Redmi Note 8T willow FRP Remove Success by Hydra Tool
Xiaomi Redmi note 8t willow Reset FRP without credits, with hydra tool standalone server by hydra dongle
Xiaomi Redmi note 8t willow Reset FRP without credits, with hydra tool standalone server by hydra dongle
PreOperation Configuration
Brand : XIAOMI Model : Redmi Note 8T (wiilow) Storage : Auto
Loader: Xiaomi_redmi8t_loader.elf
Port : Auto
Connection : Flash Mode
Searching EDL Port..[COM52]
TPortConnection.Create...(COM52)..Opening...Ok
Getting device info.......
Serial No.: 0xECF29658
MSM ID : 0x0010A0E1,
PBL Ver : 00000001
PK HASH : 1BEBE3863A6781DB4B01086063007334
DE9E5CA14971C7C4F4358EC9D79CDA46
Firehose Loader[Xiaomi_redminote8_loader.elf]
Initializing SaharaBoot... Ok
Sending ..............................Ok
Connecting to Firehose...
Ping.....
NOTE : FILTERED : <.
NOTE : FILTERED : ?.
NOTE : FILTERED : x.
NOTE : FILTERED : m.
NOTE : FILTERED : l. Ok
Configuration........
Identifying Chip....Ok
Chip Configuration :
MemoryName : eMMC
MaxPayloadSizeToTargetInBytes : 16384
MaxPayloadSizeToTargetInBytesSupported : 16384
MaxPayloadSizeFromTargetInBytes :
MaxXMLSizeInBytes : 4096
TargetName :
Version : 1
DateTime : Jul 3 2019 - 22:23:56
* STORAGE DEVICE INFO *
Memory Type : eMMC
Block Size in Bytes : 512
Page Size : 512
Manufacturer ID : 19
Serial Number : 337546819
Firmware Version : 4
Product Name : S0J9K8
Physical Partitions : 4
Total Logical Blocks:
Drive [0] 122142720[58,242 GB]
Drive [1] 8192[4 MB]
Drive [2] 8192[4 MB]
