :
18:29:09 : Activated
18:29:09 : Life :
18:29:09 : 0-
18:29:09 : [3-
18:29:09 : 0-
18:29:09 : 0-
18:29:09 : 0-
18:29:09 : 0]
18:29:09 :
18:29:10 : Searching Device By Fastboot
18:29:10 : Device Found...
18:29:10 :
18:29:10 : Reading Information...
18:29:10 : Product :
18:29:10 : product: beryllium
18:29:10 : Serial No. :
18:29:10 : serialno: b4a4f031
18:29:10 : version :
18:29:10 : getvar:version FAILED (remote: GetVar Variable Not found)
18:29:10 : Secure :
18:29:10 : secure: yes
18:29:10 : Device Info:
18:29:10 : Verity mode: true
18:29:10 : Device unlocked: true
18:29:10 : Device critical unlocked: true
18:29:10 : Charger screen enabled: false
18:29:10 : --------------------------
18:29:10 : Fastboot Flashing...
18:29:10 : -switch
18:29:10 : (dummy.img)
18:29:10 : Ok
18:29:10 : -misc
18:29:10 : (misc.img)
18:29:10 : Ok
18:29:10 : -logfs
18:29:10 : (logfs_ufs_8mb.bin)
18:29:10 : Ok
18:29:10 : -persist
18:29:10 : (persist.img)
18:29:10 : Skipped
18:29:10 : -cust
18:29:10 : (cust.img)
18:29:20 : Ok
18:29:20 : -recovery
18:29:20 : (recovery.img)
18:29:22 : Ok
18:29:22 : -cache
18:29:22 : (cache.img)
18:29:23 : Ok
18:29:23 : -userdata
18:29:23 : (userdata.img)
18:29:25 : Ok
18:29:25 : -xbl_config_a
18:29:25 : (xbl_config.img)
18:29:26 : Ok
18:29:26 : -xbl_a
18:29:26 : (xbl.img)
18:29:26 : Ok
18:29:26 : -xbl_config_b
18:29:26 : (xbl_config.img)
18:29:26 : Ok
18:29:26 : -xbl_b
18:29:26 : (xbl.img)
18:29:26 : Ok
18:29:26 : -limits
18:29:26 : (dummy.img)
18:29:26 : Ok
18:29:26 : -qupfw_a
18:29:26 : (qupfw.img)
18:29:26 : Ok
18:29:26 : -qupfw_b
18:29:26 : (qupfw.img)
18:29:26 : Ok
18:29:26 : -storsec_a
18:29:26 : (storsec.img)
18:29:26 : Ok
18:29:26 : -storsec_b
18:29:26 : (storsec.img)
18:29:26 : Ok
18:29:26 : -devcfg_a
18:29:26 : (devcfg.img)
18:29:26 : Ok
18:29:26 : -devcfg_b
18:29:26 : (devcfg.img)
18:29:27 : Ok
18:29:27 : -aop_a
18:29:27 : (aop.img)
18:29:27 : Ok
18:29:27 : -aop_b
18:29:27 : (aop.img)
18:29:27 : Ok
18:29:27 : -cmnlib_a
18:29:27 : (cmnlib.img)
18:29:27 : Ok
18:29:27 : -cmnlib_b
18:29:27 : (cmnlib.img)
18:29:27 : Ok
18:29:27 : -cmnlib64_a
18:29:27 : (cmnlib64.img)
18:29:27 : Ok
18:29:27 : -cmnlib64_b
18:29:27 : (cmnlib64.img)
18:29:27 : Ok
18:29:27 : -keymaster_a
18:29:27 : (keymaster.img)
18:29:27 : Ok
18:29:27 : -keymaster_b
18:29:27 : (keymaster.img)
18:29:27 : Ok
18:29:27 : -bluetooth
18:29:27 : (bluetooth.img)
18:29:27 : Ok
18:29:27 : -hyp_a
18:29:27 : (hyp.img)
18:29:27 : Ok
18:29:27 : -hyp_b
18:29:27 : (hyp.img)
18:29:27 : Ok
18:29:27 : -abl_a
18:29:27 : (abl.img)
18:29:27 : Ok
18:29:27 : -abl_b
18:29:27 : (abl.img)
18:29:27 : Ok
18:29:27 : -tz_a
18:29:27 : (tz.img)
18:29:28 : Ok
18:29:28 : -tz_b
18:29:28 : (tz.img)
18:29:28 : Ok
18:29:28 : -logo
18:29:28 : (logo.img)
18:29:29 : Ok
18:29:29 : -dsp
18:29:29 : (dsp.img)
18:29:30 : Ok
18:29:30 : -boot
18:29:30 : (boot.img)
18:29:31 : Ok
18:29:31 : -modem
18:29:31 : (modem.img)
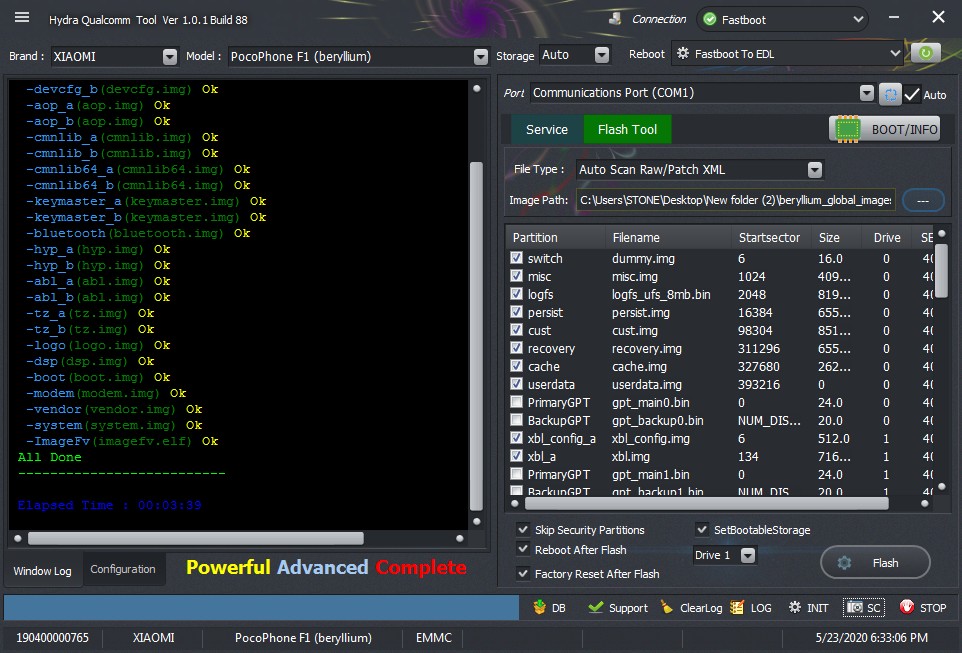
18:29:37 : Ok
18:29:37 : -vendor
18:29:37 : (vendor.img)
18:30:08 : Ok
18:30:08 : -system
18:30:08 : (system.img)
18:32:43 : Ok
18:32:43 : -ImageFv
18:32:43 : (imagefv.elf)
18:32:47 : Ok
18:32:47 : All Done
18:32:47 : --------------------------
18:32:48 :
18:32:48 : Elapsed Time : 00:03:39
18:32:48 :