Franky38
Moderator
Xiaomi MI 8 SE Flashing Success by Hydra Tool
Device need bootloader unlocked and Fastboot status
Device need bootloader unlocked and Fastboot status
Code:
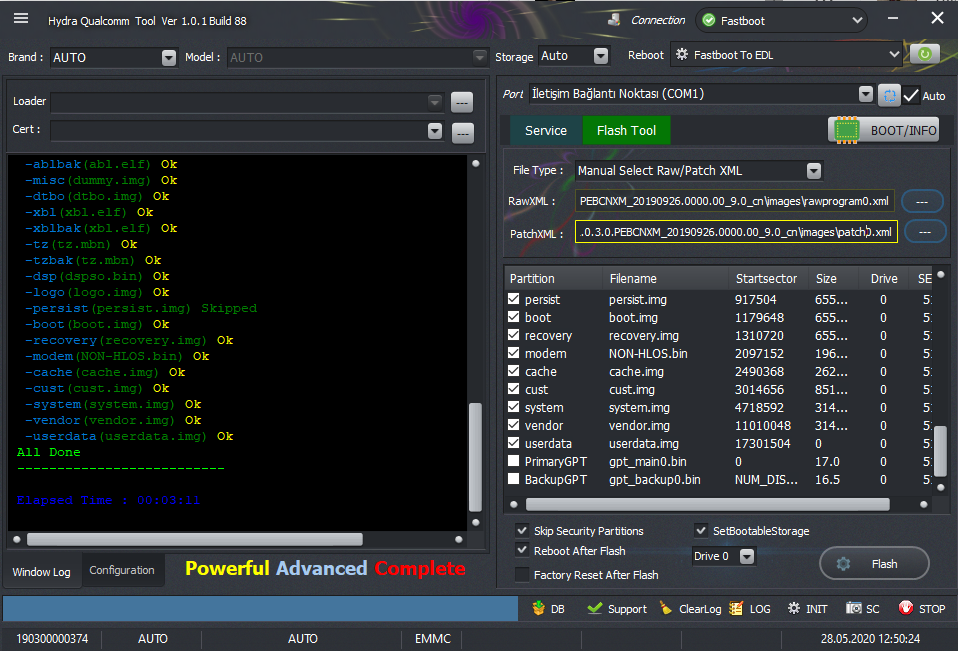
Searching Device By Fastboot
Device Found...
Reading Information...
Product : product: sirius
Serial No. : serialno: d4166a99
version : getvar:version FAILED (remote: GetVar Variable Not found)
Secure : secure: yes
Device Info:
Verity mode: true
Device unlocked: true
Device critical unlocked: true
Charger screen enabled: true
--------------------------
Fastboot Flashing...
-switch(dummy.img) Ok
-vbmeta(vbmeta.img) Ok
-qupfw(qupv3fw.elf) Ok
-xbl_config(xbl_config.elf) Ok
-storsec(storsec.mbn) Ok
-storsecbak(storsec.mbn) Ok
-aop(aop.mbn) Ok
-hyp(hyp.mbn) Ok
-hypbak(hyp.mbn) Ok
-cmnlib(cmnlib.mbn) Ok
-cmnlibbak(cmnlib.mbn) Ok
-cmnlib64(cmnlib64.mbn) Ok
-cmnlib64bak(cmnlib64.mbn) Ok
-keymaster(keymaster64.mbn) Ok
-keymasterbak(keymaster64.mbn) Ok
-bluetooth(BTFM.bin) Ok
-devcfg(devcfg.mbn) Ok
-devcfgbak(devcfg.mbn) Ok
-abl(abl.elf) Ok
-ablbak(abl.elf) Ok
-misc(dummy.img) Ok
-dtbo(dtbo.img) Ok
-xbl(xbl.elf) Ok
-xblbak(xbl.elf) Ok
-tz(tz.mbn) Ok
-tzbak(tz.mbn) Ok
-dsp(dspso.bin) Ok
-logo(logo.img) Ok
-persist(persist.img) Skipped
-boot(boot.img) Ok
-recovery(recovery.img) Ok
-modem(NON-HLOS.bin) Ok
-cache(cache.img) Ok
-cust(cust.img) Ok
-system(system.img) Ok
-vendor(vendor.img) Ok
-userdata(userdata.img) Ok
All Done
--------------------------
Elapsed Time : 00:03:11