Drive [3] 32768[16 MB]
Running : Ok
Reading GPT[4]Ok
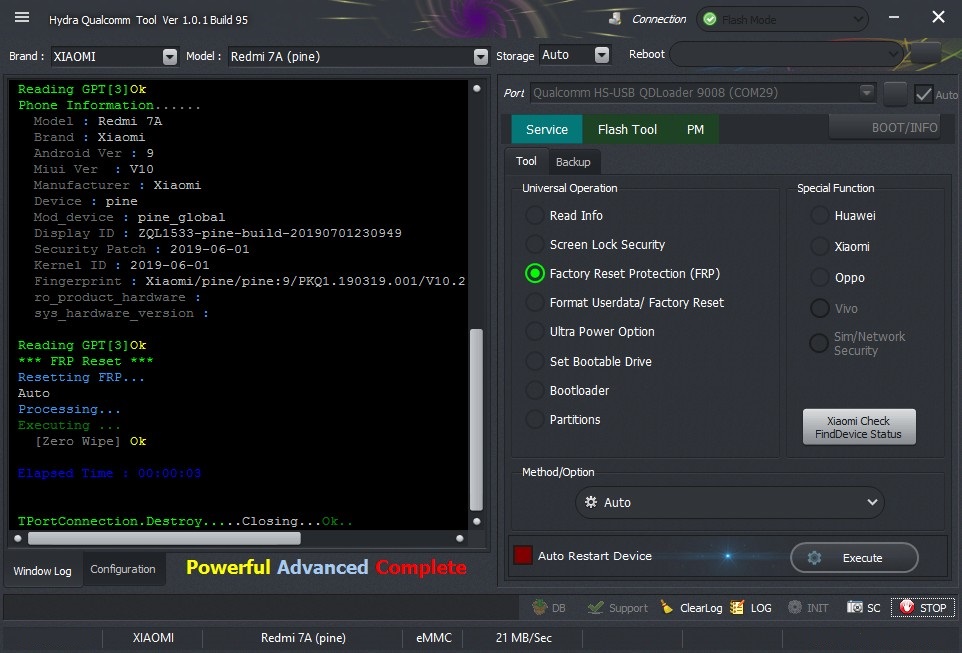
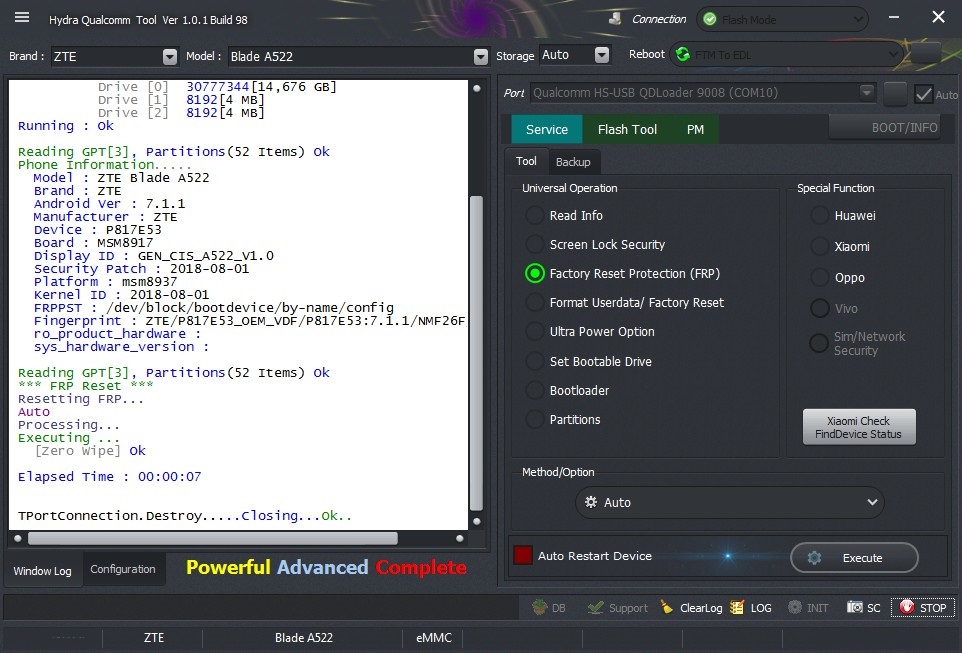
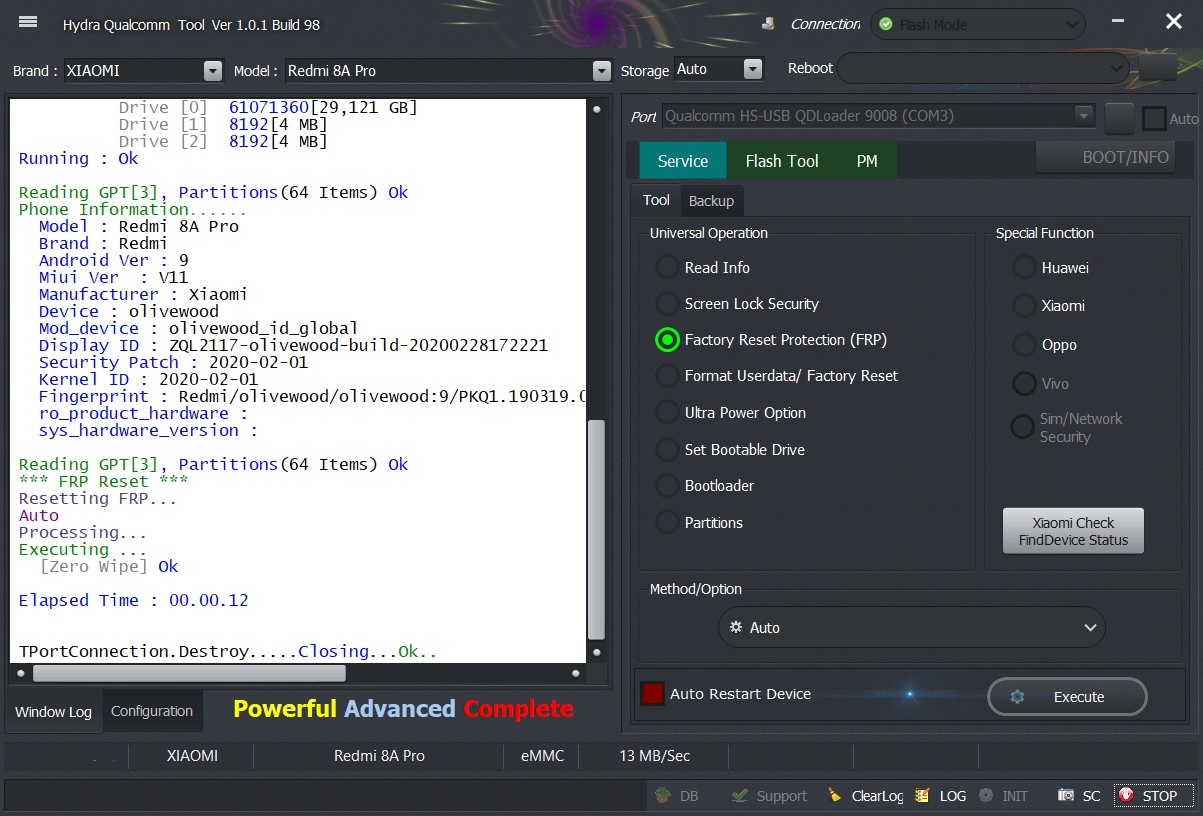
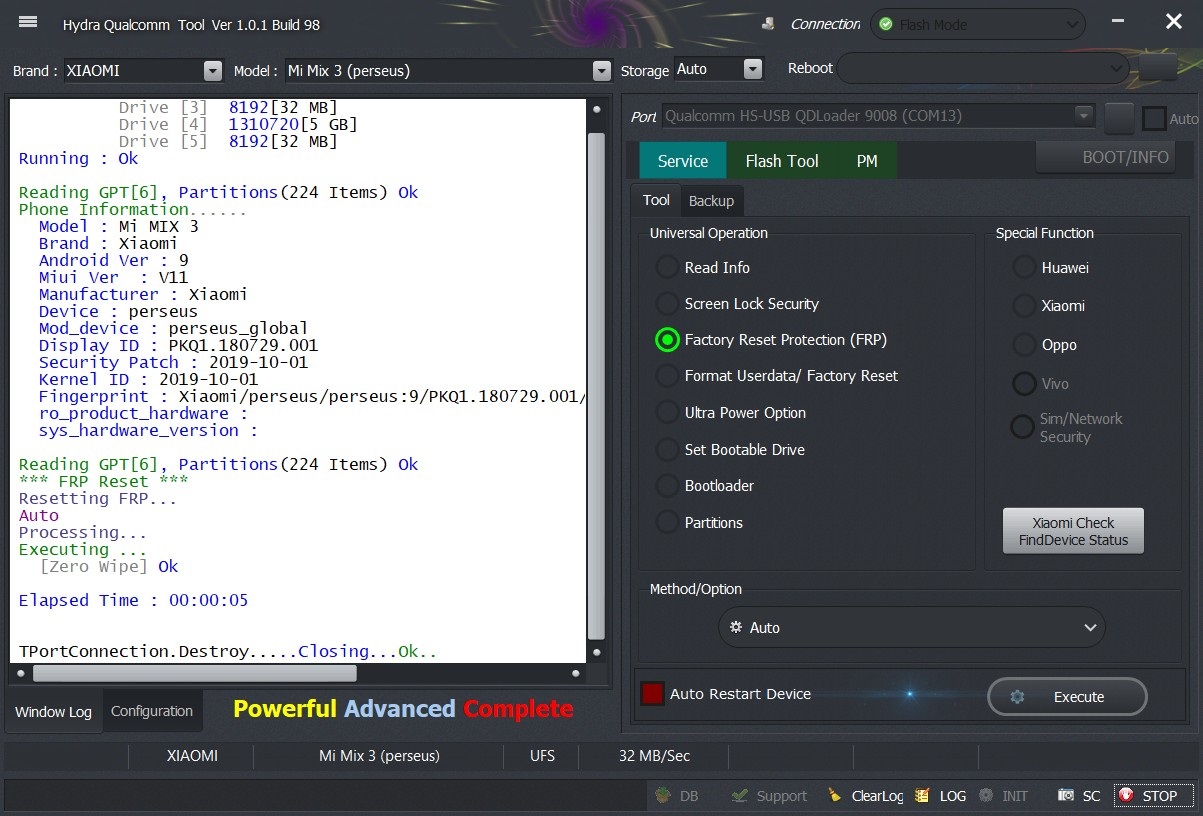
Phone Information......
Model : Redmi Note 8T
Brand : xiaomi
Android Ver : 9
Miui Ver : V11
Manufacturer : Xiaomi
Device : willow
Mod_device : willow_global
Display ID : PKQ1.190616.001
Security Patch : 2020-01-01
Kernel ID : 2020-01-01
Fingerprint : xiaomi/willow/willow:9/PKQ1.190616.001/V11.0.2.0.PCXMIXM:user/release-keys
ro_product_hardware :
sys_hardware_version :
Reading GPT[4]Ok
* FRP Reset *
Resetting FRP...
Auto
Processing...
Executing ...
[Zero Wipe] Ok
Elapsed Time : 00:00:09
TPortConnection.Destroy.....Closing...Ok..